
用户凭证管理:
- pin_auth(口令认证):模块支持用户口令的设置,删除和认证功能。与用户IAM子系统基础框架配合,也可以支持用户口令修改的功能;口令认证作为OpenHarmony最基础的用户身份认证执行器,按照协同认证定义的资源注册接口,将口令认证相关资源信息注册到协同认证框架,并根据协同认证框架的调度,完成口令的设置,删除和认证功能;
- face_auth(人脸认证):支持用户人脸的录入,删除和认证功能;人脸认证是OpenHarmony支持的一种生物认证执行器,按照协同认证定义的资源注册接口,将人脸认证相关资源信息注册到协同认证框架,并根据协同认证框架的调度,调用人脸认证HDI,完成人脸的录入,认证,删除等功能。
- user_auth_framework:主要包括三个模块,用户认证、凭据管理和执行器管理:
- 用户认证模块对外提供统一用户身份认证功能,并且开放生物特征认证API给三方应用调用。
- 凭据管理模块提供系统内统一的用户凭据管理(增删改查)接口,向下通过执行器管理模块,调用系统内的执行器资源,完成用户凭据的生命周期管理和安全存储。
- 执行器管理模块提供系统内执行器资源的统一管理和协同调度能力,当前支持口令执行器和人脸执行器的管理。
使用:
接口
import osAccount from '@ohos.account.osAccount'
凭证管理
//UserIdentityManager
/**
* Provides the abilities for managing user identity.
* @name UserIdentityManager
* @syscap SystemCapability.Account.OsAccount
* @since 8
*/
class UserIdentityManager {
/**
* Constructor to get the UserIdentityManager class instance.
* @returns Returns the UserIdentityManager class instance.
* @systemapi Hide this for inner system use.
* @since 8
*/
constructor();
/**
* Opens session.
* <p>
* Start an IDM operation to obtain challenge value.
* A challenge value of 0 indicates that opensession failed.
* @permission ohos.permission.MANAGE_USER_IDM
* @returns Returns a challenge value.
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @systemapi Hide this for inner system use.
* @since 8
*/
openSession(callback: AsyncCallback<Uint8Array>): void;
openSession(): Promise<Uint8Array>;
/**
* Adds credential.
* <p>
* Add user credential information, pass in credential addition method and credential information
* (credential type, subclass, if adding user's non password credentials, pass in password authentication token),
* and get the result / acquireinfo callback.
* @permission ohos.permission.MANAGE_USER_IDM
* @param credentialInfo Indicates the credential information.
* @param callback Indicates the callback to get results and acquireInfo.
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @throws {BusinessError} 12300002 - invalid credentialInfo.
* @systemapi Hide this for inner system use.
* @since 8
*/
addCredential(credentialInfo: CredentialInfo, callback: IIdmCallback): void;
/**
* Updates credential.
* @permission ohos.permission.MANAGE_USER_IDM
* @param credentialInfo Indicates the credential information.
* @param callback Indicates the callback to get results and acquireInfo.
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @throws {BusinessError} 12300002 - invalid credentialInfo.
* @systemapi Hide this for inner system use.
* @since 8
*/
updateCredential(credentialInfo: CredentialInfo, callback: IIdmCallback): void;
/**
* Closes session.
* <p>
* End an IDM operation.
* @permission ohos.permission.MANAGE_USER_IDM
* @systemapi Hide this for inner system use.
* @since 8
*/
closeSession(): void;
/**
* Cancels entry with a challenge value.
* @permission ohos.permission.MANAGE_USER_IDM
* @param challenge Indicates the challenge value.
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @throws {BusinessError} 12300002 - invalid challenge.
* @systemapi Hide this for inner system use.
* @since 8
*/
cancel(challenge: Uint8Array): void;
/**
* Deletes the user with the authentication token.
* @permission ohos.permission.MANAGE_USER_IDM
* @param token Indicates the authentication token.
* @param callback Indicates the callback to get the deletion result.
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @throws {BusinessError} 12300002 - invalid token.
* @systemapi Hide this for inner system use.
* @since 8
*/
delUser(token: Uint8Array, callback: IIdmCallback): void;
/**
* Deletes the user credential information.
* @permission ohos.permission.MANAGE_USER_IDM
* @param credentialId Indicates the credential index.
* @param token Indicates the authentication token.
* @param callback Indicates the callback to get the deletion result.
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @throws {BusinessError} 12300002 - invalid credentialId or token.
* @systemapi Hide this for inner system use.
* @since 8
*/
delCred(credentialId: Uint8Array, token: Uint8Array, callback: IIdmCallback): void;
/**
* Gets authentication information.
* @permission ohos.permission.USE_USER_IDM
* @param authType Indicates the authentication type.
* @param callback Indicates the callback to get all registered credential information of
* the specified type for the current user.
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @throws {BusinessError} 12300002 - invalid authType.
* @throws {BusinessError} 12300015 - the authType is not supported on current device.
* @throws {BusinessError} 12300016 - authentication timeout.
* @throws {BusinessError} 12300017 - authentication service is busy.
* @throws {BusinessError} 12300018 - authentication service is locked.
* @throws {BusinessError} 12300019 - the credential does not exist.
* @systemapi Hide this for inner system use.
