On March 24th, it was revealed that a Microsoft account had been stolen by the hacker group Lapsus$. The attackers gained limited access and claimed to have mastered part of Microsoft's source code.
Of the intrusion, Microsoft said, "Our cybersecurity response teams quickly engaged to remediate the compromised account and prevent further activity."
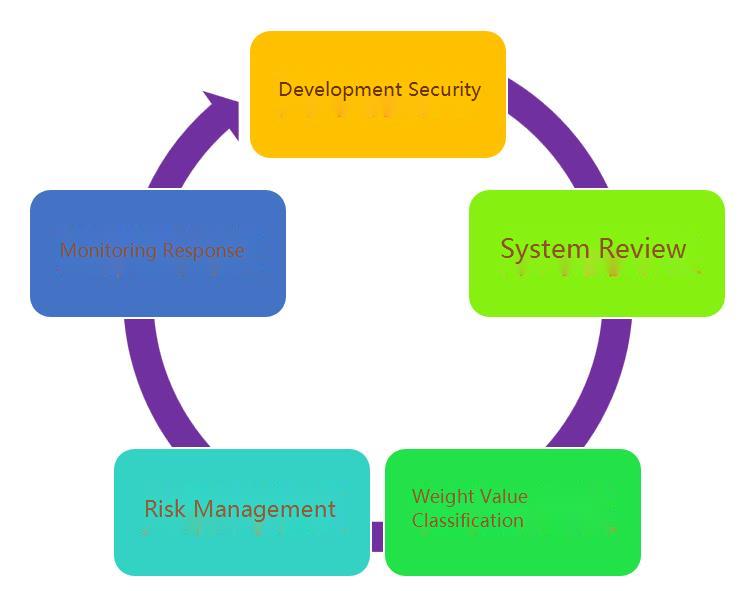
While it was not the first time that Lapsus$ breached a tech giant, after hearing of a series of incidents, risk control departments have already started establishing their system security checks and rectification plans. However, it is often said that "more preparation may quicken the pace of work." Instead of blindly acting in the existing production environment, rethinking the system development and operation could also be good. To identify security risks and prevent them beforehand, we will discuss the security control experience in this article from system development security, system review, weight value classification, risk management, and monitoring response.
1. Development Security
DevSecOps evolves from agile development and aims to left-shift security as far as possible to the initial stage of each development sub-cycle, so it could help developers know the potential threats and vulnerabilities in code earlier. Four practical patterns can be used for this purpose.
Proactive: Segmenting dependencies between applications to isolate components and limit vulnerabilities and threats to one piece, thus ensuring the continued operation of other components. The typical scenario for this pattern is micro-service applications.
One-vote negation: The code logic and user scenarios are designed to interrupt all processes in the event of malicious behavior. For instance, if a user attempts to perform a cross-site scripting attack while visiting a website, any action and its session should be blocked outright.
Industry practice: In teams that lack security experts, standard threat models and control schemas can identify potential risks that application components may face in advance and select the best protection measures.
Multiple Input: Using automated monitoring tools and many input parameters to integrate risk assessment of the operating environment and use cases into the entire software lifecycle.
In addition, we need to implement the following in software development:
Set different user function groups for various application services.
Avoid leaking any password, passphrase, certificate, or private key during the transmission of application data by encryption and other means.
Unify the login methods of multiple applications as Multi-Factor Authentication (MFA) + Single Sign-On (SSO) to achieve automatic matching of user account privileges.
Use proven products to manage keys and promptly discover expired or canceled certificates.
Quickly check code to find invalid or outdated dependencies, codebases, potential memory leaks, endless loops, and code vulnerabilities.
2. System Review
Besides providing software services, we cannot do without the underlying architecture. An enterprise's IT architecture and platforms will present an intricate and complex structural state as an enterprise grows. Therefore, we need to sort out the environment where the daily IT services are located and the resources used in a server room, equipment, lines, applications, business, and users.
Before taking inventory and collecting specific information, we need to develop the classification and definition of the entries in advance to ensure that the generated list is uniform and standardized. Based on the characteristics and status of the data, we must identify the physical hardware devices that store static data, the software applications that process real-time data, the networks that carry dynamic data, the databases that contain structured data, the cloud platforms that store unstructured data, the file servers and user terminals that continuously read and write data.
We can use "automatic tool discovery + manual input + secondary review" to ensure accuracy in building a comprehensive, complete, and intuitive system baseline. This will be our reference standard for later rectification.
3. Weight Value Classification
As a result, we can take a step back from the classical theory of information security and evaluate in-depth the actual impact that various components and data may have on the enterprise when their confidentiality (C), integrity (I) and availability (A) are compromised, and assign the respective values to the three factors accordingly. With the values, we can then calculate the weight value (V) of the asset based on the following formula:
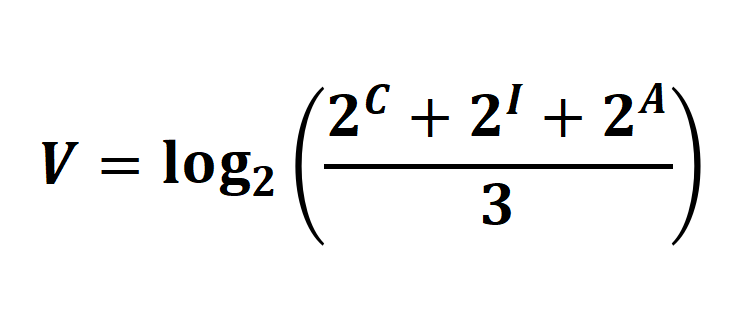
It is worth noting that we can not only assign values to hardware and software assets but also data so that we can progress to clarify which data needs to be encrypted, erased, used internally with restrictions, and available directly to the public. The actual numbers are often difficult to define, so we can use a range of values to classify them into levels like "Top Secret, Confidential, Private, Sensitive, Public, etc."
