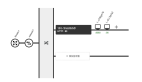
在前面,我们讲解过了关于采用积极模式并PSK的IPsec VPN配置和基于PSK的IPsec VPN配置的相关内容,那么下面我们主要分析一下GRE和IPsec的相关内容。GRE隧道本身不带安全特性,可以通过结合基于PSK的IPsec来实现安全功能.拓扑如下:
1.R1基本配置:
R1(config)#interface loopback0
R1(config-if)#ip address 10.1.1.1 255.255.255.0
R1(config-if)#no shutdown
R1(config-if)#interface serial0/0
R1(config-if)#ip address 192.168.1.1 255.255.255.252
R1(config-if)#clock rate 56000
R1(config-if)#no shutdown
R1(config)#interface tunnel 0
R1(config-if)#ip unnumbered serial0/0
R1(config-if)#tunnel source serial0/0
R1(config-if)#tunnel destination 192.168.1.1
R1(config-if)#tunnel mode gre ip /---可以不打,默认即为GRE---/
R1(config-if)#no shutdown
R1(config-if)#exit
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
2.定义感兴趣流量与路由协议:
R1(config)#access-list 100 permit gre host 192.168.1.1 host 192.168.1.2
R1(config)#ip route 0.0.0.0 0.0.0.0 serial0/0
R1(config)#ip route 10.2.2.0 255.255.255.0 serial0/0
- 1.
- 2.
- 3.
- 4.
3.全局启用ISAKMP并定义对等体及其PSK(预共享密钥):
R1(config)#crypto isakmp enable
R1(config)#crypto isakmp key 91lab address 192.168.1.2
- 1.
- 2.
- 3.
4.定义IKE策略:
R1(config)#crypto isakmp policy 10
R1(config-isakmp)#encryption aes 128 /---默认是DES加密---/
R1(config-isakmp)#hash sha /---默认是SHA-1---/
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group 2 /---默认是768位的DH1---/
R1(config-isakmp)#lifetime 3600 /---默认是86400秒---/
R1(config-isakmp)#exit
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
5.定义IPSec转换集(transform set):
R1(config)#crypto ipsec transform-set tt esp-aes 128 esp-sha-hmac
R1(cfg-crypto-trans)#mode tunnel
R1(cfg-crypto-trans)#exit
- 1.
- 2.
- 3.
- 4.
6.定义crypto map并应用在接口上:
R1(config)#crypto map cisco 10 ipsec-isakmp
R1(config-crypto-map)#match address 100
R1(config-crypto-map)#set peer 192.168.1.2 /---定义要应用crypto map的对等体地址---/
R1(config-crypto-map)#set transform-set tt /---定义crypto map要应用的IPsec转换集---/
R1(config-crypto-map)#exit
R1(config)#interface serial0/0
R1(config-if)#crypto map cisco
*Mar 1 00:08:31.131: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
R1(config-if)#end
R1#
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
R1配置完成.
同理,R2相关配置如下:
!
!
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
crypto isakmp key 91lab address 192.168.1.1
!
!
crypto ipsec transform-set tt esp-aes esp-sha-hmac
!
crypto map cisco 10 ipsec-isakmp
set peer 192.168.1.1
set transform-set tt
match address 100
!
!
!
interface Tunnel0
ip unnumbered Serial0/0
tunnel source Serial0/0
tunnel destination 192.168.1.1
!
interface Loopback0
ip address 10.2.2.1 255.255.255.0
!
interface Serial0/0
ip address 192.168.1.2 255.255.255.252
crypto map cisco
!
ip route 0.0.0.0 0.0.0.0 Serial0/0
!
access-list 100 permit gre host 10.2.2.1 host 10.1.1.1
!
- 1.
- 2.
- 3.
- 4.
- 5.
- 6.
- 7.
- 8.
- 9.
- 10.
- 11.
- 12.
- 13.
- 14.
- 15.
- 16.
- 17.
- 18.
- 19.
- 20.
- 21.
- 22.
- 23.
- 24.
- 25.
- 26.
- 27.
- 28.
- 29.
- 30.
- 31.
- 32.
- 33.
- 34.