* @since 8
*/
getAuthInfo(callback: AsyncCallback<Array<EnrolledCredInfo>>): void;
getAuthInfo(authType: AuthType, callback: AsyncCallback<Array<EnrolledCredInfo>>): void;
getAuthInfo(authType?: AuthType): Promise<Array<EnrolledCredInfo>>;
}
用户管理
/**
* Provides the abilities for user authentication.
* @name UserAuth
* @syscap SystemCapability.Account.OsAccount
* @since 8
*/
class UserAuth {
/**
* Constructor to get the UserAuth class instance.
* @returns Returns the UserAuth class instance.
* @systemapi Hide this for inner system use.
* @since 8
*/
constructor();
/**
* Gets version information.
* @returns Returns the version information.
* @systemapi Hide this for inner system use.
* @since 8
*/
getVersion(): number;
/**
* Checks whether the authentication capability is available.
* @permission ohos.permission.ACCESS_USER_AUTH_INTERNAL
* @param authType Indicates the credential type for authentication.
* @param authTrustLevel Indicates the trust level of authentication result.
* @returns Returns a status result.
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @throws {BusinessError} 12300002 - invalid authType or authTrustLevel.
* @throws {BusinessError} 12300014 - the authTrustLevel is not supported on current device
* @throws {BusinessError} 12300015 - the authType is not supported on current device.
* @systemapi Hide this for inner system use.
* @since 8
*/
getAvailableStatus(authType: AuthType, authTrustLevel: AuthTrustLevel): number;
/**
* Gets the property based on the specified request information.
* @permission ohos.permission.ACCESS_USER_AUTH_INTERNAL
* @param request Indicates the request information, including authentication type, and property type list.
* @returns Returns an executor property.
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @throws {BusinessError} 12300002 - invalid request.
* @systemapi Hide this for inner system use.
* @since 8
*/
getProperty(request: GetPropertyRequest, callback: AsyncCallback<ExecutorProperty>): void;
getProperty(request: GetPropertyRequest): Promise<ExecutorProperty>;
/**
* Sets property that can be used to initialize algorithms.
* @permission ohos.permission.ACCESS_USER_AUTH_INTERNAL
* @param request Indicates the request information, including authentication type and the key-value to be set.
* @returns Returns a number value indicating whether the property setting was successful.
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @throws {BusinessError} 12300002 - invalid request.
* @systemapi Hide this for inner system use.
* @since 8
*/
setProperty(request: SetPropertyRequest, callback: AsyncCallback<number>): void;
setProperty(request: SetPropertyRequest): Promise<number>;
/**
* Executes authentication.
* @permission ohos.permission.ACCESS_USER_AUTH_INTERNAL
* @param challenge Indicates the challenge value.
* @param authType Indicates the authentication type.
* @param authTrustLevel Indicates the trust level of authentication result.
* @param callback Indicates the callback to get result and acquireInfo.
* @returns Returns a context ID for cancellation.
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @throws {BusinessError} 12300002 - invalid challenge, authType or authTrustLevel.
* @throws {BusinessError} 12300014 - the authTrustLevel is not supported on current device
* @throws {BusinessError} 12300015 - the authType is not supported on current device.
* @throws {BusinessError} 12300016 - authentication timeout.
* @throws {BusinessError} 12300017 - authentication service is busy.
* @throws {BusinessError} 12300018 - authentication service is locked.
* @throws {BusinessError} 12300019 - the credential does not exist.
* @systemapi Hide this for inner system use.
* @since 8
*/
auth(challenge: Uint8Array, authType: AuthType, authTrustLevel: AuthTrustLevel, callback: IUserAuthCallback): Uint8Array;
/**
* Executes user authentication.
* @permission ohos.permission.ACCESS_USER_AUTH_INTERNAL
* @param userId Indicates the user identification.
* @param challenge Indicates the challenge value.
* @param authType Indicates the authentication type.
* @param authTrustLevel Indicates the trust level of authentication result.
* @param callback Indicates the callback to get result and acquireInfo.
* @returns Returns a context ID for cancellation.
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @throws {BusinessError} 12300002 - invalid userId, challenge, authType or authTrustLevel.
* @throws {BusinessError} 12300003 - the account indicated by userId dose not exist.
* @throws {BusinessError} 12300014 - the authTrustLevel is not supported on current device
* @throws {BusinessError} 12300015 - the authType is not supported on current device.
* @throws {BusinessError} 12300016 - authentication timeout.
* @throws {BusinessError} 12300017 - authentication service is busy.
* @throws {BusinessError} 12300018 - authentication service is locked.
* @throws {BusinessError} 12300019 - the credential does not exist.
* @systemapi Hide this for inner system use.
* @since 8
*/
authUser(userId: number, challenge: Uint8Array, authType: AuthType, authTrustLevel: AuthTrustLevel, callback: IUserAuthCallback): Uint8Array;
/**
* Cancels authentication with context ID.
* @permission ohos.permission.ACCESS_USER_AUTH_INTERNAL
* @param contextID Indicates the authentication context ID.
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @throws {BusinessError} 12300002 - invalid contexId.
* @systemapi Hide this for inner system use.
* @since 8
*/
cancelAuth(contextID: Uint8Array): void;
}
口令管理
/**
* Provides the abilities for Pin code authentication.
* @name PINAuth
* @syscap SystemCapability.Account.OsAccount
* @since 8
*/
class PINAuth {
/**
* Constructor to get the PINAuth class instance.