Sometimes, where confidentiality is stringent, we need to distinguish different levels of security for fields in specific structured data tables, key/value (K/V) in unstructured data fields, and meta information in the corresponding attribute labels of a vector. Besides the logical classification of data, we also need to identify the confidentiality level of equipment components as physical labels.
4. Risk Management: Operational Risk Identification and Response
Some developers may wonder what factors will affect C, I, and A? We need to identify the external threats, internal vulnerabilities, and combined risks to components and data in the operational environment. Generally, we can take the following four steps to identify risks:
- Collect and identify: Based on records and industry experience, recruit people in different roles to do brainstorming, questionnaire interviews, matrix charts, etc., to identify hidden risks in the existing environment. For example:
- Technical level: software and hardware failures and damages, application system vulnerabilities, malware deadlocks, denial-of-service attacks on the network, etc.
- infrastructure level: power outages, water leakages, operator network interruptions, etc.
- Human level: access to websites with trojans, various operational mistakes, file data misalignment or tampering, etc.
- Management level: lack of awareness of cybersecurity, mistakes in handling methods, imperfect rules and regulations, etc.
- Analysis and evaluation: Use different methods, such as qualitative/quantitative, to evaluate and rank the identified risks in terms of degree, scope, and likelihood and make a risk ranking matrix accordingly. We can refer to the following criteria for risk quantification:
- Extent of damage—minor, average, major, severe, extra serious, etc.
- Scope of impact – enterprise-wide, external customers, multiple sub-sites, specific departments, systems, individual services, etc.
- Possibility of occurrence - consider the physical and logical areas, fault tolerance, level of protection, and compliance.
- Response and disposal:We need to choose among the standard risk mitigation, transfer, avoidance, and acceptance methods and respond according to our risk policy (i.e., risk acceptance). Among them, we need to pay attention to the following two aspects:
- We should pay attention to the consistency of disposal measures to avoid some local "short slab" in the barrel effect.
- We can flexibly adjust the control strategies based on distinguishing between the owner of the risk and the control implementer and taking the time, budget, and other costs into account.
5. Monitoring Response: Minimizing Security Incidents
Currently, many companies are establishing proactive monitoring and response mechanisms to minimize the negative impact of security incidents on business operations. The operation team can set up reliability engineers (SREs) to monitor critical equipment status in real-time during routine preventive inspections and find and locate component failures based on documentation on time. They can also review and track performance metrics remotely and by deploying open-source logging and event monitoring tools such as Zabbix.
Let's take a cloud-based business environment as an example to discuss how to manage and control the entire lifecycle of event monitoring and response.
Detection and identification stage: Capture and filter system events from each VM, as well as network-based abnormal traffic information, and then continuously write the filtered log information to the HBase database, providing an essential basis for various correlation analyses and necessary forensics later.
Investigation and analysis stage: Using tools to group the types of events according to feature codes and count the frequency of events. Meanwhile, we can introduce the Application Performance Analysis (APM) module to pinpoint the URL of the application service where the access speed drops or where the user submits a SQL statement with a delay to locate the root faster.
Mitigating and remediation stage: The problematic VM image can be isolated from other systems and services by suspending it, which will not destroy the evidence on that VM but will stop the situation from getting worse.
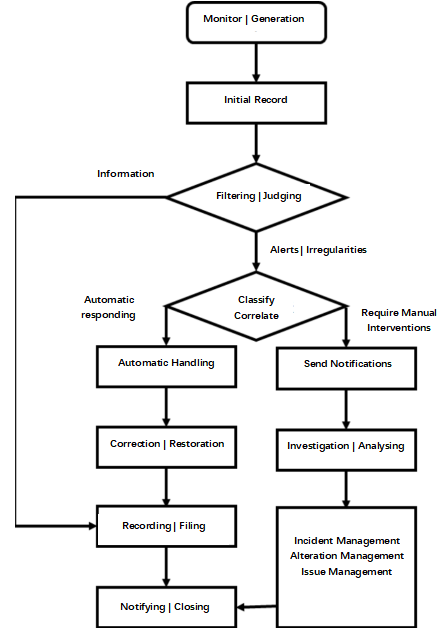
We can refer to the following process to effectively respond to emergencies:
Conclusion
In this article, we have discussed five keys in system security practices: development security, system review, weight value classification, risk management, and monitoring response.
Faced with the complex internal and external network environment, we should adhere to the simple concept of "no harming others, while guarding against others" and proactively continue to review and improve our IT system. As long as each enterprise can promptly make up for the security shortcomings, the overall cybersecurity situation in the IT industry will be significantly improved.
About the Author
Julian Chen has over ten years of IT project implementation experience and excels at resources and risk control. Chen loves to share network and information security knowledge and innovative technology tips by writing blogs. Chen also teaches information security both online and offline.