ScanT3r是一款功能强大的Web安全扫描工具,该工具支持检测下列漏洞:
- 远程代码执行漏洞-Linux;
- 反射型XSS漏洞;
- 模板注入漏洞:Jinja2、ERB、Java、Twig、Freemarker;
- SQL注入漏洞;
系统支持:
- Linux
- Android
- Windows
工具安装
注意:ScanT3r仅支持Python > 3.6环境。
Linux安装
首先,打开命令行终端窗口。
输入并运行下列命令:
- $ git clone https://github.com/knassar702/scant3r
- $ cd scant3r
- $ python3 -m pip install -r requirements.txt
- $ chmod +x scant3r
Android安装
首先,下载Termux App:https://play.google.com/store/apps/details?id=com.termux&hl=en
打开Termux应用程序,然后输入并运行下列命令:
- $ pkg install python -y
- $ pkg install git -y
- $ git clone https://github.com/knassar702/scant3r
- $ cd scant3r
- $ python3 -m pip install -r requirements.txt
- $ chmod +x scant3r
Windows安装
首先,下载并安装 Python3 环境,然后打开命令行终端窗口,输入并运行下列命令:
- $ python3 -m pip install -r requirements.txt
工具使用
- Options:
- -h, --help | Show help message and exit
- --version | Show program's version number and exit
- -u URL, --url=URL | Target URL (e.g."http://www.target.com/vuln.php?id=1")
- --data=DATA | Data string to be sent through POST (e.g. "id=1")
- --list=FILE | Get All Urls from List
- --threads | Max number of concurrent HTTP(s) requests (default 10)
- --timeout | Seconds to wait before timeout connection
- --proxy | Start The Connection with http(s) proxy
- --cookies | HTTP Cookie header value (e.g. "PHPSESSID=a8d127e..")
- --encode | How Many encode the payload (default 1)
- --allow-redirect | Allow the main redirect
- --user-agent | add custom user-agent
- --scan-headers | Try to inject payloads in headers not parameters (user-agent,referrer)
- --skip-headers | Skip The Headers scanning processe
- --sleep | Sent one request after some Seconds
- --module | add custom module (e.g. "google.py")
- --debug | Debugging Mood
工具使用样例
POST方法:
- $ python3 scant3r -u 'http://localhost/dvwa/vulnerabilities/exec/' --data='ip=localhost&Submit=Submit'
添加Cookie:
$ python3 scant3r -u 'http://localhost/?l=2' --cookies='user=admin&id=1'
添加超时:
$ python3 scant3r -u 'http://localhost/?l=13' --timeout=1
允许重定向(302、301):
$ python3 scant3r -u 'http://localhost/?l=13' --allow-redirect
休眠时间:
$ python3 scant3r -u 'http://localhost/?l=13' --sleep=2
开启调试模式:
$ python3 scant3r -u 'http://localhost/?l=13' --debug
扫描所有Header:
$ python3 scant3r -u 'http://localhost/?l=13' --scan-headers
跳过Header:
$ python3 scant3r -u 'http://localhost/?l=13' --skip-headers
添加自定义User-Agent:
$ python3 scant3r -u 'http://localhost/?l=13' --user-agent='CustomUseragent(v2)'
添加编码方案:
$ python3 scant3r -u 'http://localhost/?l=13' --encode=2
添加代理:
$ python3 scant3r -u 'http://localhost/?l=13' --proxy='http://localhost:8080'
运行你自己的模块:
$ python3 scant3r -u 'http://localhost/?l=13' --module=dumper.py
添加URL列表:
$ python3 scant3r --list urls.txt --threads=40
测试样例
- $ ./scant3r -u 'http://test.vulnweb.com/search.php?test=query' --data='searchFor=scant3r&goButton=go'
- $ ./scant3r -u 'http://test.vulnweb.com/artists.php?artist=1'
- $ ./scant3r -u 'https://menacoderrr.pythonanywhere.com/'
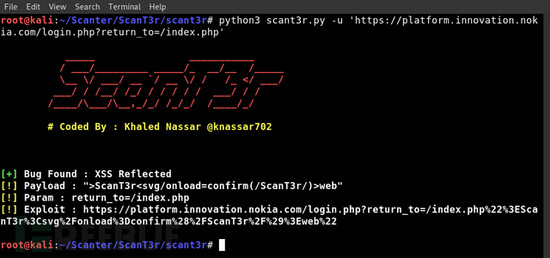
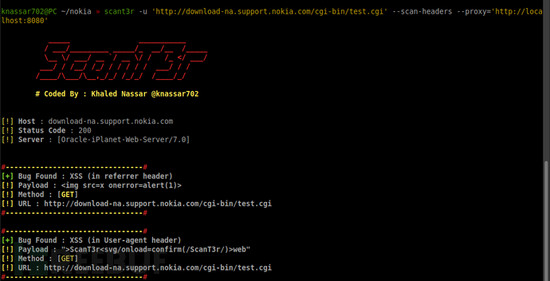
工具运行截图
诺基亚官网:
项目地址
ScanT3r:https://github.com/knassar702/scant3r