* @returns Returns the PINAuth class instance.
* @systemapi Hide this for inner system use.
* @since 8
*/
constructor();
/**
* Register inputer.
* @permission ohos.permission.ACCESS_PIN_AUTH
* @param inputer Indicates the password input box callback
* @throws {BusinessError} 201 - permission denied.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300001 - system service exception.
* @throws {BusinessError} 12300007 - PIN inputer has been registered.
* @systemapi Hide this for inner system use.
* @since 8
*/
registerInputer(inputer: IInputer): void;
/**
* Unregister inputer.
* @permission ohos.permission.ACCESS_PIN_AUTH
* @systemapi Hide this for inner system use.
* @since 8
*/
unregisterInputer(): void;
}
回调:IInputData,Inputer回调时带的参数,用来输入口令。
/**
* Password data callback.
*
* @name IInputData
* @syscap SystemCapability.Account.OsAccount
* @systemapi Hide this for inner system use.
* @since 8
*/
interface IInputData {
/**
* Notifies to set data.
* @param pinSubType Indicates the credential subtype for authentication.
* @param data Indicates the data to set.
* @throws {BusinessError} 401 - the parameter check failed.
* @throws {BusinessError} 12300002 - invalid pinSubType.
* @systemapi Hide this for inner system use.
* @since 8
*/
onSetData: (pinSubType: AuthSubType, data: Uint8Array) => void;
}
回调:IInputer,regitsterInputer是传入的回调,在需要输口令时被调用。
/**
* Password input box callback.
* @name IInputer
* @syscap SystemCapability.Account.OsAccount
* @systemapi Hide this for inner system use.
* @since 8
*/
interface IInputer {
/**
* Notifies to get data.
* @param pinSubType Indicates the credential subtype for authentication.
* @param callback Indicates the password data callback.
* @systemapi Hide this for inner system use.
* @since 8
*/
onGetData: (pinSubType: AuthSubType, callback: IInputData) => void;
}
回调:IUserAuthCallback,auth,authUser的回调,用来接收auth的结果。
/**
* User authentication callback.
* @name IUserAuthCallback
* @syscap SystemCapability.Account.OsAccount
* @systemapi Hide this for inner system use.
* @since 8
*/
interface IUserAuthCallback {
/**
* The authentication result code is returned through the callback.
* @param result Indicates the authentication result code.
* @param extraInfo Indicates the specific information for different situation.
* If the authentication is passed, the authentication token is returned in extrainfo,
* If the authentication fails, the remaining authentication times are returned in extrainfo,
* If the authentication executor is locked, the freezing time is returned in extrainfo.
* @systemapi Hide this for inner system use.
* @since 8
*/
onResult: (result: number, extraInfo: AuthResult) => void;
/**
* During an authentication, the TipsCode is returned through the callback.
* @param module Indicates the executor type for authentication.
* @param acquire Indicates the tip code for different authentication executor.
* @param extraInfo reserved parameter.
* @systemapi Hide this for inner system use.
* @since 8
*/
onAcquireInfo?: (module: number, acquire: number, extraInfo: any) => void;
}
回调:IIdmCallback,addCredential,updateCredential,delUser,delCred的回调,用来收听onResult是否成功。
/**
* Identity manager callback.
* @name IIdmCallback
* @syscap SystemCapability.Account.OsAccount
* @systemapi Hide this for inner system use.
* @since 8
*/
interface IIdmCallback {
/**
* The authentication result code is returned through the callback.
* @param result Indicates the authentication result code.
* @param extraInfo pass the specific information for different situation.
* @systemapi Hide this for inner system use.
* @since 8
*/
onResult: (result: number, extraInfo: RequestResult) => void;
/**
* During an authentication, the TipsCode is returned through the callback.
* @param module Indicates the executor type for authentication.
* @param acquire Indicates the tip code for different authentication executor.
* @param extraInfo reserved parameter.
* @systemapi Hide this for inner system use.
* @since 8
*/
onAcquireInfo?: (module: number, acquire: number, extraInfo: any) => void;
}
流程:
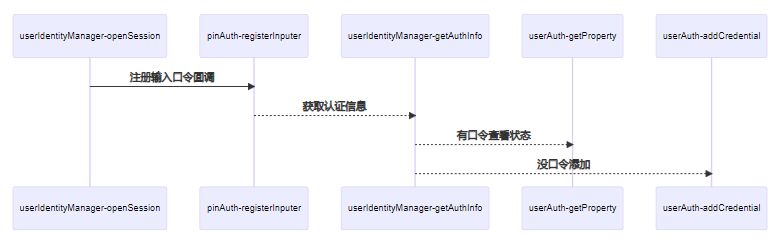
构建对象
//三个对象
this.userIdentityManager = new osAccount.UserIdentityManager();
this.pinAuth = new osAccount.PINAuth();
this.userAuth = new osAccount.UserAuth();
opensession
/**
* Open Session
* A challenge value of 0 indicates that opensession failed
*
* @returns challenge value
*/
openSession(callback: (challenge: string) => void): void {
LogUtil.debug(`${this.TAG}openSession in.`);
try {
this.userIdentityManager.openSession()
.then((data) =>{
callback(this.u8AToStr(data));
LogUtil.info(`${this.TAG} openSession success`);
})
.catch((err) => {
LogUtil.error(`${this.TAG} openSession failed` + JSON.stringify(err));
})
} catch {
LogUtil.error(`${this.TAG}openSession failed`);
callback('0');
}
LogUtil.debug(`${this.TAG}openSession out.`);
}
注册inputer
/**
* Register Inputer
*/
registerInputer(): boolean {
LogUtil.debug(`${this.TAG}registerInputer in.`);
let result = false;
try {
result = this.pinAuth.registerInputer({
onGetData: (authSubType, inputData) => {
let u8aPwd = this.encodeToU8A(this.password);
LogUtil.info(`${this.TAG} before set data, type: ${this.pinSubType}.`);
inputData.onSetData(this.pinSubType, u8aPwd);
}
});
if(!result){
this.unregisterInputer();
result = this.pinAuth.registerInputer({
onGetData: (authSubType, inputData) => {
let u8aPwd = this.encodeToU8A(this.password);
inputData.onSetData(this.pinSubType, u8aPwd);
}
});
}
} catch {
LogUtil.error(`${this.TAG}registerInputer failed`);
}
LogUtil.info(`${this.TAG}registerInputer out.`);
return result;
}
createPassword
/**
* Call api to create password
*/
createPassword() {
PasswordModel.addPinCredential(this.passwordType, this.password, (result) => {
if (result === ResultCode.SUCCESS) {
LogUtil.info(`${this.TAG}create password success`);
this.goBackCorrect();
} else {
LogUtil.info(`${this.TAG}create password failed`);
//TODO show api message to view
this.checkMessage = 'create failed.';
}
});
}
getAuthInfo
/**
* Get AuthInfo
*
* @param authType Credential type.
* @returns Returns all registered credential information of this type for the current user
*/
getPinAuthInfo(callback: (data: Array<{
authType: number;
authSubType: number;
}>) => void): void {
LogUtil.debug(`${this.TAG}getPinAuthInfo in.`);
try {
this.userIdentityManager.getAuthInfo(AuthType.PIN)
.then((data) => {
LogUtil.info(`${this.TAG} get pin auth info data.`);
let arrCredInfo = [];
try {
for(let i = 0; i < data.length; i++) {
let credInfo = {
'authType': data[i].authType,
'authSubType': data[i].authSubType
};
if (credInfo.authType == AuthType.PIN) {
this.pinSubType = credInfo.authSubType;
}
arrCredInfo.push(credInfo);
}
} catch(e) {
LogUtil.info('faceDemo pin.getAuthInfo error = ' + e);
}
callback(arrCredInfo);
LogUtil.info(`${this.TAG} getAuthInfo success.`);
})
.catch((err) => {
LogUtil.error(`${this.TAG} getAuthInfo failed.` + JSON.stringify(err));
})
} catch (e) {
LogUtil.error(`${this.TAG}getPinAuthInfo failed:` + e);
}
LogUtil.debug(`${this.TAG}getPinAuthInfo out.`);
}
autPin
/**
* Auth
*
* @param challenge pass in challenge value. challenge是从openSession的回调得到
* @param password password
* @param onResult Return results through callback.
*/
authPin(challenge: string, password: string, onResult: (result: number, extraInfo: {
token?: string;
remainTimes?: number;
freezingTime?: number;
}) => void): void {
LogUtil.debug(`${this.TAG}authPin in.`);
this.password = password;
try {
LogUtil.info(`${this.TAG} before userAuth auth pin`);
this.userAuth.auth(this.strToU8A(challenge), AuthType.PIN, AuthTrustLevel.ATL4, {
onResult: (result, extraInfo) => {
try{
if (result === ResultCode.SUCCESS) {
LogUtil.debug(`${this.TAG}userAuth.auth onResult: result = success`);
} else {
LogUtil.debug(`${this.TAG}userAuth.auth failed onResult: result = ${result}`);
}
let info = {
'token': this.u8AToStr(extraInfo?.token),
'remainTimes': extraInfo.remainTimes,
'freezingTime': extraInfo.freezingTime
}
onResult(result, info)
}
catch(e) {
LogUtil.debug(`${this.TAG}userAuth.auth onResult error = ${JSON.stringify(e)}`);
}
},
onAcquireInfo: (acquireModule, acquire, extraInfo) => {
try{
LogUtil.debug(this.TAG + 'faceDemo pin.auth onAcquireInfo acquireModule = ' + acquireModule);
LogUtil.debug(this.TAG + 'faceDemo pin.auth onAcquireInfo acquire = ' + acquire);
}
catch(e) {
LogUtil.error(this.TAG + 'faceDemo pin.auth onAcquireInfo error = ' + e);
}
}
})
} catch (e) {
LogUtil.error(`${this.TAG}AuthPin failed:` + e);
}
LogUtil.debug(`${this.TAG}authPin out.`);
}
概述
- 主干代码:1014日下载的。
- hilog -b D:打开debug输出。
- 可能需要的权限:ohos.permission.MANAGE_USER_IDM, ohos.permission.USE_USER_IDM,ohos.permission.MANAGE_LOCAL_ACCOUNTS,ohos.permission.ACCESS_USER_AUTH_INTERNAL,ohos.permission.ACCESS_PIN_AUTH。
- 运行settings,日志分析。
//opensession
11-29 14:56:32.473 2813-2813/com.ohos.mysettings I A00500/[Settings]: Settings PasswordModel#openSession in.
11-29 14:56:32.474 2813-2813/com.ohos.mysettings I A00500/[Settings]: Settings PasswordModel#openSession out.
//registerInputer(不是系统hap,没有selinux权限,没打包设置)
com.ohos.mysettings I A00500/[Settings]: Settings PasswordModel#registerInputer in.
com.ohos.mysettings I C02441/PIN_AUTH_SDK: [RegisterInputer@pinauth_register.cpp:40] start
com.ohos.mysettings I C02441/PIN_AUTH_SDK: [GetProxy@pinauth_register.cpp:70] start
accesstoken_ser I C02f01/AccessTokenManagerStub: [OnRemoteRequest]:OnRemoteRequest called, code: 65296
accesstoken_ser I C02f01/PermissionManager: [VerifyAccessToken]:VerifyAccessToken called, tokenID: 537131032, permissionName: ohos.permission.MANAGE_USER_IDM
accesstoken_ser I C02f01/AccessTokenManagerService: [VerifyAccessToken]:tokenID: 537131032, permissionName: ohos.permission.MANAGE_USER_IDM, res 0
samgr I C01800/SAMGR: SystemAbilityManagerStub::OnReceived, code = 2, callerPid = 2813, flags= 0
accountmgr I C02f01/AccessTokenManagerProxy: [VerifyAccessToken]:result from server data = 0
samgr I C01800/SAMGR: SystemAbilityManagerStub::OnReceived, code = 2, callerPid = 571, flags= 0
samgr E C02f02/Selinux: avc: denied { get } for service=941 pid=2813 scontext=u:r:system_core_hap:s0 tcontext=u:object_r:sa_useriam_pinauth_service:s0 tclass=samgr_class permissive=0
samgr E C01800/SAMGR: CheckSystemAbilityInner selinux permission denied! SA : 941
samgr I C01800/SAMGR: found service : 901.
com.ohos.mysettings E C01510/BinderInvoker: 125: SendRequest: handle=0 result = 1
com.ohos.mysettings E C02441/PIN_AUTH_SDK: [GetProxy@pinauth_register.cpp:81] get distributed gallery manager service fail
com.ohos.mysettings E C02441/PIN_AUTH_SDK: [RegisterInputer@pinauth_register.cpp:47] get proxy failed
com.ohos.mysettings E C01b00/AccountIAM: [RegisterInputer:89]:Failed to register inputer
com.ohos.mysettings E A00500/[Settings]: Settings PasswordModel#registerInputer failed
com.ohos.mysettings I A00500/[Settings]: Settings PasswordModel#registerInputer out.
//registerInputer(是系统hap,有分布式权限)
com.ohos.settings I C02441/PIN_AUTH_SDK: [RegisterInputer@pinauth_register.cpp:40] start
accesstoken_ser I C02f01/PermissionManager: [VerifyAccessToken]:VerifyAccessToken called, tokenID: 537311758, permissionName: ohos.permission.MANAGE_USER_IDM
com.ohos.settings I C02441/PIN_AUTH_SDK: [GetProxy@pinauth_register.cpp:70] start
accesstoken_ser I C02f01/AccessTokenManagerService: [VerifyAccessToken]:tokenID: 537311758, permissionName: ohos.permission.MANAGE_USER_IDM, res 0
samgr I C01800/SAMGR: SystemAbilityManagerStub::OnReceived, code = 2, callerPid = 3279, flags= 0
accountmgr I C02f01/AccessTokenManagerProxy: [VerifyAccessToken]:result from server data = 0
samgr I C01800/SAMGR: SystemAbilityManagerStub::OnReceived, code = 2, callerPid = 571, flags= 0
samgr I C01800/SAMGR: found service : 941.
samgr I C01800/SAMGR: found service : 901.
com.ohos.settings I C02441/PIN_AUTH_SDK: [GetProxy@pinauth_register.cpp:92] succeed to connect distributed gallery manager service
com.ohos.settings I C02441/PIN_AUTH_SDK: [RegisterInputer@pin_auth_proxy.cpp:30] start
com.ohos.settings I C02441/PIN_AUTH_SDK: [SendRequest@pin_auth_proxy.cpp:76] code = 1
accountmgr I C02401/USER_IDM_SDK: [SendRequest@user_idm_proxy.cpp:351] code = 0
pinauth I C02441/PIN_AUTH_SA: [OnRemoteRequest@pin_auth_stub.cpp:28] cmd = 1, flags = 0
pinauth I C02441/PIN_AUTH_SA: [RegisterInputerStub@pin_auth_stub.cpp:47] start
useriam I C02421/USER_AUTH_SA: [OnRemoteRequest@user_idm_stub.cpp:32] cmd = 0, flags= 0
useriam I C02421/USER_AUTH_SA: [OpenSessionStub@user_idm_stub.cpp:66] enter
useriam I C02421/USER_AUTH_SA: [OpenSession@user_idm_service.cpp:61] start
pinauth I C02441/PIN_AUTH_SA: [RegisterInputer@pin_auth_service.cpp:112] start
pinauth I C02441/PIN_AUTH_SA: [CheckPermission@pin_auth_service.cpp:104] start
accesstoken_ser I C02f01/AccessTokenManagerStub: [OnRemoteRequest]:OnRemoteRequest called, code: 65296
accesstoken_ser I C02f01/PermissionManager: [VerifyAccessToken]:VerifyAccessToken called, tokenID: 537311758, permissionName: ohos.permission.MANAGE_USER_IDM
accesstoken_ser I C02f01/AccessTokenManagerService: [VerifyAccessToken]:tokenID: 537311758, permissionName: ohos.permission.MANAGE_USER_IDM, res 0
useriam I C02f01/AccessTokenManagerProxy: [VerifyAccessToken]:result from server data = 0
accesstoken_ser I C02f01/AccessTokenManagerStub: [OnRemoteRequest]:OnRemoteRequest called, code: 65296
samgr I C01800/SAMGR: SystemAbilityManagerStub::OnReceived, code = 12, callerPid = 924, flags= 0
accesstoken_ser I C02f01/PermissionManager: [VerifyAccessToken]:VerifyAccessToken called, tokenID: 671961229, permissionName: ohos.permission.MANAGE_USER_IDM
accesstoken_ser I C02f01/AccessTokenManagerService: [VerifyAccessToken]:tokenID: 671961229, permissionName: ohos.permission.MANAGE_USER_IDM, res 0
useriam I C02f01/AccessTokenManagerProxy: [VerifyAccessToken]:result from server data = 0
samgr I C01800/SAMGR: found service : 3503.
accesstoken_ser I C02f01/AccessTokenManagerStub: [OnRemoteRequest]:OnRemoteRequest called, code: 65316
accesstoken_ser I C02f01/AccessTokenManagerService: [GetTokenType]:called, tokenID: 0x280ff12c
accesstoken_ser I C02f01/AccessTokenManagerService: [GetNativeTokenInfo]:called, tokenID: 0x280d508d
useriam I C02f01/AccessTokenManagerProxy: [GetNativeTokenInfo]:result from server data = 0
samgr I C01800/SAMGR: SystemAbilityManagerStub::OnReceived, code = 12, callerPid = 483, flags= 0
pinauth I C02f01/AccessTokenManagerProxy: [VerifyAccessToken]:result from server data = 0
pinauth I C02441/PIN_AUTH_SA: [RegisterInputer@pin_auth_manager.cpp:29] start, tokenId = 537311758
pinauth I C02441/PIN_AUTH_SA: [RegisterInputer@pin_auth_manager.cpp:47] end
com.ohos.settings I A00500/[Settings]: Settings PasswordModel#registerInputer out.
//getAuthInfo (找不到)
com.ohos.mysettings I A00500/[Settings]: Settings PasswordModel# get pin auth info data.
com.ohos.mysettings I A00500/[Settings]: Settings PasswordSettingController#getListData(false,) in
com.ohos.mysettings I A00500/[Settings]: Settings PasswordSettingController#getListData(false,) out => undefined
com.ohos.mysettings I A00500/[Settings]: Settings PasswordModel# getAuthInfo success.
//getAuthInfo(找到)
com.ohos.settings I A00500/[Settings]: Settings PasswordModel# get pin auth info data.
com.ohos.settings I A00500/[Settings]: Settings h#getListData(true,) in
com.ohos.settings I A00500/[Settings]: Settings h#getListData(true,) out => undefined
com.ohos.settings I A00500/[Settings]: Settings PasswordModel# getAuthInfo success.
//addCredential(添加口令失败,因为不是系统hap所以没有成功注册inputer)
com.ohos.mysettings I A00500/[Settings]: Settings PasswordInputController passwordOnChange in.
com.ohos.mysettings I A00500/[Settings]: Settings PasswordInputController checkInputDigits in.
com.ohos.mysettings I A00500/[Settings]: Settings Password Checker isNumber6 in.
com.ohos.mysettings I A00500/[Settings]: Settings PasswordModel#addPinCredential in.
com.ohos.mysettings I A00500/[Settings]: Settings PasswordModel#addPinCredential out.
com.ohos.mysettings I A00500/[Settings]: Settings PasswordInputController passwordOnChange out.
useriam I C02f01/AccessTokenManagerProxy: [GetNativeTokenInfo]:result from server data = 0
useriam I C02421/USER_AUTH_SA: [Start@base_context.cpp:56] Context(type:Enroll, contextId:0xXXXX7702) start
useriam I C02421/USER_AUTH_SA: [OnStart@enroll_context.cpp:43] Context(type:Enroll, contextId:0xXXXX7702) start
samgr I C01800/SAMGR: SystemAbilityManagerStub::OnReceived, code = 12, callerPid = 483, flags= 0
samgr I C01800/SAMGR: found service : 5100.
hdf_devmgr I C02500/devsvc_manager_stub: service user_auth_interface_service found
user_auth_host 17 user_auth_host I C02421/USER_AUTH_HDI: [BeginEnrollment@user_auth_interface_service.cpp:374] start
user_auth_host 17 user_auth_host I C02421/USER_AUTH_HDI: [CopyScheduleInfo@user_auth_interface_service.cpp:69] start
useriam I C02421/USER_AUTH_SA: [Build@schedule_node_builder.cpp:114] scheduleNode builder start to build
useriam I C02421/USER_AUTH_SA: [Schedule@finite_state_machine_impl.cpp:51] fsm schedule new schedule event input:0
useriam I C02421/USER_AUTH_SA: [OnStart@enroll_context.cpp:51] Context(type:Enroll, contextId:0xXXXX7702) success
useriam I C02421/USER_AUTH_SA: [operator()@user_idm_stub.cpp:158] leave
useriam I C02421/USER_AUTH_SA: [BeginExecute@resource_node_impl.cpp:138] start
useriam I C02421/USER_AUTH_SA: [SendRequest@executor_callback_proxy.cpp:195] code = 2
pinauth I C02421/USER_AUTH_EXECUTOR: [OnBeginExecuteInner@framework_executor_callback.cpp:64] ExecutorCallback(Id:1) start process cmd 0
pinauth I C02421/USER_AUTH_EXECUTOR: [StartProcess@async_command_base.cpp:56] Command(type:ENROLL, id:3, scheduleId:0xXXXX246e) start process
pinauth I C02421/USER_AUTH_EXECUTOR: [AddCommand@executor.cpp:105] Executor(Id:0x00010001) start
pinauth I C02421/USER_AUTH_EXECUTOR: [SendRequest@enroll_command.cpp:42] Command(type:ENROLL, id:3, scheduleId:0xXXXX246e) send request start
pin_auth_host 16 pin_auth_host I C02441/PIN_AUTH_IMPL: [Enroll@executor_impl.cpp:123] start
pin_auth_host 16 pin_auth_host I C02441/PIN_AUTH_IMPL: [NewSalt@executor_impl.cpp:290] start
pin_auth_host 16 pin_auth_host I C02441/PIN_AUTH_IMPL: [NewSalt@executor_impl.cpp:315] EVP_sha256 success
pin_auth_host 16 pin_auth_host I C02441/PIN_AUTH_IMPL: [NewSalt@executor_impl.cpp:326] result size is : [32]
pin_auth_host 16 pin_auth_host I C02441/PIN_AUTH_IMPL: [AddScheduleInfo@executor_impl.cpp:333] start
pinauth I C02441/PIN_AUTH_SA: [OnGetData@pin_auth_executor_callback_hdi.cpp:48] Start tokenId_ is 537131032
pinauth I C02441/PIN_AUTH_SA: [getInputerLock@pin_auth_manager.cpp:65] start
pinauth E C02441/PIN_AUTH_SA: [getInputerLock@pin_auth_manager.cpp:71] pinAuthInputer is not found
pinauth E C02441/PIN_AUTH_SA: [OnGetData@pin_auth_executor_callback_hdi.cpp:51] inputer is nullptr
pinauth E C02500/executor_callback_stub: ExecutorCallbackStubOnGetData failed, error code is <private>
pin_auth_host 16 pin_auth_host E C01510/BinderInvoker: 125: SendRequest: handle=3 result = -1
pin_auth_host 16 pin_auth_host E C02500/executor_callback_proxy: OnGetData failed, error code is -1
pin_auth_host 16 pin_auth_host E C02441/PIN_AUTH_IMPL: [Enroll@executor_impl.cpp:143] Enroll Pin failed, fail code : -1
pin_auth_host 16 pin_auth_host I C02441/PIN_AUTH_IMPL: [DeleteScheduleId@executor_impl.cpp:369] start
pin_auth_host 16 pin_auth_host I C02441/PIN_AUTH_IMPL: [DeleteScheduleId@executor_impl.cpp:372] Delete scheduleId succ
pin_auth_host 16 pin_auth_host E C02500/executor_stub: ExecutorStubEnroll failed, error code is <private>
com.ohos.mysettings I C01c00/ImsaKit: line: 483, function: OnConfigurationChange,InputMethodController::OnConfigurationChange
com.ohos.mysettings W C03900/Ace: [render_text_field.cpp(UpdateAccessibilityAttr)-(0)] RenderTextField accessibilityNode is null.
pinauth E C01510/BinderInvoker: 125: SendRequest: handle=2 result = -1
pinauth E C02500/executor_proxy: Enroll failed, error code is -1
pinauth E C02441/PIN_AUTH_SA: [ConvertResultCode@pin_auth_executor_hdi.cpp:317] covert hdi result code -1 to framework result code 1
pinauth E C02441/PIN_AUTH_SA: [Enroll@pin_auth_executor_hdi.cpp:131] Enroll fail ret=1
pinauth I C02421/USER_AUTH_EXECUTOR: [SendRequest@enroll_command.cpp:53] Command(type:ENROLL, id:3, scheduleId:0xXXXX246e) enroll result 1
pinauth E C02421/USER_AUTH_EXECUTOR: [StartProcess@async_command_base.cpp:65] Command(type:ENROLL, id:3, scheduleId:0xXXXX246e) send request failed
pinauth I C02421/USER_AUTH_EXECUTOR: [EndProcess@async_command_base.cpp:112] Command(type:ENROLL, id:3, scheduleId:0xXXXX246e) end process
pinauth I C02421/USER_AUTH_EXECUTOR: [RemoveCommand@executor.cpp:113] Executor(Id:0x00010001) start
pinauth I C02421/USER_AUTH_EXECUTOR: [OnBeginExecuteInner@framework_executor_callback.cpp:80] command id = 0 ret = 1
useriam E C02421/USER_AUTH_SA: [ProcessBeginVerifier@schedule_node_impl.cpp:281] start verify failed
useriam I C02421/USER_AUTH_SA: [ScheduleInner@finite_state_machine_impl.cpp:84] fsm schedule schedule [state:0] + [event:0] -> [nextState:1]
useriam I C02421/USER_AUTH_SA: [OnResult@enroll_context.cpp:57] Context(type:Enroll, contextId:0xXXXX7702) receive result code 7
useriam E C02421/USER_AUTH_SA: [UpdateScheduleResult@enroll_context.cpp:88] (scheduleResultAttr != nullptr) check fail, return
useriam E C02421/USER_AUTH_SA: [OnResult@enroll_context.cpp:62] Context(type:Enroll, contextId:0xXXXX7702) UpdateScheduleResult fail
useriam I C02421/USER_AUTH_SA: [OnResult@user_idm_callback_proxy.cpp:29] start
useriam I C02421/USER_AUTH_SA: [SendRequest@user_idm_callback_proxy.cpp:87] start
accountmgr E C01b00/AccountMgrService: [OnResult:138]:failed to add credential
com.ohos.mysettings I C03900/NAPI: [native_api.cpp(napi_call_function)] engine: 00F1D680, nativeRecv: CD18BAE0, nativeFunc: CD18BC18, nativeArgv: FF95C088
com.ohos.mysettings I A00500/[Settings]: Settings PasswordModel# Add pin credential, result: 7
com.ohos.mysettings I A00500/[Settings]: Settings PasswordInputController create password failed
//addCredential(添加口令成功)
com.ohos.settings I A00500/[Settings]: Settings PasswordInputController passwordOnChange in.
com.ohos.settings I A00500/[Settings]: Settings PasswordInputController checkInputDigits in.
com.ohos.settings I A00500/[Settings]: Settings Password Checker isNumber6 in.
com.ohos.settings I A00500/[Settings]: Settings PasswordModel#addPinCredential in.
com.ohos.settings I A00500/[Settings]: Settings PasswordModel#addPinCredential out.
com.ohos.settings I A00500/[Settings]: Settings PasswordInputController passwordOnChange out.
……进入服务层
com.ohos.settings I C02441/PIN_AUTH_SDK: [OnRemoteRequest@inputer_get_data_stub.cpp:29] cmd = 1, flags = 0
com.ohos.settings I C02441/PIN_AUTH_SDK: [OnGetData@inputer_get_data_service.cpp:34] start
……进入app层回调
com.ohos.settings D A00500/[Settings]: Settings PasswordModel#encodeToU8A in.
com.ohos.settings D A00500/[Settings]: Settings PasswordModel#encodeToU8A out.
com.ohos.settings I A00500/[Settings]: Settings PasswordModel# before set data, type: 10000.
……进入服务层
com.ohos.settings I C02441/PIN_AUTH_SDK: [OnSetData@inputer_data_impl.cpp:37] start and data size is 6
com.ohos.settings I C02441/PIN_AUTH_SDK: [GetScrypt@scrypt.cpp:36] start
com.ohos.settings I C02441/PIN_AUTH_SDK: [OnSetData@inputer_set_data_proxy.cpp:27] start
com.ohos.settings I C02441/PIN_AUTH_SDK: [SendRequest@inputer_set_data_proxy.cpp:51] code = 1
com.ohos.settings I C02441/PIN_AUTH_SDK: [OnSetData@inputer_set_data_proxy.cpp:45] result = 0
com.ohos.settings I C02441/PIN_AUTH_SDK: [OnRemoteRequest@inputer_get_data_stub.cpp:29] cmd = 1, flags = 0
com.ohos.settings I C02441/PIN_AUTH_SDK: [OnGetData@inputer_get_data_service.cpp:34] star
com.ohos.settings I C02441/PIN_AUTH_SDK: [OnSetData@inputer_data_impl.cpp:37] start and data size is 6
com.ohos.settings I C02441/PIN_AUTH_SDK: [GetScrypt@scrypt.cpp:36] start
com.ohos.settings I C02441/PIN_AUTH_SDK: [OnSetData@inputer_set_data_proxy.cpp:27] start
com.ohos.settings I C02441/PIN_AUTH_SDK: [SendRequest@inputer_set_data_proxy.cpp:51] code = 1
com.ohos.settings I C02441/PIN_AUTH_SDK: [OnSetData@inputer_set_data_proxy.cpp:45] result = 0
com.ohos.settings D C02421/USER_AUTH_SA: [Impl@attributes.cpp:157] emplace pair success, type is 100025
com.ohos.settings I A00500/[Settings]: Settings PasswordModel# Add pin credential, result: 0
com.ohos.settings I A00500/[Settings]: Settings PasswordInputController create password success
小结
- 用户鉴权(包括屏保)是以accountmgr服务为入口为应用层提供功能,以useridm为实现,完成具体的口令管理和人脸管理(人脸管理目前还有欠缺,现在设置里的人脸认证需要先设置口令为123456,然后才开始人脸认证,但是经使用人脸认证时候虽然摄像头是好的但是没有图像,可能是应用的Bug吧)。
- 用户鉴权是系统级服务,要求ohos.permission.MANAGE_USER_IDM, ohos.permission.USE_USER_IDM,ohos.permission.MANAGE_LOCAL_ACCOUNTS,ohos.permission.ACCESS_USER_AUTH_INTERNAL,ohos.permission.ACCESS_PIN_AUTH权限和selinux权限(富设备支持)。











































